Supercharge Cybersecurity with Hunto AI
Defeat threats efficiently and identify attackers proactively with a revolutionary cyber threat intelligence platform powered by Hunto AI.
Start here
The Intelligence Evolution of Cybersecurity
For too long, organizations have operated reactively, defending their infrastructure only after an attack has begun. Hunto AI’s mission is to change this by making your defenses proactive. Our platform understands the threat actors targeting your organization, providing the knowledge of how, when, where, and why they will strike. We transform massive amounts of raw data, including Dark Web forums and vulnerability intelligence, into actionable insights. This intelligence, aligned with the MITRE ATT&CK framework, optimizes your defenses, effectively preventing breaches, fraud, and other cyber threats at their source.
Threats Blocked
Intelligence Sources Used
Automation of Security Workflows
Intelligence Types Delivered
Solving Cyber Threat Intelligence Challenges
See how Hunto AI transforms raw data into Strategic, Operational, and Tactical intelligence for proactive defense.
Problem
Security teams are overwhelmed by raw, disparate data feeds (IOCs) from limited sources, making it impossible to gain comprehensive, real-time visibility into emerging threats.
Solution
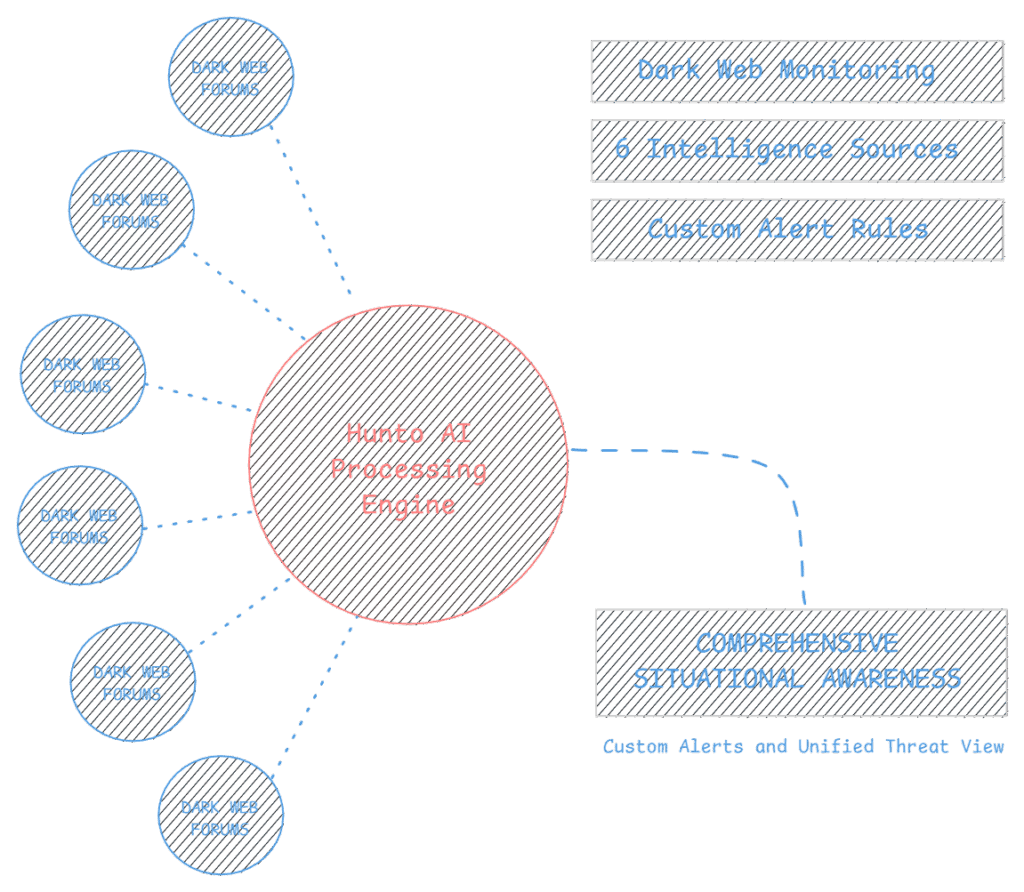
Continuously collect data from 6 diverse intelligence sources- including Dark Web forums, paste sites, and ISP-level sensors- to provide complete, real-time situational awareness.
- Dark Web Monitoring
- Access to Multiple Data sources.
- Set custom alert rules to notify you
Problem
Understanding the relationships between threat actors, their tools, and infrastructure requires complex, manual analysis, slowing down response and limiting context.
Solution
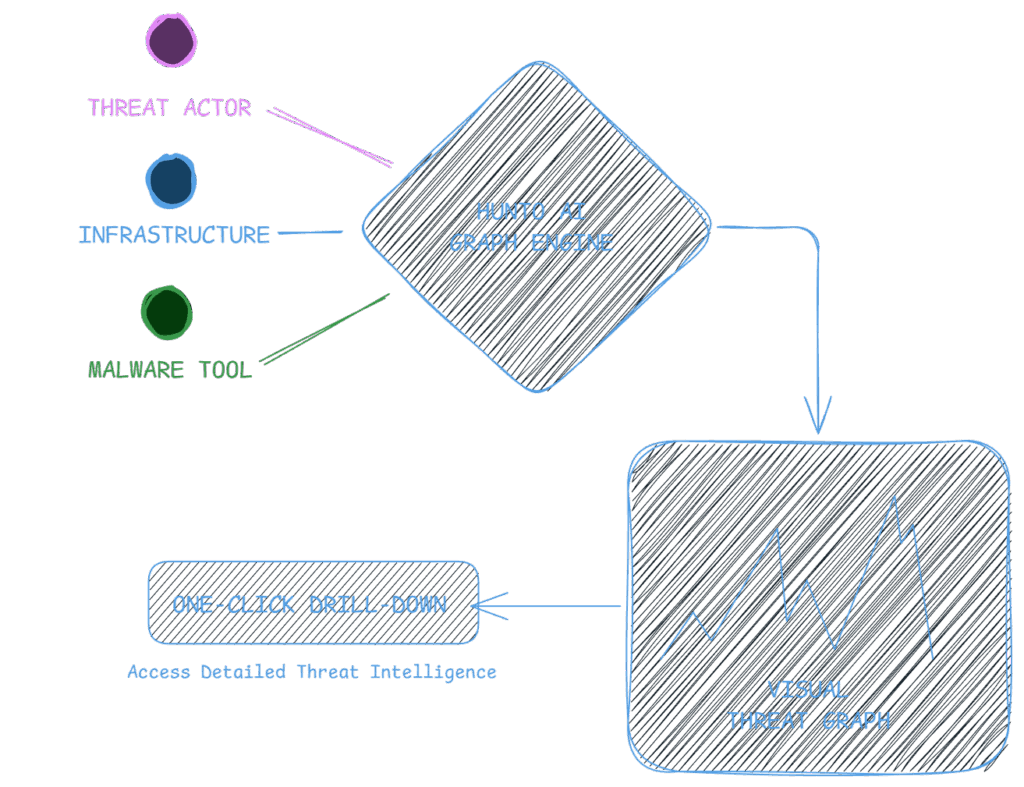
Explore relationships between threat actors, their infrastructure, and tools they employ; all visible at a glance with one-click drill-down into detailed threat intelligence.
- insights into malware behaviors and targeted vulnerabilities
- Malware Analysis and Response
- Drive data-informed strategic decisions.
Problem
Lack of context on attacker methodologies makes it difficult for SOC teams to apply intelligence to specific defensive controls and anticipate future moves.
Solution
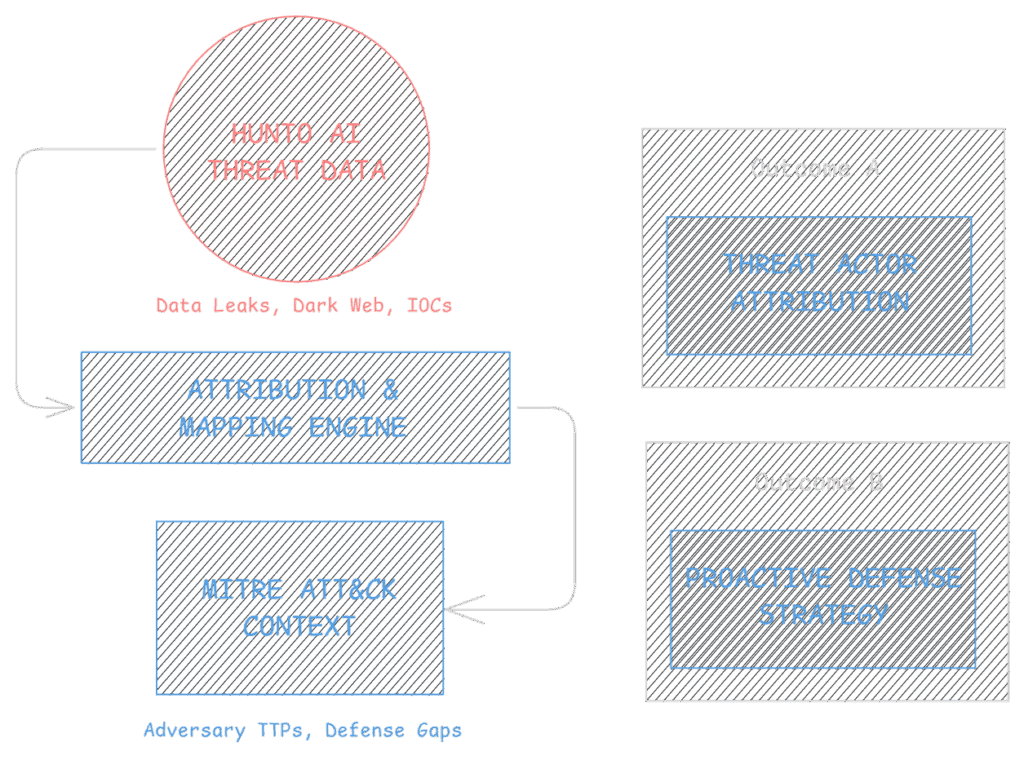
Quickly understand your adversaries’ behaviors, preferred attack methods, and infrastructure with detailed insights automatically aligned with the MITRE ATT&CK framework.
- Visibility into adversary tactics, techniques, and procedures (TTPs).
- Threat Landscape Dashboard
- Detailed visibility of attack stages
Problem
Threat intelligence often remains siloed, requiring manual effort to feed IOCs into existing security tools (SIEM/SOAR), limiting its practical value.
Solution
Enhance your existing security stack effortlessly. Hunto AI integrates out-of-the-box with popular SIEM, SOAR, and TIP solutions, supporting API and STIX/TAXII data exchange to automate workflows.
- Automate Security Workflows
- Reduce False Positives
- Prioritize Patch Management
Measurable Outcomes: Intelligence to Action
Reduced False Positive Rate
Eliminate noise by leveraging a comprehensive database of known and validated Indicators of Compromise (IOCs) tailored to your environment.
Optimized Security Investments
Lower cybersecurity costs by avoiding unnecessary purchases and prioritizing budget based on actual, intelligence-driven threat likelihood.
Accelerated Incident Response (IR)
Benefit from detailed visibility of attack stages mapped to the MITRE ATT&CK matrix, enabling rapid attacker containment and removal from your network.
Key Capabilities
Our Threat Intelligence doesn’t live in a silo. It is the engine that proactively amplifies the effectiveness of every Hunto AI module.
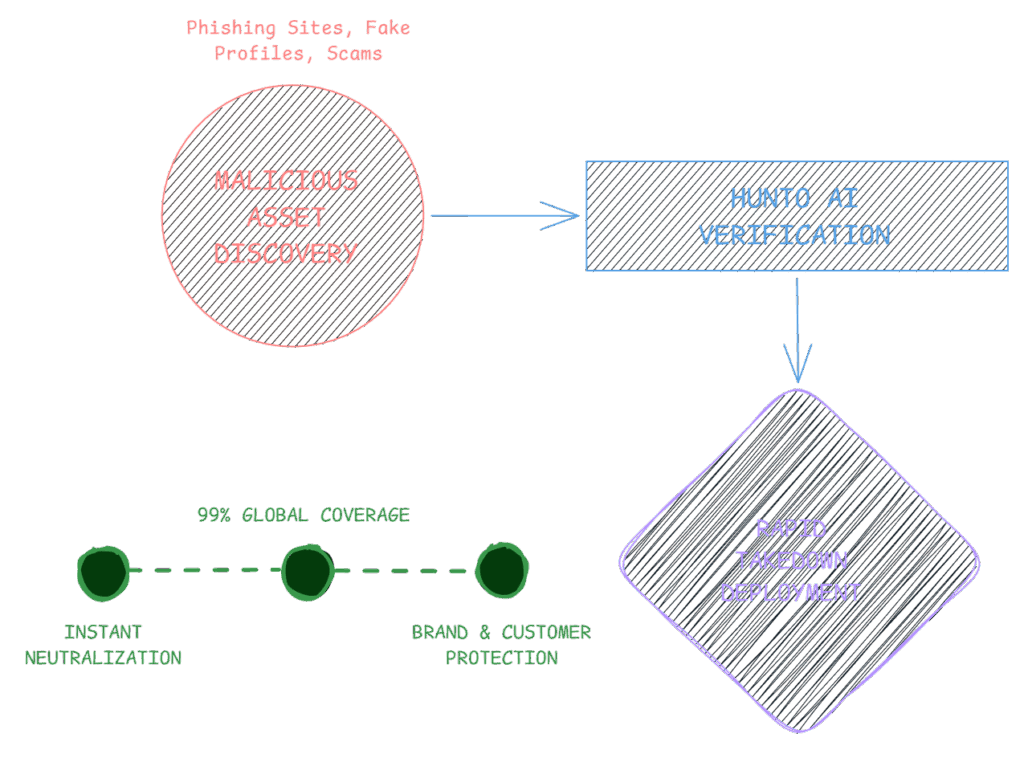
Proactive Brand Defense
TI provides Dark Web and Fraud Infrastructure insights, immediately feeding information on rogue domains and phishing campaigns into our system. This allows for the rapid, preemptive takedown of infrastructure before the attack is launched. Linked Module: Brand Monitoring
Warning

Domain Spoofing Confidence
TI enriches DMARC+ reporting by validating malicious senders attempting to spoof your domain. This intelligence gives our Automated Policy Engine the confidence to move your email security policy safely to the strict ‘reject’ level. Linked Module: DMARC+
Real-World Human Risk Scoring
TI continuously flags employees whose credentials have appeared on Dark Web forums or breach repositories. This critical, real-world data is used to contextualize the Human Risk Number (HRN), allowing for immediate intervention and targeted training. Linked Module: Human Risk
What “Great” Looks Like (Benchmarked Against Leaders)
See how Hunto AI stacks up against top platforms with personalized content, automated campaigns, and real-time risk scoring.
MITRE ATT&CK Mapping
Intelligence is instantly aligned with MITRE ATT&CK, providing contextualized TTPs for faster, data-driven security decisions.
Graphical Threat Investigation
Explore threat actor relationships and infrastructure visually with one-click drill-down, eliminating complex manual data correlation.
Full STIX/TAXII Automation
Seamlessly integrate and automate security workflows across SIEM, SOAR, and TIPs with out-of-the-box API and STIX/TAXII support.
Common Questions
Frequently asked questions
This section answers common questions to help you understand how Hunto AI protects your digital assets and brand against external cyber threats.
It is curated, processed, and analyzed data from multiple sources providing insight into adversary tactics and motivations, enabling proactive cybersecurity decisions.
Hunto AI Threat Intelligence is a cloud service, activated instantly, with expert onboarding for custom configuration and integration.
The solution is modular and flexible, without per-user, integration, or API call charges.
Through Threat Hunting Rules, customizable during onboarding, with ongoing refinement by your team.
Comprehensive sets from open source, malware, data, sensor, human, and vulnerability intelligence collected and correlated by Hunto AI.








