Get Started Today
Protect What Your Brand Stands For
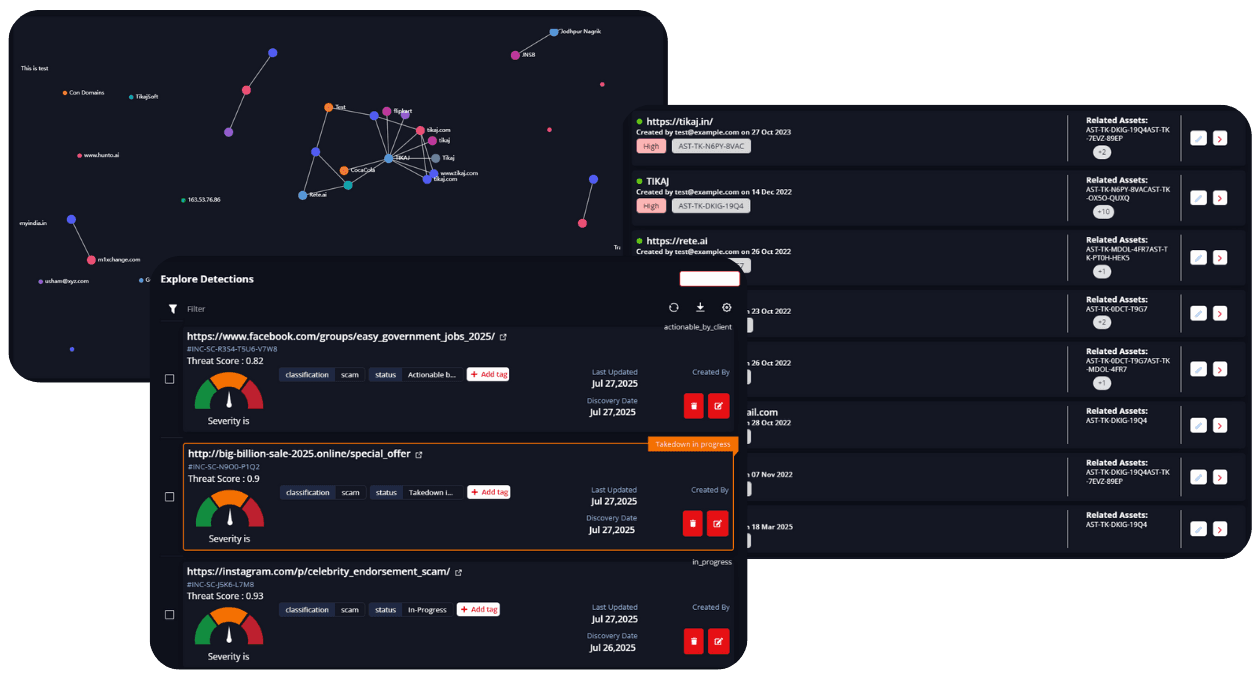
Your brand is your reputation. In today’s digital landscape, it’s constantly under attack from fake domains and phishing emails to rogue apps and social impersonators. Hunto AI actively monitors, mitigates, and eliminates these threats so your brand stays trusted.
Brand Defence
Guard your digital reputation from spoofing, phishing, rogue apps, and impersonation before it damages trust.
OUR BRAND DEFENCE PROCESS
Track, Identify, Neutralize. A Strategic Approach to Brand Protection
We follow a precise 4-step strategy to detect brand abuse early, take swift action, and ensure your digital identity remains safe and trusted
-
Discovery & Detection
Constantly scan the web, app stores, and social media to detect brand impersonation, spoofed domains, and rogue assets in real time.
-
Verification & Analysis
Use AI and human validation to assess threat credibility, classify attack type (phishing, smishing, etc.), and prioritize action.
-
Initiate Takedown
Initiate rapid takedowns of fake websites, mobile apps, and social media profiles through automated workflows and legal escalations.
-
Reporting & Insights
Deliver detailed reports with attack source, action taken, and protection insights to support compliance and boost cyber resilience.
BRAND DEFENSE
Protecting Brand Trust in the Digital World
01
Brand Impersonation Alerts
ACTIVE
Rapidly detect and flag look-alike domains, fake websites, and social profiles attempting to misuse your brand’s identity.
This solution empowers your team to respond instantly to digital impersonations, preserving customer trust and preventing fraud.
02
Fake App Detection
ONGOING
Monitor official and third-party app stores for rogue applications that exploit your brand for malicious purposes.
Stay secure as our system uncovers fraudulent apps and guides you through swift takedown, protecting both users and reputation.
03
Dark Web Brand Surveillance
REAL-TIME
Scan hacker forums, marketplaces, and leak sites for exposed credentials or unauthorized use of your brand assets.
Proactive monitoring uncovers threats at the earliest stage, enabling immediate response to prevent downstream damage.
04
Automated Takedowns
ACTIONED
Trigger removal of malicious domains, phishing sites, and counterfeit brand assets automatically via global enforcement workflows.
Accelerate incident resolution and ensure brand protection with smart, streamlined takedown capabilities.
Frequently Asked Questions.
What is Hunto.ai Brand Defence?
unto.ai Brand Defence is a proactive cybersecurity solution designed to protect your brand’s reputation from digital threats such as impersonation, phishing, fake domains, rogue apps, and social media misuse. It continuously monitors the internet for any unauthorized or malicious use of your brand identity and takes swift action to neutralize those threats before they impact customer trust or compliance.
How does Hunto.ai detect brand misuse or impersonation?
Using a combination of advanced AI scanning and human validation, Hunto.ai monitors the web, app stores, and social media platforms in real time. It identifies signs of brand abuse—like lookalike websites, impersonator accounts, or unauthorized app listings—by analyzing domain names, content patterns, metadata, and branding elements. Once a suspicious asset is detected, it’s verified, classified, and prioritized for action based on the threat level.
What happens after a threat is detected?
When Hunto.ai confirms a threat, it triggers an immediate response. This includes automated takedown requests to hosting providers, registrars, and platform operators, along with legal escalations if required. The system tracks every step of the takedown process until the malicious asset is removed, ensuring rapid mitigation and minimal exposure to brand damage.
What kind of threats does it help prevent?
Hunto.ai protects your brand from a wide range of digital impersonation threats—such as phishing domains, fake social profiles, smishing attacks, and unauthorized or malicious mobile applications. By catching these threats early, the platform helps prevent fraud, protects customers from scams, and maintains the integrity of your brand online.
Will I receive reports or alerts about brand abuse?
Yes. Hunto.ai provides detailed, easy-to-understand reports outlining what threats were found, how they were handled, and the actions taken to resolve them. These reports include threat source, type, severity, takedown status, and recommended next steps. They’re ideal for internal security tracking, regulatory compliance, and strengthening your overall digital risk posture.
Explore all other modules
Contact Us
We’re eager to hear from you
Do you have a question? A compliant? or need any help to choose the right Plan from hunto? Feel free to contact us
Have a simple question? Check out our FAQ page
Fill out your information and a representative will reach out to you.



