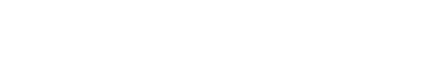Get attacker's perspective to reduce cyber risk
The rapid expansion of technology and the shift to cloud-based solutions have exponentially increased the potential attack vectors for cybercriminals. Enter Attack Surface Management (ASM).
- Stay Ahead of Attackers by understanding your attack surface from an attacker's perspective, you can anticipate potential threats and mitigate them proactively.
- Optimized Resource Allocation by prioritizing vulnerabilities, organizations can allocate resources more effectively, addressing the most critical threats first.
- Enhanced Visibility: ASM provides a clear view of all external-facing assets, ensuring that no potential vulnerability goes unnoticed.
Stay ahead of attackers
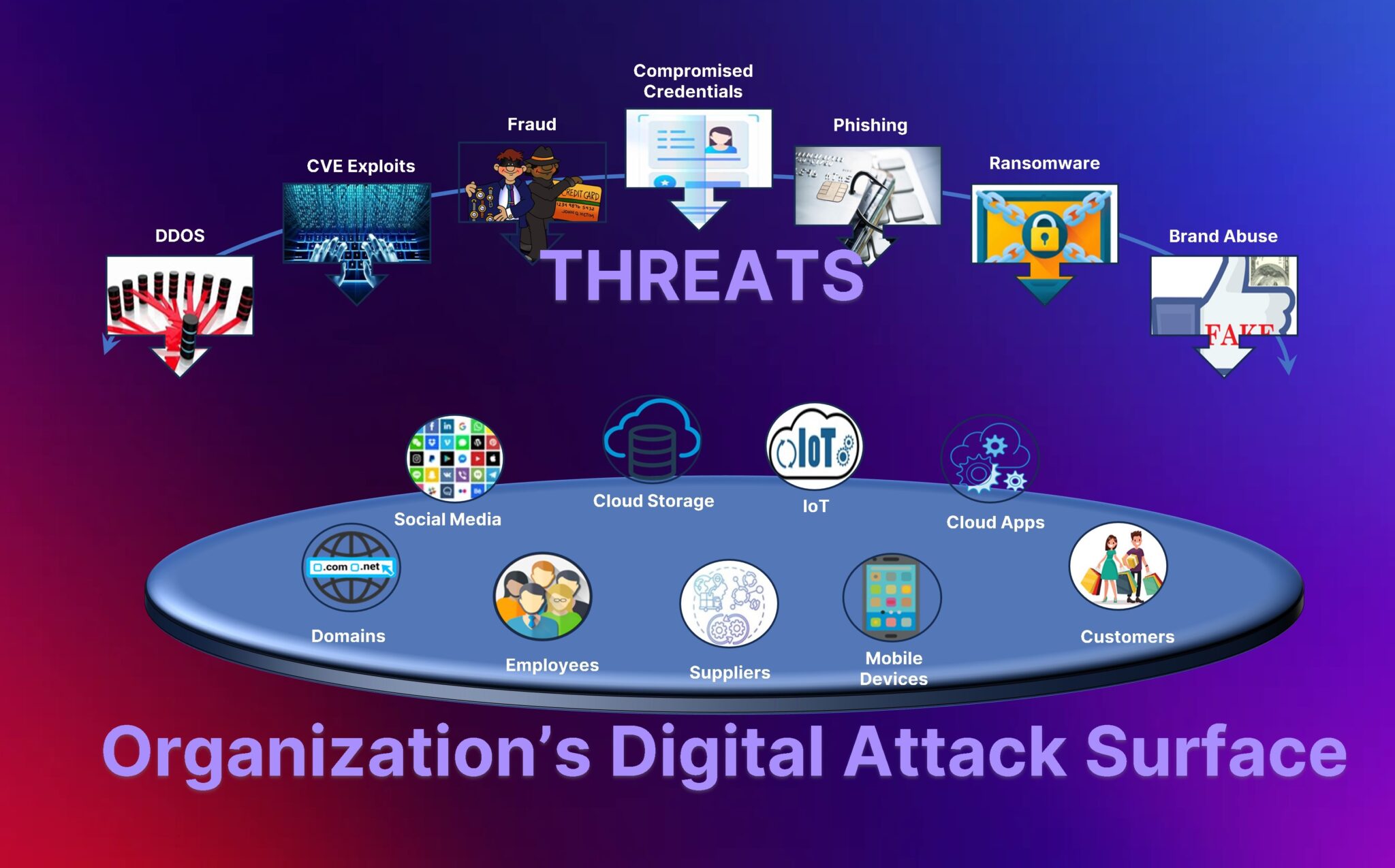
Hunto ASM solution offers a comprehensive, proactive, and adaptive approach to managing and securing an organization’s ever-evolving digital footprint.
Built on four key pillars, Hunto provides comprehensive visibility of external threats targeting your organization.
1. Digital Attack Surface Monitoring
2. Brand Defense
3. DMARC Compliance
4. Deep and Dark Web Monitoring
Digital Attack Surface
Continuous External IT Asset Discovery
Automatically identifies and catalogs all external digital assets, including web applications, cloud services, IoT devices, and even overlooked or forgotten assets, ensuring a complete view of the organization’s digital exposure.
Brand Reputation
Threats that can negatively impact the reputation or perceived value of a brand – come from a variety of sources, such as online phishing scams, social media, and rogue mobile applications.
Confidential Information Exposure
Unauthorized information disclosure of sensitive information – trade secrets, financial data, personal information, and more.
Infrastructure Exposure
Unauthorized information disclosure of assets such as perimeter security assets both physical and cloud based, domains/subdomains, digital certificates, ip addresses.
Brand Defense
Phishing Protect
Phishing is the predominant attack method used by cybercriminals to steal account data and perform online fraud.
Hunto provides world-class phishing detection capabilities that combine automated high-volume data processing with human expertise to identify phishing attacks targeting your brand and customer.
Fake Social Media Profiles Rogue mobile apps
Organizations need to protect their brand from malicious activity on social media platforms.
The ease at which social media profiles can be created has introduced a new security challenge to both consumers and organisations, with criminals perpetrating impersonations and other malicious activity.
Equally, mobile Apps should only be downloaded from stores authorized by the owner to avoid tampered apps with malicious intent.
Brand Abuse
Rogue applications or webpages use your organization’s names, brands logos, likeness to falsely claim affiliation or imply relation without explicit permission from you.
DMARC Compliance
DMARC
Email has been the most prominent aspect of the internet for well over two decades.
The importance of email communications for internal use, between business and its suppliers and also its customers, only highlights the need to safeguard this important medium of exchange.
Email lacks the ability to verify authenticity of all received emails. This fundamental flaw has allowed its exploitation by fraudsters and cyber criminals for malicious purposes.
Email domains configured with DMARC can provide the following key benefits:
- Decrease and stop illegitimate use of valid domains by criminals in spam emails
Prevent Enterprise spear phishing, and other attack variants such as CEO fraud email
Detect misconfigurations of the underlying SPF and DKIM settings - Inventory of all email senders using the valid email domains.
Hunto recommends a full DMARC Compliance program be undertaken and progress from the initial passthrough mode, to quarantine and eventually to reject.
Deep& Dark Web Monitoring
Continually discover new sources
Hunto searches and finds new sources in deep and dark web marketplaces, groups and forums
Analysis and reports
Anallyze volumes of data points to better understand and profile malicious threat actors, including the place of operations, targeted countries or verticals, tools in use and the type of operations often associated with this actor or group.
Mitigate and remediate threats
Assess and respond to threats to your physical and digital assets proactively with the help of our highly skilled analysts.
Monitor digital assets in realtime

Take the Next Step in Strengthening Your Cybersecurity
Our team of experts will walk you through the platform’s features and how it can be customized to fit your organization’s specific needs.
- Free 14-day trial
- Threat Detection
- DMARC Compliance
- Incident Takedown
- Brand Defense