Trusted by 150+ teams
Explore the Hunto AI Platform
Secure every layer of your digital presence with unified visibility, rapid response, and intelligent automation.
Why choose Hunto AI?
Discover how Hunto’s integrated platform helps security, compliance, and IT teams sleep better at night.
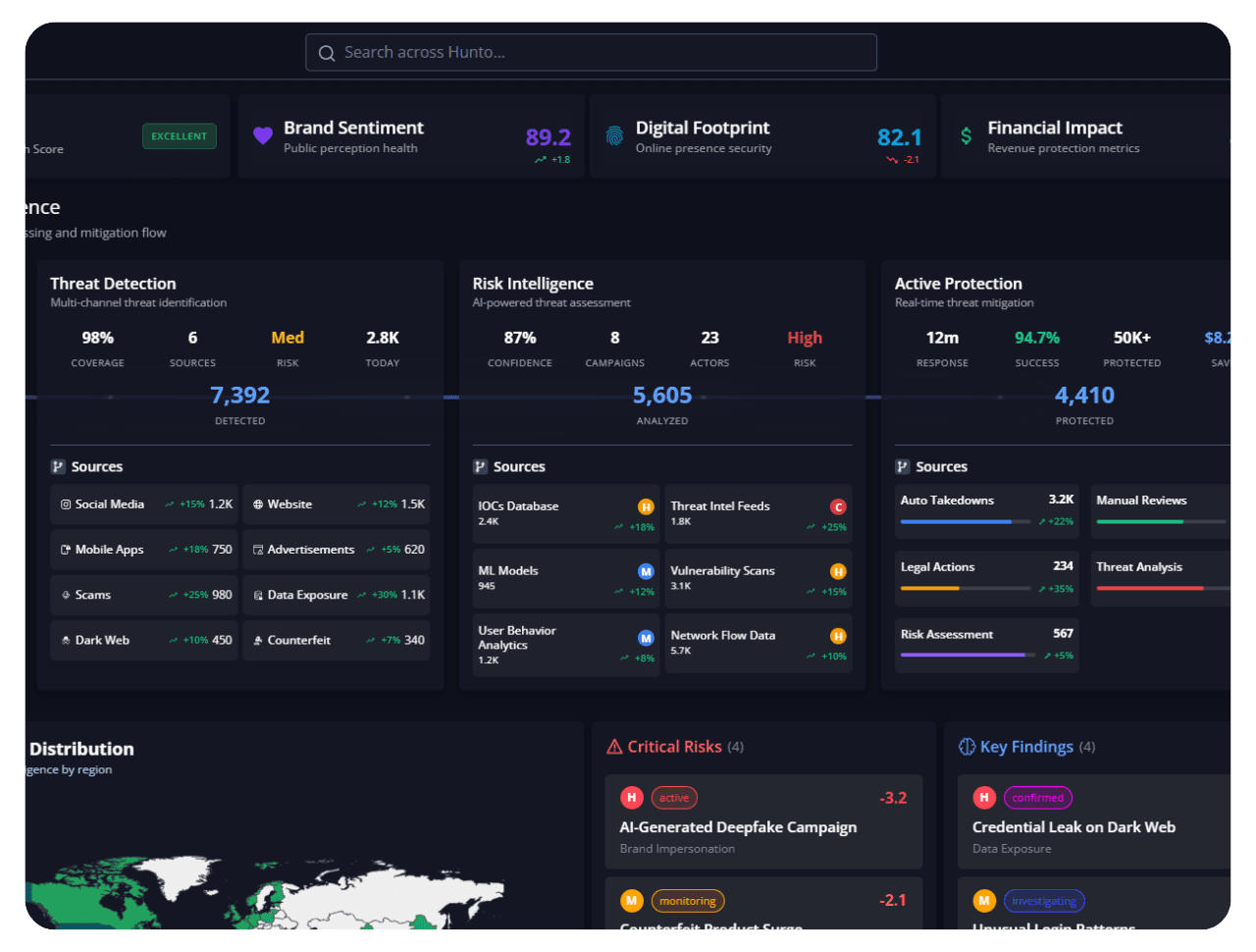
Real-Time Risk Visibility
Continuously monitor your external attack surface and uncover threats before attackers do from rogue assets to misconfigured domains.
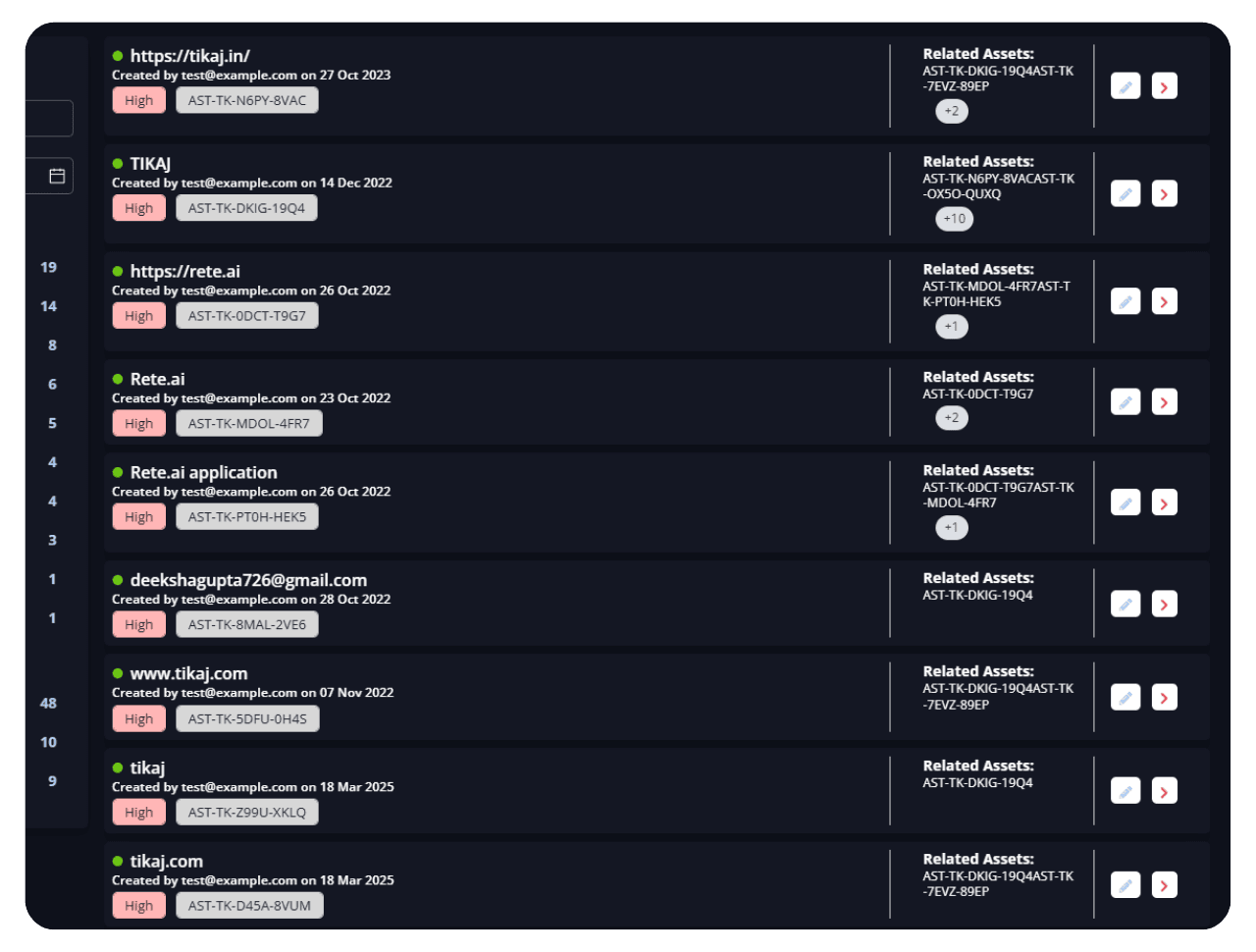
Unified Brand Defence
Stop impersonations, phishing scams, fake apps, and rogue social profiles from eroding brand trust all from a single command center.
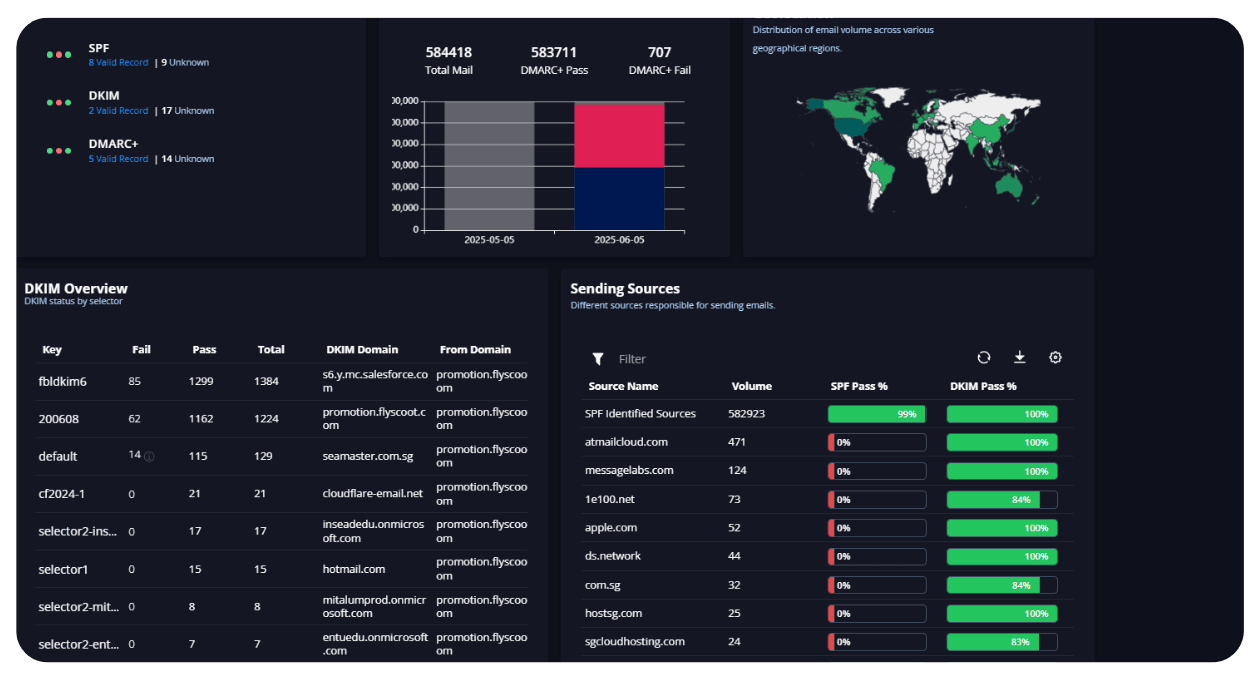
Email-Secured Communication
Achieve and maintain full DMARC, SPF, and DKIM alignment. Prevent spoofed emails, phishing, and CEO fraud from reaching inboxes.
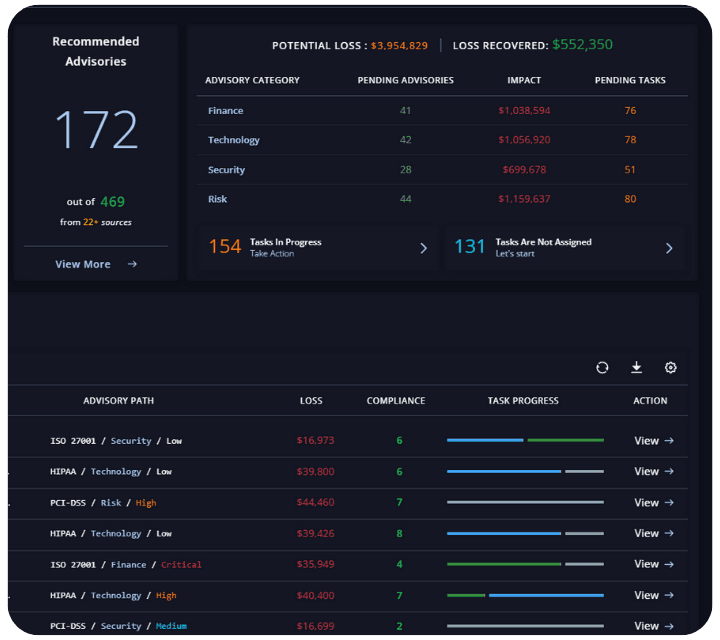
Compliance, Simplified
Cut through regulatory chaos. From RBI/SEBI compliance to internal audit readiness track, manage, and resolve advisories with ease.
Contact Us
Take the Next Step in Strengthening Your Cybersecurity
Our team of experts will walk you through the platform’s features and how it can be customized to fit your organization’s specific needs.
- Free 14-day trial
- Threat Detection
- DMARC Compliance
- Incident Takedown
- Brand Defense
