Safeguard Your Brand Identity
Guard your brand against misuse with our effective Enforcement and Takedown service. Your online presence is your identity in the eyes of customers, your community, and the industry. Rely on us to protect your brand's reputation.
Hunto - Brand Defense
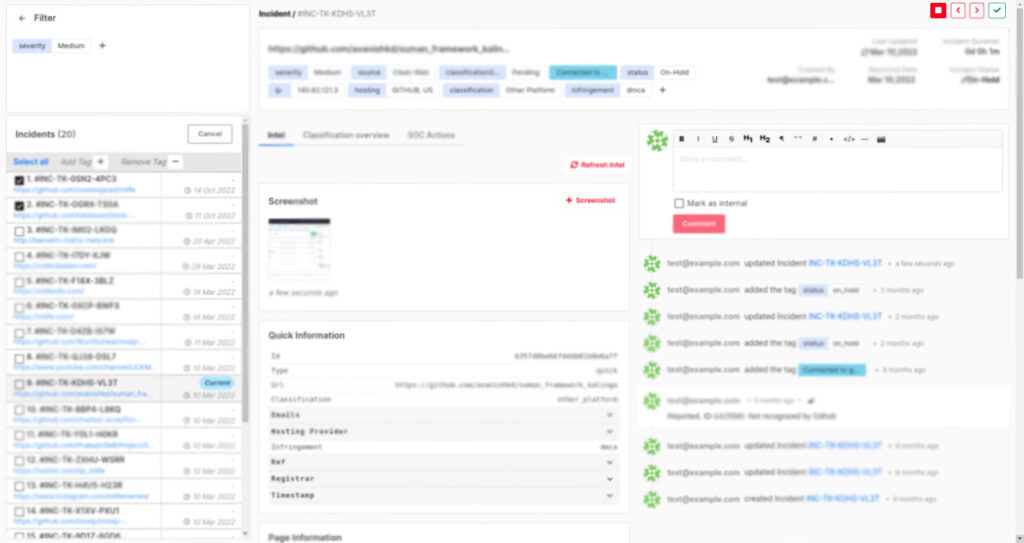
- Automated takedown of incidents
- 24×7 Rogue mobile app monitoring across 150+ platforms
- Immediate action on reporting.
- Extensive reporting and threat management platform
- Cater to your compliance as well as cyber resilience needs
- Spoofed websites that imitate a legitimate website in order to trick users into entering personal information.
- “Typosquatting” websites with common typos made when entering a website’s URL that redirect to a malicious site.
- “Phishing” emails that masquerade as legitimate communications from a trusted source in order to trick users into clicking on malicious links or attachments.
- “Smishing” text messages that masquerade as legitimate communications from a trusted source in order to trick users into clicking on malicious links or attachments.
- “Vishing” phone calls that masquerade as legitimate communications from a trusted source in order to trick users into divulging personal information.
- Malicious advertisements that are displayed on legitimate websites and trick users into clicking on them.
- Malicious attachments that are sent via email or social media and trick users into downloading and opening them.
- “Watering hole” attacks that exploit vulnerabilities in websites that users frequently visit in order to infect their computers with malware.
Domain name phishing attacks are a type of phishing attack where the attacker uses a fake domain name to try to trick the victim into providing sensitive information or clicking on a malicious link. The attacker may register a domain name that is very similar to a legitimate domain name, or they may use a domain name that looks identical to a legitimate domain name but with a different top-level domain (TLD). For example, an attacker could register the domain name “example.com” when the legitimate domain name is “example.org”. We also cover following types of domains:
- Subdomain
- Compromised domains
- Phonetically similar
- Typosquatting domain
- GTLD’s
Online app stores are filled with mobile applications for gaming, mobile banking, shopping, social media and other purposes.
Mobile Apps are available from trusted App stores and from not so trusted marketplaces, and from general websites on the internet.
Criminals are increasingly deploying malicious fake mobile Apps with the objective of stealing credentials and eventually funds from the owner’s banking accounts or other Personal Identifiable Information.
Hunto actively monitors official and unofficial application repositories, analysing current mobile apps, updates and new mobile applications.
Organisations are increasingly relying on social media as an important medium to communicate with their customers and to conduct their business. Brand trust with customers is built over many years. Consumers and organisations both need to protect their brand from malicious activity. The ease at which social media profiles can be created has introduced a new security challenge to both consumers and organisations.
Criminals perpetrate impersonations and other malicious activity. The purpose of the impersonations is varied but can include:
- Basic marketing redirection to an alternative product or service offering that is in competition with your brand
- Identity theft
- Harvesting personal identifiable information, and
- Links to malicious websites that can download malware
Take the Next Step in Strengthening Your Cybersecurity
Our team of experts will walk you through the platform’s features and how it can be customized to fit your organization’s specific needs.
- Free 14-day trial
- Threat Detection
- DMARC Compliance
- Incident Takedown
- Brand Defense