Agentic, Effortless
Threat Management
100% Autonomous AI Agents that continuously discover, monitor, and mitigate external threats — no manual intervention required.
No credit card required • Setup in 5 minutes • Cancel anytime
Trusted by Industry Leaders
150+ Enterprises Trust Hunto AI
From banking to fintech, e-commerce to healthcare — organizations worldwide rely on our autonomous threat protection.














Continuous Threat Exposure Management
Hunto AI works 24/7 without sleep, breaks, or bias. It autonomously discovers, investigates, and mitigates threats while you focus on strategy.
Continuous Threat Hunting
Autonomous agents actively scan the open, deep, and dark web for mentions of your brand, employees, and assets 24/7.
Early Signal Detection
Identify leaked credentials and exposed data before they turn into active attacks.
Threat Signal Discovery
Surface early indicators of compromise across underground and public sources.
Automated Takedowns
detect and initiate takedowns of phishing sites and impersonations in minutes, not days.
Audit-Ready Compliance
Automatic evidence collection mapped to ISO 27001, SOC 2, and GDPR controls.
Unifies Your Stack
Seamless two-way integration with your existing security tools, SIEMs, and communication platforms.
Deploy in Minutes,
Not Months.
Connect your existing tools and assets with a few clicks. Hunto AI automatically maps your attack surface and starts monitoring immediately. No agents to install, no complex configuration.
- Auto-discovery of assets and domains
- One-click integrations with Slack, Jira, and SIEMs
- Instant historical scan and threat baseline
Deep Dive Analysis
Beyond Surface Level.
Our agents don't just alert; they investigate. By analyzing headers, DOM structures, IP reputation, and historical data, Hunto AI filters out noise and delivers confirmed, actionable intelligence.
- Automated forensic analysis of phishing kits
- Correlation with global threat intelligence feeds
- Visual evidence and detailed incident timelines
Global Impact
Securing Organizations Worldwide
We protect businesses across fintech, healthcare, legal services, telecom, and more — delivering measurable security outcomes.
Browse 15+ Success Stories
Real results speak louder than promises. Discover how enterprises across banking, fintech, and e-commerce achieved measurable security improvements with Hunto AI.
Read all case studiesA co-operative bank in Gujarat × Hunto AI
How a Gujarat co-operative bank strengthens digital trust with Hunto AI Industry Urban Co-operative Banking Scale Multi-branch retail and MSME bank […]
The Union Co-operative Bank × Hunto AI
How The Union Co-operative Bank protects its brand with Hunto AI Industry Urban Co-operative Banking Scale Multi-branch regional bank serving retail […]
Jodhpur Nagrik Sahakari Bank Ltd
How Jodhpur Nagrik Sahakari Bank protects its brand with Hunto AI Industry Urban Cooperative Banking Employees 200+ Product used Hunto AI […]
Knowledge Hub
Insights, Guides & Expert Resources
Stay ahead of emerging threats with our comprehensive library of cybersecurity insights, best practices, and implementation guides.
Explore all resources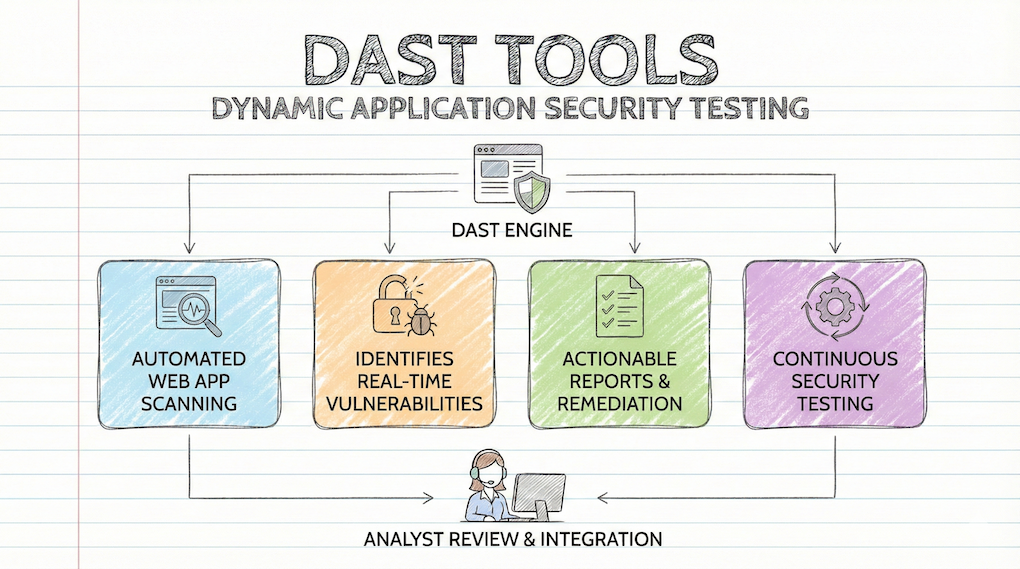
Top 10 Dynamic Application Security Testing Tools (2026)
Modern web applications are complex systems. They use multiple APIs, cloud services, and microservices to function. Securing these apps in 2026 […]
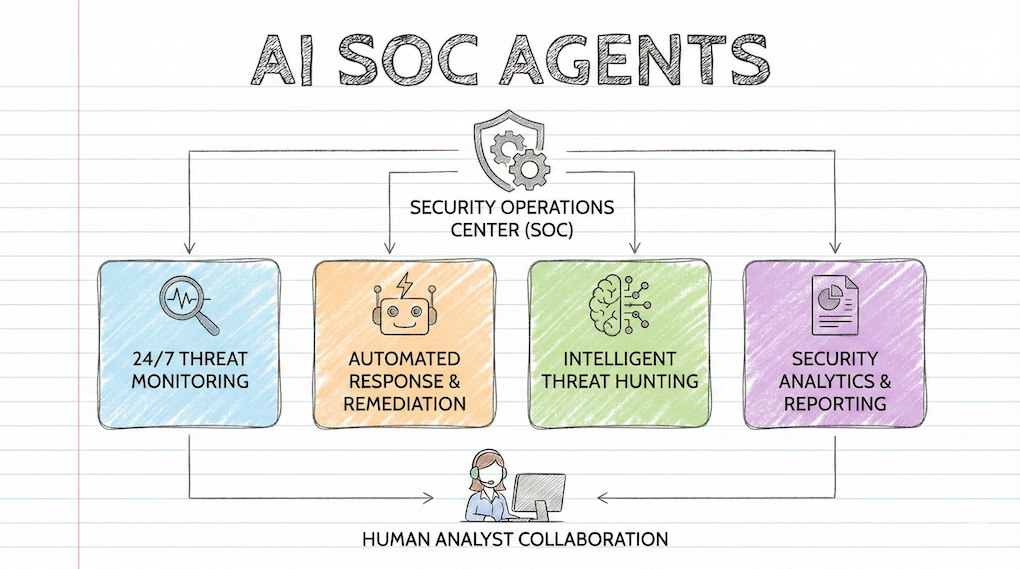
What Are AI SOC Agents? And How Do They Work – Detailed Guide
Modern Security Operations Centers (SOCs) are drowning in alerts and over burdened due to a shortage of skilled analysts. AI SOC […]
6 Best AI SOC Automation Tools for 2026
Security operations centers (SOCs) are drowning in alerts gloabally. Auto generated threats and alert fatigue are leaving cybersecurity teams overwhelmed. To [&
Frequently asked questions
This section answers common questions to help you understand how Hunto AI protects your digital assets and brand against external cyber threats.
Hunto AI is an advanced external threat management platform powered by autonomous AI agents that continuously discover, monitor, and mitigate cyber threats to protect your organization's digital presence.
Unlike legacy tools that require manual intervention, Hunto AI uses 100% autonomous AI agents that work 24/7 without human oversight, providing faster threat detection and response with audit-ready evidence.
Hunto AI protects against phishing, brand impersonation, domain spoofing, data leaks, credential theft, social media fraud, mobile app abuse, and various external cyber threats.
Yes, Hunto AI provides audit-ready evidence and compliance support for RBI, ISO 27001, SOC 2, PCI DSS, HIPAA, GDPR, DPDP, and other regulatory frameworks.
Absolutely. Hunto AI integrates seamlessly with your existing security infrastructure including SIEM systems, email gateways, and other security tools via APIs.

Get A Free Demo
Ready to safeguard your organization's digital presence? Choose your plan and start your free trial.