AI Agents for Cybersecurity: The Ultimate 2025 Guide to Deploying Agentic Defense
Security teams don’t get judged by how many alerts they triage; they get judged by outcomes: fewer incidents, faster containment, cleaner audits, and less disruption to customers. That is why 2025 is the year “AI agents for Cybersecurity” stop being a buzzword and become the default operating model for modern security programs. In plain language, an AI agent in cybersecurity is software that doesn’t just describe a problem, it scopes your environment, discovers issues, decides on the right action, executes it under guardrails, verifies that the action worked, and then proves the result with time-stamped evidence.
This guide explains what Cybersecurity AI Agents mean in practice, why enterprises and regulated institutions should shift to agentic defense, how to deploy agents safely, and exactly which metrics to use so leadership can see progress in days rather than quarters. Along the way, learn how Hunto AI implements AI agents for Cybersecurity, because the market needs real systems, not theory.
Table of Contents
The goal of this article is to help you build a durable, measurable approach whether you buy, build, or blend AI Agents for Cybersecurity.
Why 2025 is the tipping point on AI Agents for Cybersecurity?
Most organizations spent the last decade collecting tools and dashboards, and only in the last few years started asking hard questions about time-to-remediation and time-to-evidence. Cloud growth didn’t slow down while those dashboards multiplied: internet-facing assets change daily, test subdomains appear and never get decommissioned, contractors spin up storage for “just a week,” and marketing runs campaigns on landing pages that security never knew existed.
Meanwhile, attackers scaled their own automation. The compliance bar also moved. Supervisors and auditors increasingly expect continuous monitoring with artifacts (not quarterly or once a year), not anecdotes: when was this risk discovered, who acted, what policy was applied, which platform accepted the takedown, and where is the before/after proof.
The cost math forced the issue. If teams spend hours assembling screenshots and writing notices, that’s money diverted from prevention to paperwork. AI agents change the dynamic by collapsing the loop from detection to mitigation, reducing “human-in-loop” work where it adds little value, and standardizing the evidence trail so audits stop consuming entire sprints.
What an AI Agent for cyber security agent really is (and isn’t)
An AI security agent is a bounded, policy-aware system that continuously scopes internet and your environment, discovers changes and signals, decides on actions based on risk and policy, acts natively on external platforms or internal systems, verifies that the act achieved the intended result, and proves it with threat intelligence and artifacts suitable for audit and learning.
The emphasis on autonomy, verification, and proof is the difference between activity and outcome. Without verification, you measure effort; with verification, you measure security The agent loop is simple to say and hard to deliver: Sense → Decide → Act → Verify → Prove.
Sense: Sense aggregates external data (DNS, WHOIS, TLS, page content, social/app store/ad listings, leaked-data sources) and optional internal context (ticketing, SIEM, mail auth, cloud inventory).
Decide: Decide blends statistical scores (EPSS, CVSS), business context (is this asset on the login path; is it tied to payments or PII), and policy (what is allowed to be changed automatically; when to require an approval).
Act: Act means platform-native actions: submit a registrar abuse notice, file an app-store takedown, open and assign a ticket with the right replication steps, set DMARC policy stages, schedule a phishing simulation for a specific cohort.
Verify: Verify is a second-order scan or check: recrawl the page, re-fetch headers, confirm the ad is down, ensure the app listing is removed, run a search for mirrors.
Prove: Prove is the exportable evidence bundle: before/after screenshots, header diffs, platform receipts, timelines, and a mapping to your policy or regulatory expectations. You can bolt that evidence into incident records, board packs, vendor reviews, and audit responses. Without it, you will always be explaining; with it, you can simply show.
Where AI agents can deliver the most value for cybersecurity

The first beachhead for most organizations is the external world, because those surfaces are the fastest to attack and the easiest to verify after action. Agentic Attack Surface Management discovers new domains and subdomains as soon as they resolve, fingerprints exposed services, and flags misconfigurations that create real risk, from weak TLS and missing headers to forgotten admin panels and open indexes.
The next obvious value pool is brand impersonation: look-alike domains, fake support pages, clone apps, malicious search ads, and social imposters. Here, agentic defense shines because the act phase is clear and the verification is unambiguous: you either got the asset removed or you didn’t.
Human Risk is a third high-yield area. If simulations are annual and generic, they teach habits for a week; if they are continuous, role-aware, and paired with micro-training, they reduce risk every month.
Measuring Agentic Defence — The metrics that actually matter (and how to instrument them)
Security leaders rightly distrust vanity numbers. The point of deploying AI Agents for Cybersecurity is to move a few rigorous operational metrics that any board member or regulator can understand.
New-asset detection speed
The first is new-asset detection speed, measured as the median time from when a domain or service becomes publicly resolvable to when the platform first sees it. A realistic target for external discovery is a median under twenty-four hours with a P90 under forty-eight hours.
Critical closure velocity
The second is critical closure velocity, measured from first detection of an externally exploitable issue to the moment the agent’s re-test passes. A defensible goal is at least seventy percent of criticals closed within seven days and a median time-to-remediate under five days, with one hundred percent of closures auto-verified.
Median time-to-takedown
For brand defense, measure median time-to-takedown: under twenty-four hours for domain/hosting cases and under twelve hours for social/app store listings after evidence submission.
Human Risk Number
For Human Risk, track the “Human Risk Number” over time, plus click-through and repeat-clicker rates; make your objective a forty-to-sixty percent CTR reduction over ninety days and a seventy percent improvement among repeat-clickers after targeted training.
Time-to-evidence
Finally, keep an eye on a deceptively simple governance metric: time-to-evidence. If an auditor asks for proof of an action, your system of record should render it within a business day without a manual hunt.
Guardrails: How to trust cybersecurity AI Agents autonomy without fear
The reluctance to allow software to act is often rational. The answer is not to avoid autonomy but to channel it with controls.
Defined Scope
Define scope at the outset: which domains, which brands, which stores and networks, which geographies. Create a simple list of sensitive actions that require a human approval, such as email policy enforcement or DNS edits, and leave routine takedowns and ticket creation to the agent.
Rate Limits
Apply rate limits so you never overwhelm a platform with notices. Keep an explanation trail that captures why a finding scored as it did and why a particular action was chosen. Above all, insist on rollback and compensating controls for actions with user impact. If those guardrails are present, you will discover that autonomy reduces risk rather than adding it.
Deploying AI Agents for Cybersecurity – Hunto AI 90-Day Plan
Week 1: Baseline and boundaries
We start with deploying a dedicate AI agent pointing at your public domains and brands, set scopes, and codify dual-control rules. Run a forty-eight-hour discovery sweep and publish your live risk number with a short narrative:
- here is where we are,
- here are the top ten externally exploitable exposures,
- here is our goal for week two.
Week 2 to Week 4: Quick/Visible Wins
We enable agentic attack surface and brand monitoring, close the top ten issues, and execute your first takedowns. Publish an “official channels” snippet that lists verified URLs, app IDs, and handles so customer-facing teams have a single page to share. Wire ticketing so owners and vendors see clean, deduplicated work items with evidence attached.
Week 5 to Week 8: Standardize Agentic Workflow
Start Human Risk simulations for high-risk cohorts, launch DMARC+ discovery, connect SIEM or SOAR for visibility and correlation, and turn on mirror suppression logic so takedowns clear clusters of abuse rather than single URLs.
Week 9 to 14: Scaling Agentic Defence
Export a quarter-end evidence pack, label vendor-managed public assets and set SLAs, and publish an executive dashboard that reports new-asset MTTD, critical MTTR, median TTD, first-notice acceptance, and risk-weighted reduction. We maintain this cadence for your board and responsible stakeholder to see agentic defense as a continuous and active defense program, not a project.
Build vs. Buy vs. Blend AI Agents for Cybersecurity: A scorable checklist you can take to procurement
The market is noisy, so score what matters. Here is Hunto AI’s checklist to internally assess our AI Agent’s capabilities:
Autonomy and actions:
- Can the platform act natively on registrars, hosts, social networks, app stores, and ad platforms;
- Can it open tickets with the right owners;
- Can it change email policy in stages;
- Does it verify and suppress mirrors after action.
Risk reasoning:
- Does prioritization mix exploitability, business context, and regulatory cues so the top of the list matches real attack paths.
Evidence and compliance:
- Does every closure include before/after artifacts and policy receipts,
- Can you export clause-mapped packs for audits without manual assembly.
Time-to-value:
- Can you get a forty-eight-hour baseline with a live risk number and deliver first takedowns within a day of evidence submission.
Integrations and fit:
- Ticketing
- SIEM/SOAR
- Cloud DNS/CDN
- Email security
- Role-based access
- Ownership mapping by domain, business unit, or vendor
Cost to operate:
- Is duplicate noise kept under five percent week-over-week,
- Are at least seventy percent of criticals closing within seven days.
If a platform scores high on those dimensions, it is ready for enterprise scale reality.
The financial case for cybersecurity AI agents
Agentic defense is not only a security story; it is a cost story.
Start with resource cost
Analysts spend surprising time on non-decision work:
- collecting screenshots,
- rewriting near-identical notices for different platforms,
- chasing ownership,
- and documenting status for audits.
If agents do that work automatically, you are effectively returning analyst weeks to higher-value tasks.
Consider time-to-mitigation
The window between public exposure and attacker action is measured in hours for some classes of abuse; shaving days off that window is the difference between near-misses and incidents.
Software bloat
Buying a monolith because it includes a dozen modules you might use “someday” creates drag and discourages teams from switching on what they actually need.
A model where you deploy agents individually and pay for what you use keeps the bill tied to value.
Compliance dividend
The ability to produce evidence on demand without war-rooms, and the total cost picture becomes favorable even before you account for avoided incidents.
Hunto AI’s Agentic Defense — Deploying Dedicated AI Agents for Cybersecurity
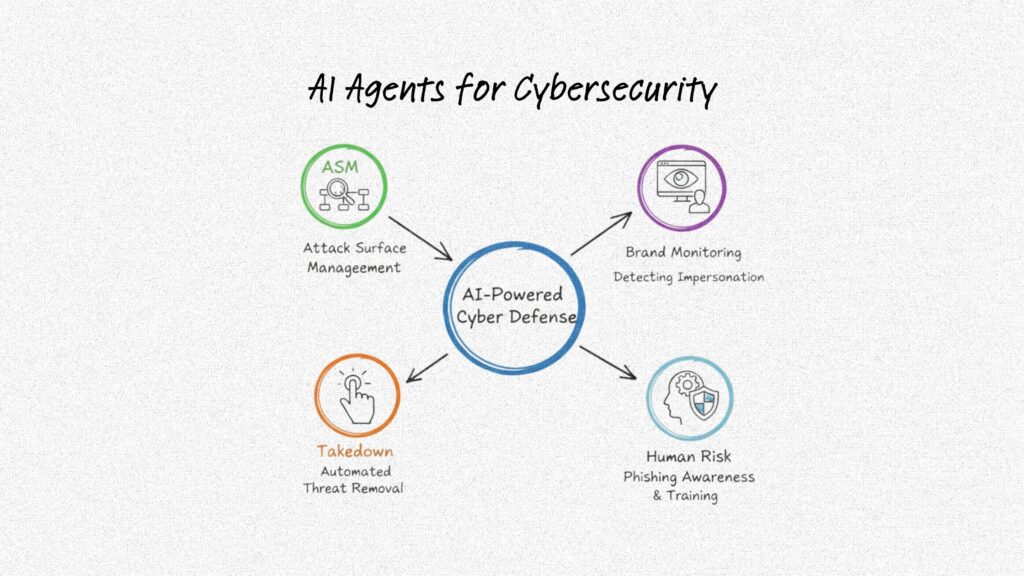
Hunto AI builds Cyber Security AI Agents that follow the exact loop described above, and you can deploy them individually rather than buying a bloated suite. Hunto AI’s five agents are:
- Agentic Attack Surface Management,
- Agentic Brand Monitoring,
- Agentic Human Risk,
- Agentic Takedown,
- Agentic DMARC+.
Each agent is 100 percent autonomous within clearly defined scopes and guardrails, produces time-stamped, audit-ready artifacts, and can be deployed as a dedicated on-premise instance when you need strict data boundaries.
Most teams see a live risk number within forty-eight hours, first takedowns inside twenty-four hours of evidence submission, and a forty-plus percent reduction in risk-weighted exposures within the first month.
If you only need one capability, you deploy one agent and pay for the usage you actually exercise; if you need more coverage, you add agents without re-platforming. That modularity and the evidence-by-design model are the reasons Hunto’s agentic approach is resonating with banks, fintechs, and listed enterprises that must show outcomes, not just activity.
Deep dive: How to adapt cybersecurity agents to your organization (not the other way around)
The most overlooked advantage of agentic defense is adaptability.
Traditional software forces process changes on teams: new queues, new roles, new handoffs. Because traditional cybersecurity can only operate one way.
Agentic Cyber Security flips the requirement. Cybersecurity AI Agents adapt to your ownership maps, your approval rules, your cloud conventions, and your regulatory posture.
In a bank, the same brand-abuse takedown might need legal’s sign-off before first notice; in a startup, security and marketing may own it together and move immediately. The agent shouldn’t care; it should support both with configurable approvals and tracking.
For Human Risk, agents can run continuous campaigns that reflect how different teams actually work. A finance cohort that handles payouts is not the same as a field-sales cohort; templates, timing, and micro-training differ, and the agent should evolve with observed behavior.
Adaptability and security is also what makes on-premise AI agents compelling. If your risk committee wants the entire model, prompt, and artifact trail inside your control boundary, deploy agents on your infrastructure; if you don’t need that, run them as a managed service.
The compliance conversation, simplified with cybersecurity AI Agents
Whether you operate under banking supervision, national cyber directions, or privacy law, the question is the same:
Are you monitoring continuously, are you acting in time, and can you show proof.
Agentic defense makes compliance conversation easier.
Detected phishing or impersonation? You can produce a case file with discovery time, first action time, evidence submitted, and platform acceptance, plus a re-scan with the asset gone.
External exposure flagged and closed? You can show before/after headers and screenshots and the change in the risk score for that asset.
Regular phishing simulations expected by your regulator? You can export the calendar, cohort results, and the Human Risk trend.
Email-auth alignment? You can share the sender inventory, policy stages, and user-impact checks. Compliance people don’t need perfection; they need a credible system of record. Agentic defense gives you one.
Next Steps for deploying your first AI Agent for cybersecurity
if you want a concrete feel for how this looks in your environment, run a forty-eight-hour external scan, publish your live risk number, execute one or two takedowns, and export an evidence pack.
Whether you do that with Hunto AI or your own build, the habit of proving outcomes will change how your program operates, and how your stakeholders see it.