Get Started Today
Discover and Secure Your Entire Digital Footprint
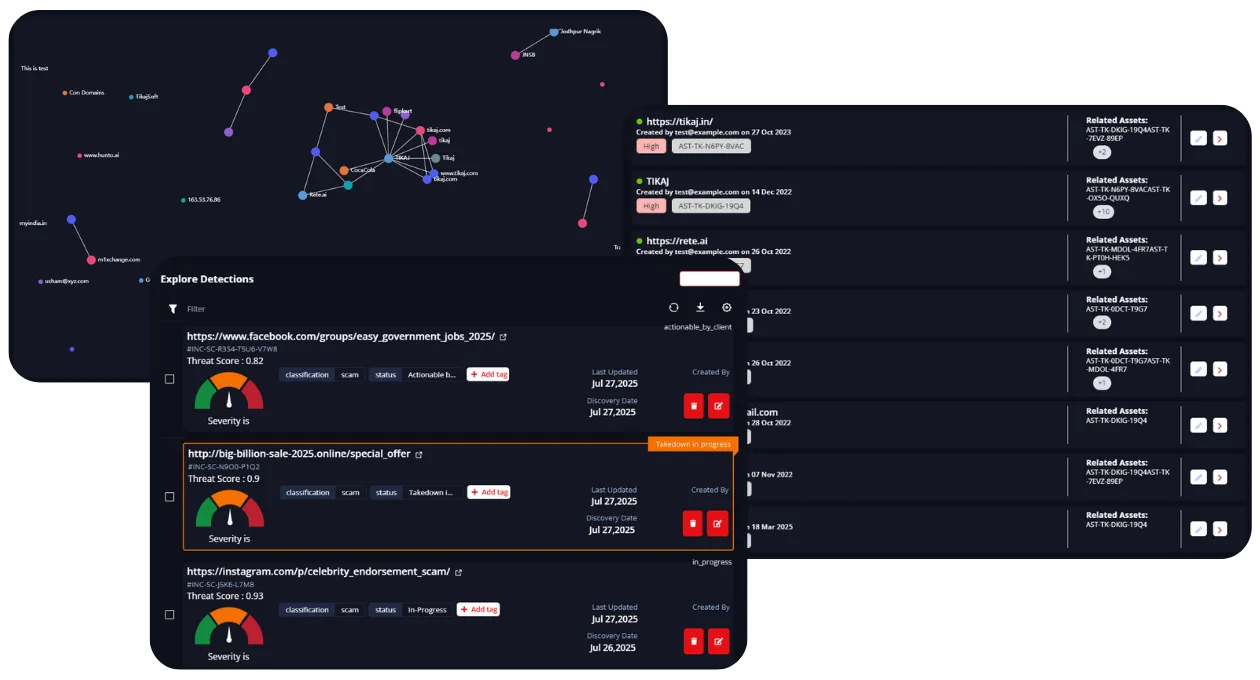
Today’s digital landscape is vast and ever changing. Unseen attack vectors such as cloud misconfigurations, shadow IT proliferation, and asset sprawl make full external attack surface discovery essential for proactive defense. Hunto AI delivers dynamic digital footprint visibility and total control with integrated tools for cloud misconfiguration detection, vulnerability exposure mapping, and more. All capabilities are unified in a single dashboard for efficient management.
Asset Monitoring
Maintain a real-time inventory and monitor domains, unmanaged assets, subdomains, shadow IT components, rogue servers, and exposed data across your brand’s infrastructure.
Everything You Need to Stay Protected
Continuous Asset Discovery
Shadow IT Detection
Real-Time Risk Scoring
Comprehensive Visibility
Automated Exposure Alerts
Prioritized Remediation
Seamless Integrations
Asset Monitoring
Effortlessly Gain Control Over Your
Attack Surface in Just a Few Steps!
- START
1
External Attack Surface Discovery
Automatically identify every public facing and cloud asset including unmanaged shadow IT and poorly configured cloud resources.
2
Asset Inventory Monitoring
Visualize and monitor your complete inventory. Track asset changes and exposures in live dashboards using dynamic mapping.
3
Exposure Prioritization and Threat Detection
Receive exposure scores for each asset. Quickly prioritize critical vulnerabilities, control asset sprawl, and launch rapid remediation using built in workflows.
- FINISH
Data-Driven SEO
Auto-classification (phishing, scam, counterfeit, rogue app)
Competitor Insights
Status tracking: discovered, in progress, takedown requested
Realtime Analyitics
Built-in takedown request flow for phishing and brand abuse
Digital Footprint Visibility Alerts
notifications for new risks or exposed assets
Vulnerability Exposure Mapping
automated analysis of weaknesses targeting your external assets
Change Tracking:
monitor all modifications in your attack surface, across domains, cloud deployments, and more
Frequently Asked Questions.
What is Attack Surface Management (ASM)?
Attack Surface Management is the continuous process of discovering, inventorying, assessing, and securing an organization’s security perimeter and all of the Internet-facing assets within their digital estate. It’s worth emphasizing that attack surface management is not a short-lived task or project, but an ongoing and recursive process that is fundamental to every organization’s cybersecurity program.
As the name suggests, the attack surface is any aspect of an organization’s digital presence that is accessible from the Internet and can therefore be probed for weaknesses by threat actors. It may be helpful to think of your attack surface as the sum of all potential attack vectors that cybercriminals could use to breach your corporate network. Managing the attack surface is an effective way to reduce risk and improve security posture.
Attack Surface Management is also an emerging product class that simplifies and streamlines the ASM process for customers. It automates several steps, including IT asset discovery, risk assessment, and the prioritization of issues based on the risk they present to the organization. By deploying the Rete.ai ASM solution, you can save time that would otherwise be dedicated to these steps, which makes the attack surface management process more efficient and frees up resources to focus on other high priority projects.
What is External Attack Surface Management?
External Attack Surface Management is the process of continuously discovering, inventorying, assessing, and securing all of the external IT assets that an organization owns. An IT asset is considered external if it can be accessed from the public Internet without the use of a VPN.
External Attack Surface Management is generally considered a specific subset of the broader concept of Attack Surface Management. Other adjacent categories include “cyber asset attack surface management,” which covers IT asset discovery and management for both internal and external assets, and “cloud security posture management,” which is a flavor of attack surface management focused exclusively on cloud assets.
The precise definitions of these terms are still up for discussion. As technology and markets evolve, some of these terms will coalesce and others will simply fall out of fashion. The important thing to understand is that external attack surface management is an essential security process that discovers, catalogs, assesses, and secures all external IT assets.
How does Hunto.ai ASM work?
Hunto.ai scans the entire internet to identify your assets — even ones you may have forgotten. Here’s how it works:
Enter your domain
Hunto.ai uses public data (DNS records, SSL certs, subdomain relationships, etc.) to map your infrastructure
It enriches findings with real-time discovery & threat intelligence
Alerts are generated for misconfigurations, exposures, or risky assets
No installation. No agents. Just enter your domain to begin.
How is Hunto.ai ASM different from a vulnerability scanner?
The focus of Attack Surface Management is to identify your full attack surface, including the external assets you do not know about, such as shadow IT, forgotten infrastructure, and misconfigured databases that are accidentally exposed to the open web. This is distinct from vulnerability scanners, which must be given a specific IP range of known assets to function.
What value does Hunto.ai ASM provide?
Hunto.ai delivers ROI by:
Uncovering unmanaged assets, reducing security blind spots
Improving the coverage of existing tools (scanners, pentests, BAS, CART, etc.)
Automating asset discovery, freeing your team from manual work
You get faster time-to-insight, lower risk exposure, and improved efficiency.
What threat intelligence does Hunto.ai use?
Hunto.ai integrates with rich, proprietary threat intelligence including:
Credential leaks
Dark web activity
Phishing kits and malware campaigns
Initial access markets
Botnet and C2 infrastructure data
Your discovered assets are continuously checked against these sources for added context and alerts.
How do I start a free trial or POC?
Getting started is easy. Just:
Visit the contact form on Hunto.ai
Share your corporate email
We’ll provision your trial access in minutes no deployment required
How is Hunto.ai ASM priced?
Pricing is based on your external footprint, including:
Domains & subdomains
IP addresses
SSL certificates
We offer flexible licensing for companies of all sizes. Standard licenses are annual, with discounts for multi-year commitments.
Explore all other modules
Contact Us
We’re eager to hear from you
Do you have a question? A compliant? or need any help to choose the right Plan from hunto? Feel free to contact us
Have a simple question? Check out our FAQ page
Fill out your information and a representative will reach out to you.








