Block Advanced Email-Borne Threats
Secure corporate email- on-premises and in the cloud- from even the most sophisticated attacks, powered by AI-driven analytics and managed by expert security teams.
Start here
Defeating the Evasion Epidemic
Traditional email gateways fail because cybercriminals prioritize evasion tactics at the point of compromise. Hunto AI’s BEP solution was engineered to counter this, leveraging patented technologies and Threat Intelligence to detect, block, and analyze attacks that mimic your corporate environment. We use a customizable detonation platform to defeat evasion, alongside Attachment & Link Analysis for over 290 file types. This integrated approach stops phishing, BEC, and malware and provides Attacker Attribution to ensure true, proactive defense for M365, Google Workspace, and on-premises systems.
File Types Analyzed
Major Email Threats Prevented
Defeat Rate for Evasion Tactics
Deployment Options
Solving Critical Email-Borne Threat Challenges
See how Hunto AI defeats advanced BEC, phishing, and malware attacks using anti-evasion technology and integrated threat intelligence.
Problem
Sophisticated malware and phishing campaigns are designed to detect generic sandboxes and virtual environments, triggering evasion tactics that bypass traditional email security gateways.
Solution
Customize malware detonation environments to mimic your organization’s configuration, defeating evasion tactics and exposing even the most advanced, targeted email-borne threats.
- Payload Detonation
- Anti-Evasion Techniques
- Analyze over 290 file types
Problem
Security teams often block an attack without knowing the actor or methodology, making it impossible to proactively secure against the next stage of the campaign.
Solution
Correlate detonation findings with Threat Intelligence to identify threat actors targeting your organization, providing comprehensive TTPs, network, and file indicators.
- Malware Analysis
- BEC Protection
- Enables Threat Hunting using extracted attack data
Problem
Even after detection, manual quarantine and removal of malicious emails post-delivery is slow and risks exposure to the entire organization.
Solution
Provide comprehensive coverage: stop phishing, BEC, and spoofing attempts pre-delivery, and enable Automated Threat Remediation to rapidly quarantine and remove malicious emails post-delivery.
- Spoofing & Phishing Prevention
- Customizable Security Policies
- Expert Support Services for rapid incident response
Problem
Deploying advanced security often disrupts existing infrastructure, forcing organizations to choose between protection and compatibility with their current email providers.
Solution
Deploy quickly via Flexible SaaS with Seamless Integration for Microsoft 365, Google Workspace, Exchange, and on-premises systems, providing unified threat visibility and reporting.
- Cloud-native
- Users get access to a fully customizable dashboard
- Reports are compliance-ready and aligned with industry frameworks
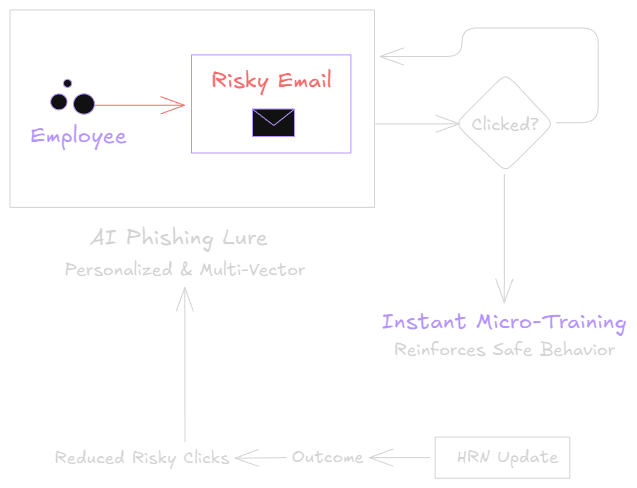
Measurable Outcomes: Intelligence to Action
100% Evasion Tactic Defeat
Successfully identify and block malware designed to avoid detection, utilizing our customizable, anti-evasion detonation platform that mimics your network.
Universal Platform Compatibility
Achieve full email security coverage across Microsoft 365, Google Workspace, and on-premises Exchange without deployment friction or feature limitations.
Rapid Threat Remediation
Leverage Automated Threat Remediation to rapidly quarantine and remove malicious emails post-delivery, significantly reducing employee exposure time.
Key Capabilities
BEP’s unique anti-evasion findings and Attacker Attribution capabilities are seamlessly shared to enrich Threat Intelligence and proactively close external risk vectors across the platform.
Deep Attacker Attribution
BEP uses its customizable detonation platform and malware analysis to uncover attacker TTPs. This rich data is immediately fed back into our Threat Intelligence platform, enhancing global knowledge and strategic defense.
Warning

BEC Threat Hunting & XDR
Data extracted from malicious emails (BEC, phishing) is instantly available via the unified XDR Console. This allows security teams to proactively hunt threats within their network, enabling rapid containment and minimizing dwell time, a core function of Digital Risk Protection
Continuous Policy & Risk Alignment
BEP integrates with your existing email platform (M365/Google) and allows you to tailor security policies to your unique risk profile. Automated remediation and detailed threat visibility (aligned with MITRE ATT&CK) ensures your email posture remains fully compliant and effective.
What “Great” Looks Like (Benchmarked Against Leaders)
See how Hunto AI stacks up against top platforms with personalized content, automated campaigns, and real-time risk scoring.
Anti-Evasion Detonation
Use a customized detonation platform that mimics your corporate environment, defeating evasion tactics and identifying the most advanced, targeted malware.
Attacker Attribution & TTPs
Correlate email findings with Threat Intelligence to quickly attribute attacks and map attacker TTPs, moving beyond simple blocking to proactive defense.
Cloud-Native Deployment & IR
Achieve seamless integration with Microsoft 365, Google Workspace, and Exchange, providing immediate compatibility and enabling rapid, automated post-delivery remediation.
Common Questions
Frequently asked questions
This section answers common questions to help you understand how Hunto AI protects your digital assets and brand against external cyber threats.
Our solution detects phishing, spam, malware, business email compromise, account takeovers, malicious attachments, and advanced evasion techniques to protect your organization comprehensively.
It replicates your corporate environment’s specific language, network routing, and user variables within a virtual environment, evading detection by sophisticated malware designed to avoid generic sandboxes.
Yes, Hunto AI supports seamless integration with popular cloud email providers like Microsoft 365, Google Workspace, and on-premises Exchange servers to quickly deploy protections.
Our system continuously correlates email threat data with global real-time intelligence, providing up-to-date attacker tactics, network indicators, and automated attack attribution.
Users get access to a fully customizable dashboard offering real-time security status, detailed threat analytics, and reports aligned with industry frameworks like MITRE ATT&CK for compliance and response planning.








