Attack Surface Management
Secure your digital footprint proactively with our AI-powered solution. We provide complete visibility and protection against external threats that traditional defenses miss.
Start here
AI Evolution of Threat Takedowns
Hunto AI delivers next-generation cybersecurity from an attacker’s perspective, ensuring complete protection across all external-facing digital assets. Our journey has been dedicated to setting the gold standard in threat counteraction, leveraging 90+ global partners and AI to perform 15,900+ successful takedowns last year. We are your strategic partner in eradicating threats and elevating security.
Threats & data points analyzed
Global partners for takedown and solutions
Compliances addressed
Types of cyber attacks remediated
Solving Human Cyber Security Challenges
See how Hunto AI addresses your critical human-centric security needs.
Problem
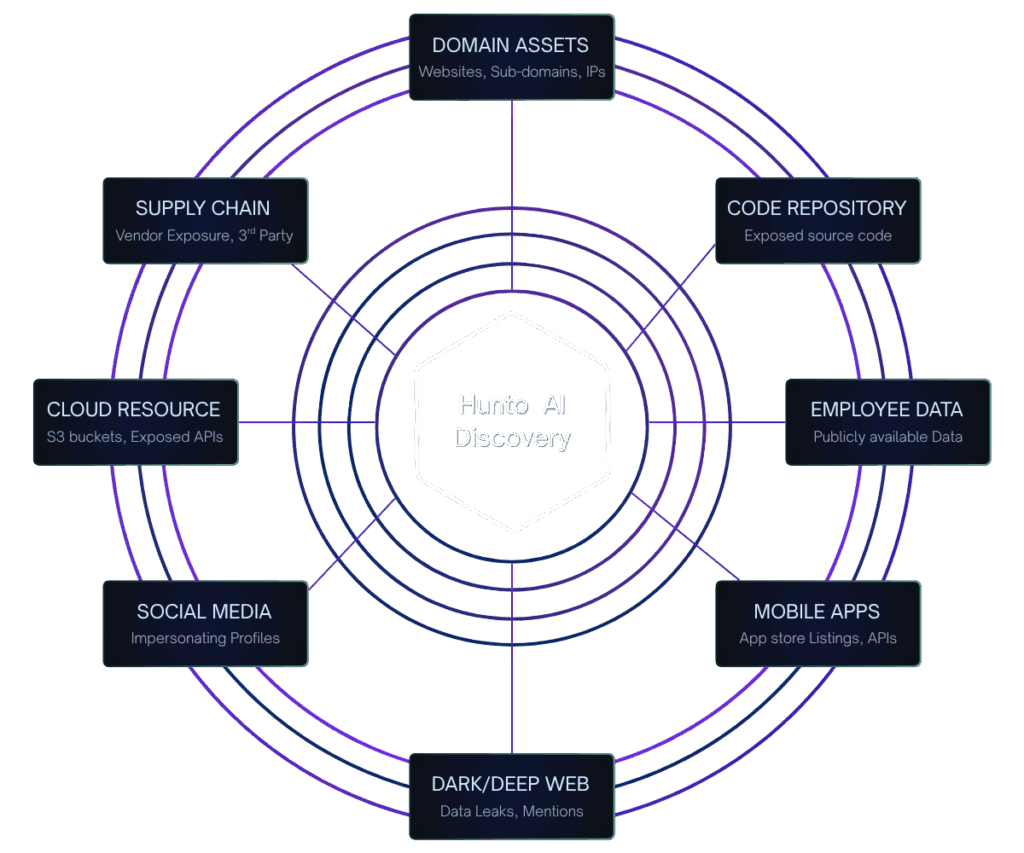
Security teams lack comprehensive visibility into the rapidly expanding external attack surface, leaving Shadow IT, rogue domains, and unknown cloud assets exposed to sophisticated attackers
Solution
Hunto AI continuously identifies and inventories all external digital assets (cloud, mobile, on-premise) from an attacker’s perspective, ensuring complete coverage and eliminating critical blind spots.
- Complete asset visibility, including Shadow IT.
- Continuous identification of all threats.
- Automated Drift Detection for instant alerting on system changes.
Problem
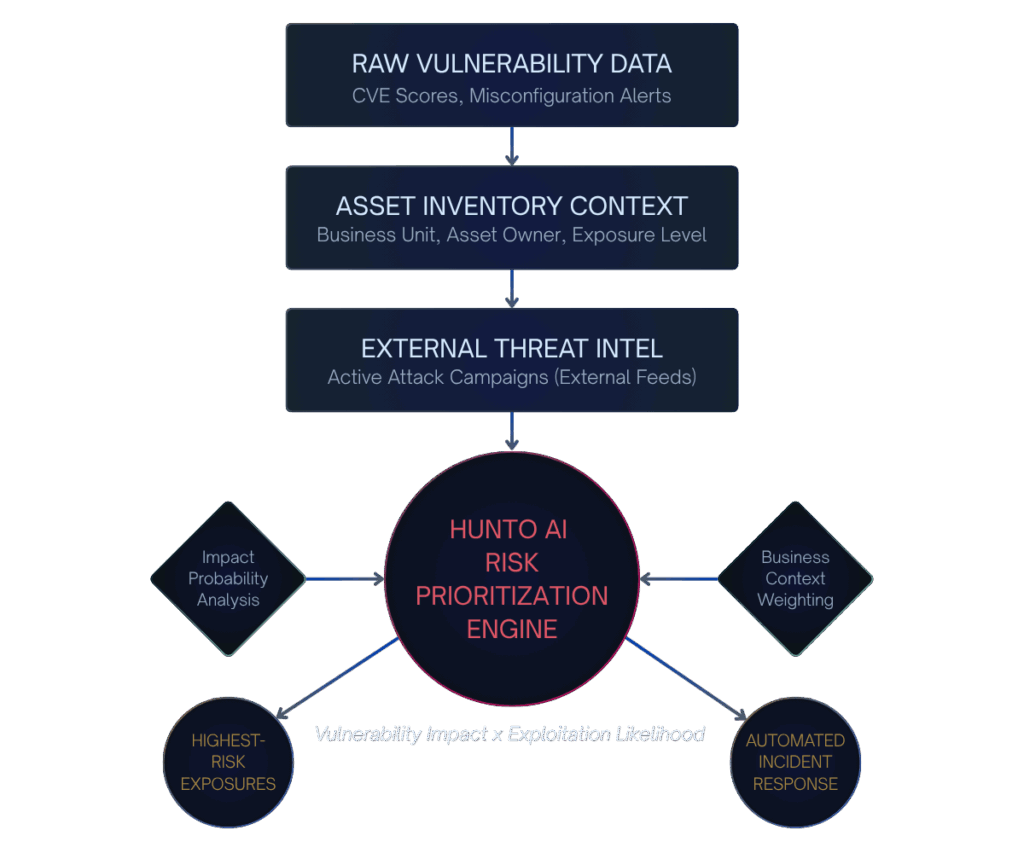
Overwhelmed teams waste resources patching low-impact vulnerabilities because traditional scanners fail to assess exploitation likelihood or prioritize the actual threat to the business.
Solution
Advanced algorithms continuously assess vulnerability impact and exploitation likelihood, directing resources to the highest-risk exposures for maximum security effectiveness.
- Intelligent algorithms prioritize risks based on impact probability.
- Automated Incident Response via remediation workflows
- Security Policy Orchestration: Real-time risk assessments.
Problem
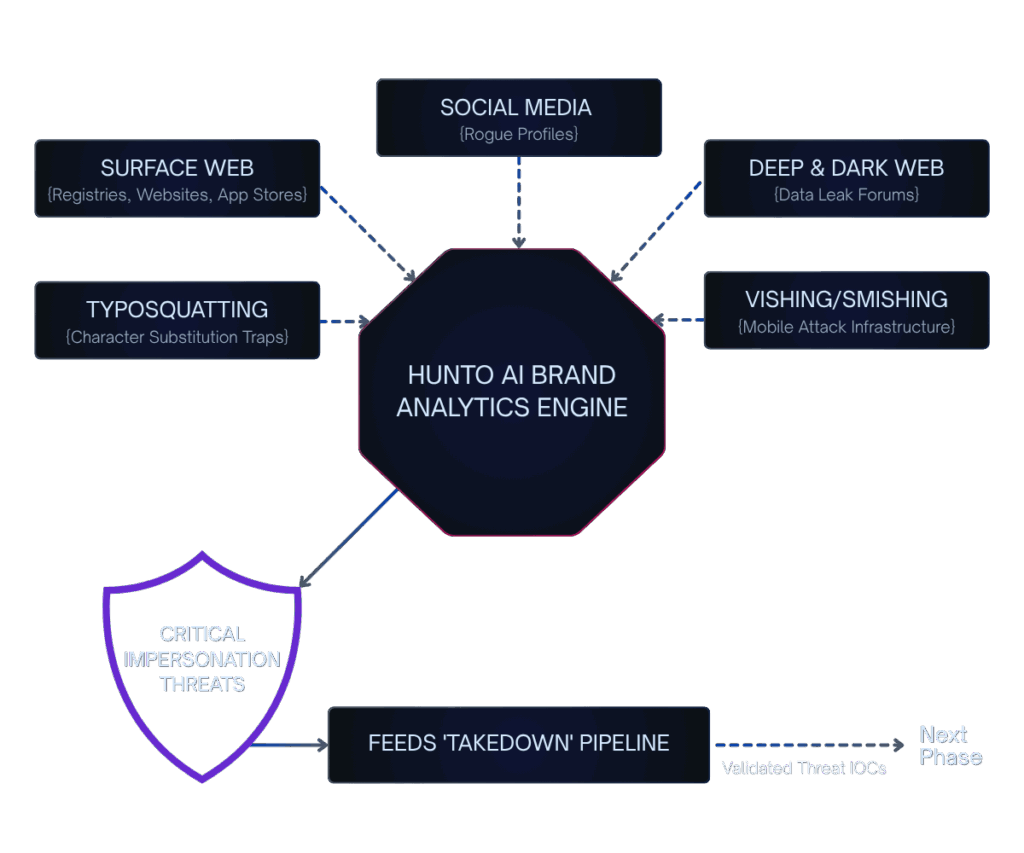
External threats like phishing sites, typosquatting traps, and rogue social media accounts directly threaten brand reputation, customer trust, and lead to data loss.
Solution
We proactively detect and swiftly remediate phishing sites, rogue domains, and impersonation attempts across the surface and deep web, safeguarding your brand reputation and customer trust.
- Detection of phishing, trademark infringement etc.
- Monitoring your brand across surface web and deep web.
- Remediation of threats like Typosquatting Traps and Vishing scams.
Problem
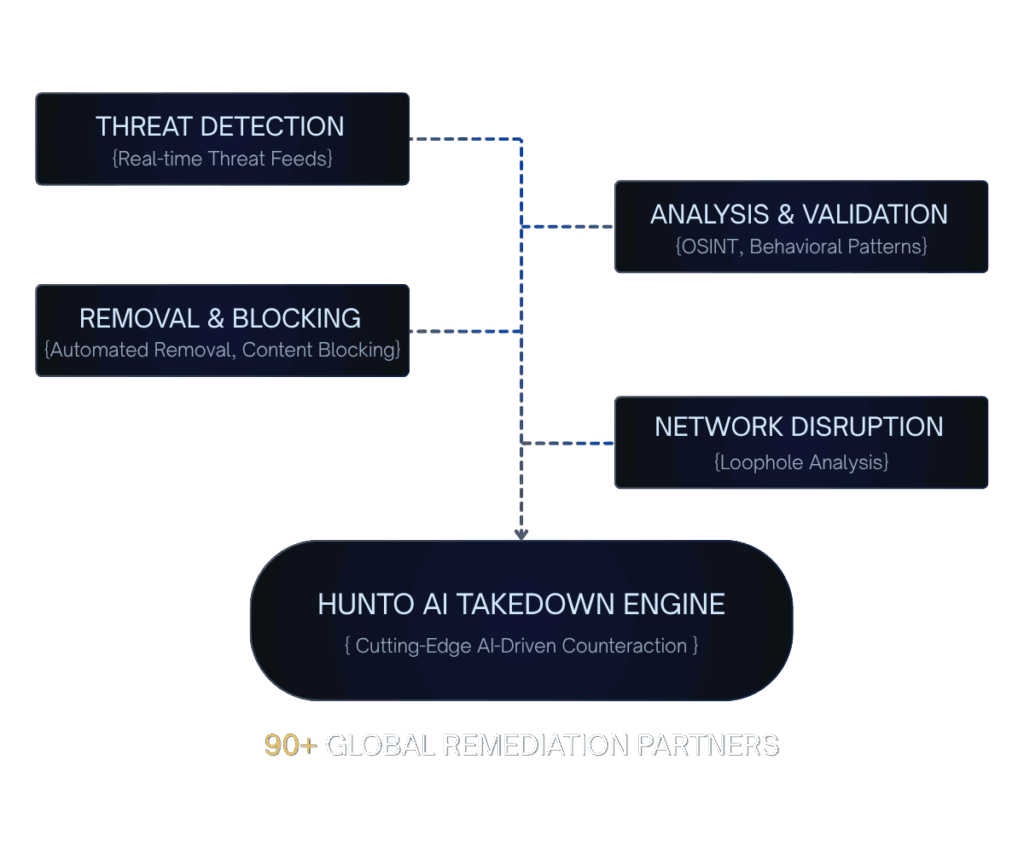
Manual threat counteraction is slow and often incomplete, failing to dismantle the underlying attack network, allowing threats to quickly reappear and persist.
Solution
We employ a four-phase process; Detection, Analysis, Takedown, and Disruption: using our cutting-edge AI engine and 90+ global partners to swiftly and permanently neutralize threats.
- Analysis & Blocking: Harness OSINT and report incidents.
- Swiftly and efficiently remove harmful content using the AI engine.
- Disruption: Analyze network loopholes and continuously monitor.
Key Capabilities
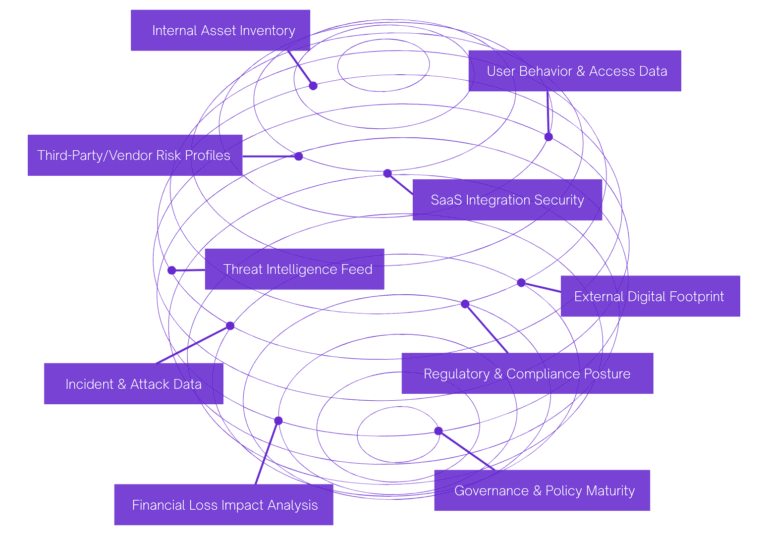
ASM provides the critical inventory of all external risk. Its continuous discovery and comprehensive vulnerability prioritization are seamlessly amplified by insights from Threat Intelligence and integrated with Digital Risk controls across the entire platform.
Continuous Intelligence-Driven Discovery
ASM’s continuous mapping of the external attack surface is guided by real-time indicators of compromise (IOCs) and threat actor TTPs from our Threat Intelligence module. This ensures the discovery engine prioritizes scanning assets currently targeted in the wild
Warning
Your data might be
at risk

Validate External Risk Remediation
ASM validates the effectiveness of defensive measures by continuously checking known Digital Risk Protection (DRP) targets (e.g., fraudulent domains, fake social media). If a spoofing domain is missed by DRP, ASM identifies it as an unmitigated risk, closing the loop.
Vulnerability-Aware Human Risk Scoring
ASM’s vulnerability prioritization identifies high-risk technical flaws (e.g., misconfigured email server settings, exposed RDP ports). This technical context is used to raise the Human Risk Number (HRN) of owners/teams responsible for those critical assets, driving accountability.
Measurable outcomes in just days.
Complete Asset Visibility
Continuously identify all external digital assets, including Shadow IT and orphaned systems, to eliminate all blind spots.
Real-Time Risk Prioritization
Advanced algorithms assess vulnerability impact and exploitation likelihood, directing resources to the highest-risk exposures first.
15,900+ Takedowns/Year
Proven counteraction ability, achieving swift and efficient removal of harmful content with our cutting-edge AI engine.
Proactive Brand Protection
Detect and remediate phishing sites, rogue domains, and impersonation attempts across the surface and deep web.
Automated Incident Response
Streamlined remediation workflows enable rapid patching, configuration changes, and threat mitigation to minimize attack surface in real-time
Threat Intelligence Enrichment
Enhance alerts with actionable insights from 1M+ threats and data points analyzed, supporting advanced attribution analysis.
Check Our Core Takedown Features
Hunto AI delivers next-generation cybersecurity from an attacker’s perspective, ensuring complete protection.
Automated Drift Detection
Continuously monitor system changes, misconfigurations, and exposure anomalies with instant alerting to prevent security policy drift.
Security Policy Orchestration
Automatically adjust security controls and configurations based on real-time risk assessments for continuous defense hardening.
Forensic Timeline Analysis
Detailed attack path reconstruction with evidence collection to streamline incident response workflows and post-mortem analysis.
Deep Web & Dark Web Monitoringc
We monitor your brand through AI-based search, not only on the surface web but also on the deep web to capture phishing and impersonation threats.
AI Takedown Engine
Employ our cutting-edge AI engine to swiftly and efficiently remove harmful content, safeguarding your brand’s digital reputation with precision.
Network Disruption
After takedown, we analyze for loopholes and take action against the network, continuously monitoring to ensure threats stay neutralized.
What "Great" Looks Like (Built for Zero Trust)
See how Hunto AI secures your digital infrastructure against external threats and asset exposure.
Real-Time Asset Discovery
Continuously identify all external digital assets, including Shadow IT, orphaned systems, and forgotten domains across all environments.
Automated Drift Detection
Continuously monitor system changes, misconfigurations, and exposure anomalies with instant alerting and policy enforcement.
Multi-Vector Threat Remediation
Adept at addressing 70+ types of cyber attacks—Phishing, Typosquatting, Vishing, Rogue Apps, and Watering Hole tactics.
Automated Incident Response
Streamlined remediation workflows enable rapid patching, configuration changes, and threat mitigation to reduce your attack surface in real-time.
Continuous Risk Prioritization
Advanced algorithms assess vulnerability impact and exploitation likelihood, directing resources to the highest-risk exposures for maximum effectiveness.
Threat Intelligence Enrichment
Enhance alerts with actionable insights from global threat feeds and attribution analysis derived from 1M+ data points analyzed.
Common Questions
Frequently asked questions
This section answers common questions to help you understand how Hunto AI protects your digital assets and brand against external cyber threats.
Hunto AI continuously identifies all internet-facing assets, including cloud services, web applications, APIs, domains, IoT devices, and unmanaged shadow IT resources.
Advanced risk-scoring algorithms evaluate both impact probability and exploitation likelihood, ensuring your team focuses on the most critical exposures first.
Yes. Hunto AI seamlessly connects with SIEM platforms, cloud providers, email gateways, domain registrars, and ticketing systems to enhance and unify your security workflows.
The platform continuously monitors infrastructure and application settings for unauthorized changes or misconfigurations, triggering instant alerts for remediation.
Hunto AI enriches asset and vulnerability data with global threat feeds, dark-web monitoring, and attribution analysis to deliver contextual insights and predictive attack patterns.








