Attack Surface Management:
AI-Powered Attack Surface Discovery & Intelligence
Complete external attack surface intelligence — from discovery to remediation Continuous attack surface intelligence with AI-powered discovery, vulnerability mapping, and real-time risk prioritisation. Identify shadow IT, exposed services, and misconfigured assets before attackers do.
Hunto AI delivers next-generation cybersecurity from an attacker's perspective, ensuring complete External Threat Protection across all digital assets using Attack Surface Management. Our journey has been dedicated to setting the gold standard in threat counteraction, leveraging 90+ global partners and AI to perform 15,900+ successful takedowns last year. We are your strategic partner in eradicating threats and elevating security.
Solving External Attack Surface & Blind Spot Challenges
See how Hunto AI addresses your critical human-centric security needs.
Problem
Security teams lack comprehensive visibility into the rapidly expanding external attack surface, leaving Shadow IT, rogue domains, and unknown cloud assets exposed to sophisticated attackers
Solution
Hunto AI continuously identifies and inventories all external digital assets (cloud, mobile, on-premise) from an attacker's perspective, ensuring complete coverage and eliminating critical blind spots.
- Complete asset visibility, including Shadow IT.
- Continuous identification of all threats.
- Automated Drift Detection for instant alerting on system changes.
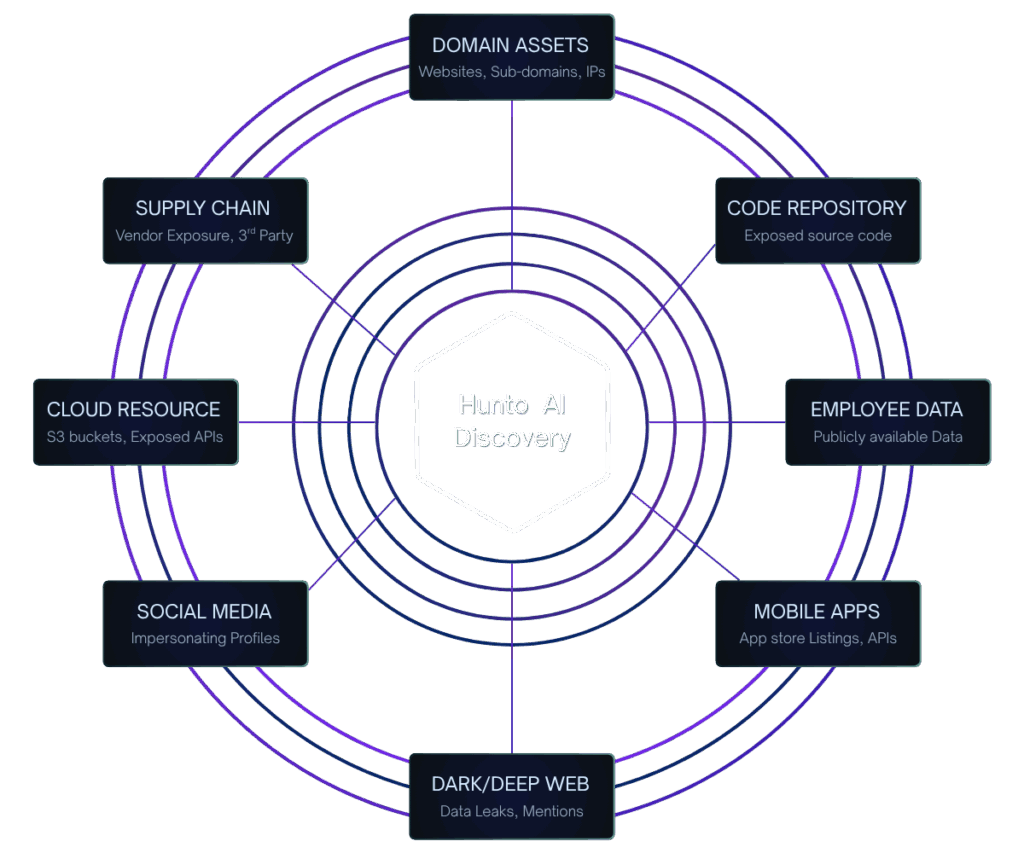
Key Capabilities of Hunto's Attack Surface Management
ASM provides the critical inventory of all external risk. Its continuous discovery and comprehensive vulnerability prioritization are seamlessly amplified by insights from Threat Intelligence and integrated with Digital Risk controls across the entire platform.
Continuous Intelligence-Driven Discovery
ASM's continuous mapping of the external attack surface is guided by real-time indicators of compromise (IOCs) and threat actor TTPs from our Threat Intelligence module. This ensures the discovery engine prioritizes scanning assets currently targeted in the wild.
Learn More
Validate External Risk Remediation
ASM validates the effectiveness of defensive measures by continuously checking known Digital Risk Protection (DRP) targets (e.g., fraudulent domains, fake social media). If a spoofing domain is missed by DRP, ASM identifies it as an unmitigated risk, closing the loop.
Learn More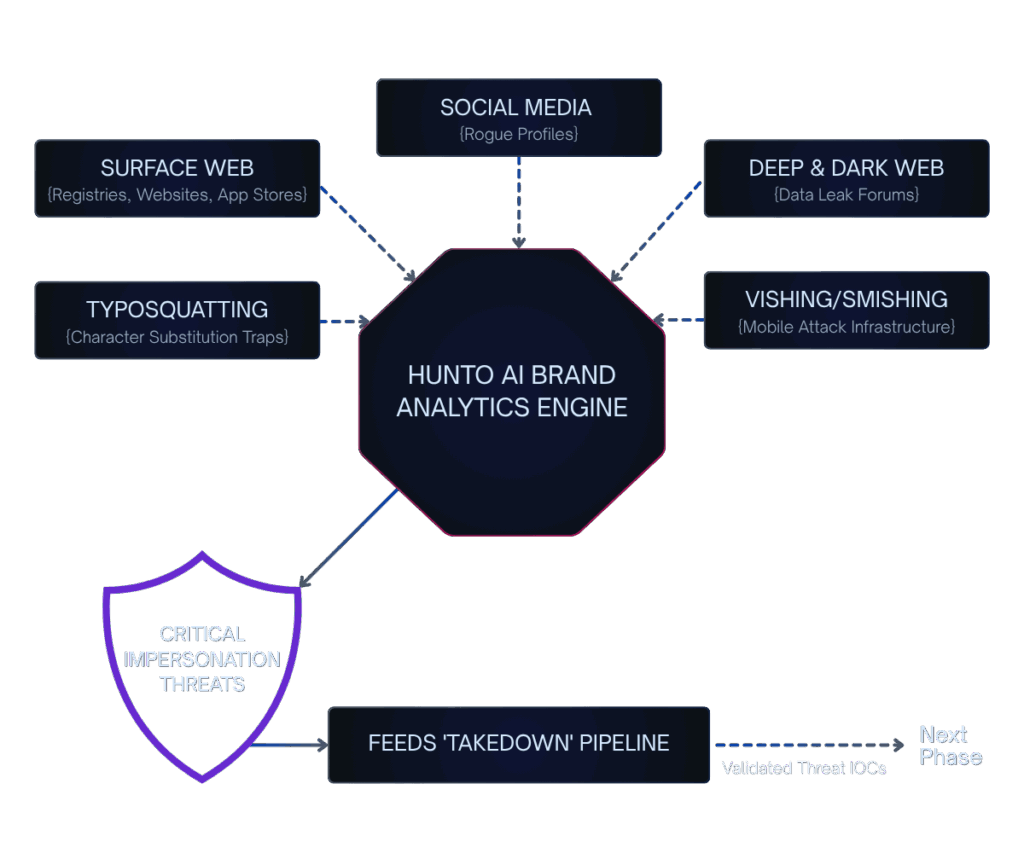
Vulnerability-Aware Human Risk Scoring
ASM's vulnerability prioritization identifies high-risk technical flaws (e.g., misconfigured email server settings, exposed RDP ports). This technical context is used to raise the Human Risk Number (HRN) of owners/teams responsible for those critical assets, driving accountability.
Learn More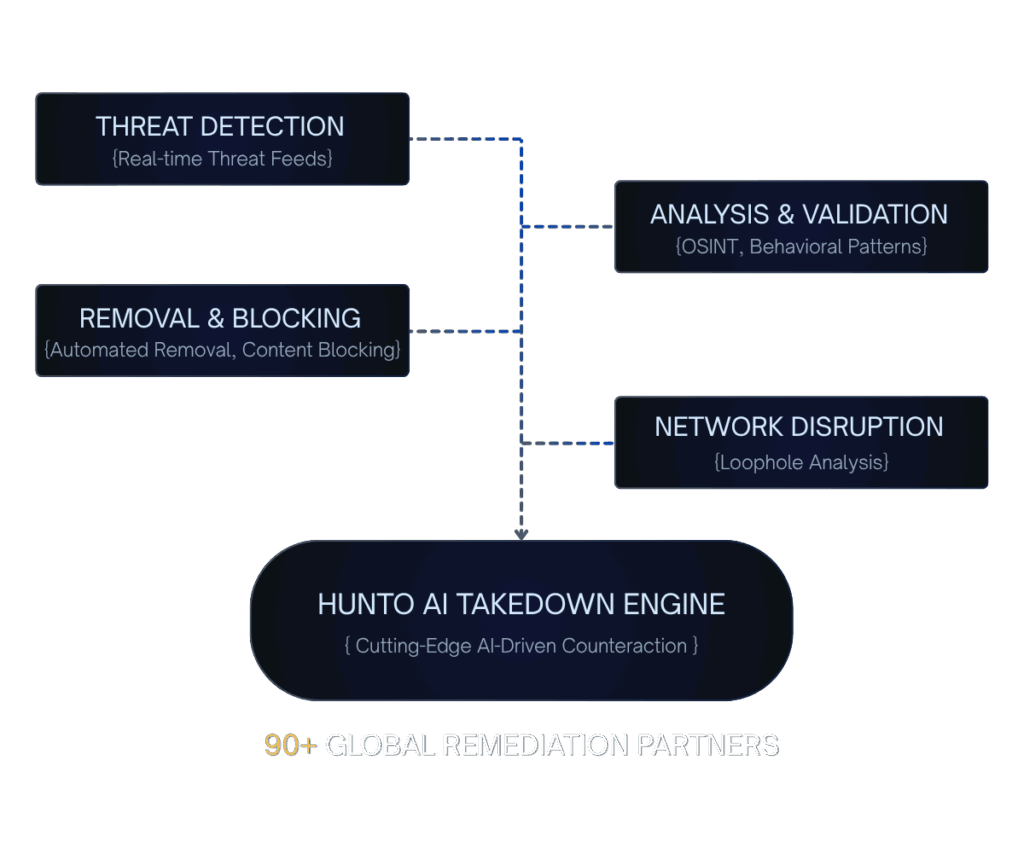
Measurable outcomes in just days.
Complete Asset Visibility
Discover 100% of your external attack surface including shadow IT, forgotten assets, and third-party exposures.
Real-Time Risk Prioritization
AI-powered scoring identifies critical vulnerabilities requiring immediate attention based on exploitability and business impact.
15,900+ Takedowns/Year
Automated threat neutralization removes fraudulent domains, phishing sites, and brand impersonation attempts.
Proactive Brand Risk Intelligence
Prevent attacks before they occur with predictive threat modeling and continuous external monitoring.
Automated Incident Response
Reduce response time from days to minutes with automated workflows and AI-assisted remediation.
Threat Intelligence Enrichment
Enrich vulnerability data with real-time threat intelligence to understand which assets are actively targeted.
What "Great" Looks Like (Built for Zero Trust)
See how Hunto AI secures your digital infrastructure against external threats and asset exposure.
Real-Time Attack Surface Discovery
Continuously identify all external digital assets, including Shadow IT, orphaned systems, exposed services, and forgotten domains across cloud, on-premise, and hybrid environments.
Attack Surface Intelligence Monitoring
Go beyond simple scanning with AI-powered attack surface intelligence that monitors, analyses, and prioritises threats based on real-time exploitation data and threat actor activity.
Multi-Vector Threat Remediation
Address 70+ types of cyber attacks including phishing, typosquatting, vishing, rogue apps, watering hole tactics, and exposed services — all from a single attack surface management platform.
AI-Powered Vulnerability Mapping
Attack surface intelligence mapping provides visual, contextual views of your external risk — showing which assets, services, and vulnerabilities pose the highest risk to your organisation.
Continuous Risk Prioritisation
Advanced algorithms assess vulnerability impact and exploitation likelihood, directing resources to the highest-risk exposures. AI-powered insights eliminate alert fatigue and focus your team.
Threat Intelligence Enrichment
Enrich attack surface intelligence with actionable insights from global threat feeds, IOC correlation, and attribution analysis derived from 1M+ data points analysed daily.
Frequently asked questions
Attack surface intelligence is the process of continuously discovering, mapping, and analysing all external-facing digital assets from an attacker's perspective. It goes beyond simple asset inventory by enriching discovery data with real-time threat intelligence, vulnerability context, and exploitability scoring. Hunto AI's attack surface intelligence platform discovers domains, subdomains, IP addresses, cloud infrastructure, exposed services, APIs, and shadow IT — then prioritises risks based on active threat actor targeting.
AI-powered attack surface discovery uses machine learning to continuously identify and map all internet-facing assets associated with your organisation. Unlike manual or periodic scanning, AI-driven discovery proactively finds shadow IT, forgotten subdomains, misconfigured cloud assets, and third-party exposures in real-time. Our discovery engine analyses DNS records, SSL certificates, WHOIS data, and cloud provider APIs to build a complete external asset inventory — then applies threat intelligence to prioritise the highest-risk exposures.
Hunto AI's ASM discovers all external-facing digital assets including domains, subdomains, IP addresses, cloud infrastructure, SSL certificates, exposed services (RDP, SSH, databases), APIs, mobile apps, social media accounts, and third-party integrations associated with your organisation. Our attack surface intelligence scanning identifies both known and unknown assets — including shadow IT that your security team may not be aware of.
Our AI-powered system analyses vulnerabilities based on multiple factors: exploitability, business impact, active threat intelligence, asset criticality, and exposure level. This contextual attack surface intelligence ensures you focus on the highest-risk issues first — not just the highest CVSS scores. We correlate vulnerability data with real-world threat actor activity to identify which exposed services and vulnerabilities are actively being targeted in the wild.
Hunto AI's attack surface management platform provides AI-powered insights by combining continuous asset discovery with real-time threat intelligence, automated vulnerability prioritisation, and predictive risk scoring. Our AI engine analyses 1M+ data points to identify patterns, predict emerging threats, and recommend remediation actions — going beyond simple vulnerability scanning to deliver actionable attack surface intelligence.
Yes. Hunto AI offers affordable attack surface management designed for small security teams. Our autonomous AI agents handle continuous discovery, vulnerability prioritisation, and drift detection without requiring a large SOC team. Plans scale with your organisation's needs, and the platform is designed to replace multiple point solutions — typically saving 40-60% compared to assembling a separate scanner, EASM tool, and vulnerability management platform.
Yes, Hunto AI integrates seamlessly with your existing security stack including SIEM, SOAR, ticketing systems, and vulnerability management platforms. Our API and webhooks enable automated workflows and bidirectional data sharing. We support STIX/TAXII for threat intelligence sharing and integrate with Splunk, Sentinel, Jira, ServiceNow, and more.
Our automated drift detection continuously monitors your external attack surface for unauthorised changes, misconfigurations, and policy violations. You receive instant alerts when new assets appear, configurations change, or security policies are violated. This is critical for maintaining security posture across cloud infrastructure where misconfigurations are the leading cause of breaches.
Threat intelligence enriches attack surface management by providing context about active threats, attacker TTPs, and IOCs. Our attack surface intelligence monitoring correlates vulnerability data with real-world exploitation attempts, helping prioritise assets that are actively targeted by threat actors. This integration guides the discovery engine to focus on assets currently in the crosshairs of specific threat groups.
Attack surface discovery is the process of finding all external-facing assets — domains, IPs, cloud services, mobile apps, and exposed services. Attack surface intelligence goes further by enriching that inventory with vulnerability data, threat intelligence, exploitability scoring, and business context. Hunto AI delivers both: continuous discovery to maintain complete asset visibility, and intelligence-driven prioritisation to focus your security team on the exposures that matter most.
Explore more modules

Get A Free Demo
Ready to safeguard your organization's digital presence? Choose your plan and start your free trial.