12 Best Automated Phishing Simulation Tools [2026 Guide]
“Monthly Phishing Simulation” is no more effective as your human risk management strategy. In 2026, cybercriminals who perform phishing attacks do not operate on a schedule, and they certainly do not use static phishing templates. We have entered the age of Agentic Threats, where offensive AI agents scrape your employee data, craft hyper personalised lures, and execute campaigns at machine speed.
If your defence strategy relies on manual spreadsheets or legacy tools that require hours of admin work to launch a single campaign, you are already behind. The modern standard is Automated Phishing Simulation. These are “set and forget” platforms that use AI to continuously test, train, and inoculate your workforce against attacks that look and feel real because, in many cases, they are generated by the same AI models attackers use.
At Hunto, we are pioneering the shift to Agentic Security. We believe your defence should be as autonomous as the offence. While we offer the world’s first fully autonomous Phishing Simulation Agent, we believe in helping you find the right tool for your specific maturity level.
Table of Contents
What are Phishing Simulations?
Phishing simulations are controlled exercises used by organisations to educate staff about the dangers of deceptive emails. These programs mimic real world cyber attacks by sending fake phishing attempts to employees. The goal is not to trick people for the sake of it but to build a stronger human firewall.
How Phishing Simulations Work?
Security teams or specialised software providers craft messages that look like legitimate requests from banks, IT departments, or HR. They often include common red flags such as:
- Urgent language demanding immediate action
- Suspicious links that lead to fake login portals
- Unexpected attachments containing harmless tracking files
When an employee interacts with the simulated threat, they are typically redirected to a brief training module. This provides an immediate “teachable moment” that explains what they missed and how to spot similar threats in the future.
Key Benefits of Phishing Simulations for Businesses:
Implementing these exercises offers several strategic advantages for maintaining website and data integrity:
| Feature | Impact on Security |
| Risk Assessment | Identifies which departments or roles are most vulnerable to social engineering. |
| Behavioral Change | Shifts employee habits from clicking instinctively to verifying every request. |
| Compliance | Helps meet regulatory requirements for ongoing security awareness training. |
| Data Metrics | Provides concrete numbers on click rates and reporting accuracy to measure |
What Makes a Phishing Simulation Automated or Agentic ?
Before listing the tools, it is critical to understand the shift from “Automated” to “Agentic.”
- Legacy Automation (2020s): You select a template, upload a CSV of users, schedule the blast, and look at a static report.
- Agentic Automation (2026): The software acts as an autonomous operator. It discovers your employees from public sources, crafts unique payloads using Generative AI, sends them based on user behaviour (e.g., when they are most likely to check email), and provides instant micro training when a user fails.
You need a tool that acts like a resident hacker, not a survey machine.
Top 12 Automated Phishing Simulation Tools
1. Phishing Simulation Agent by Hunto AI
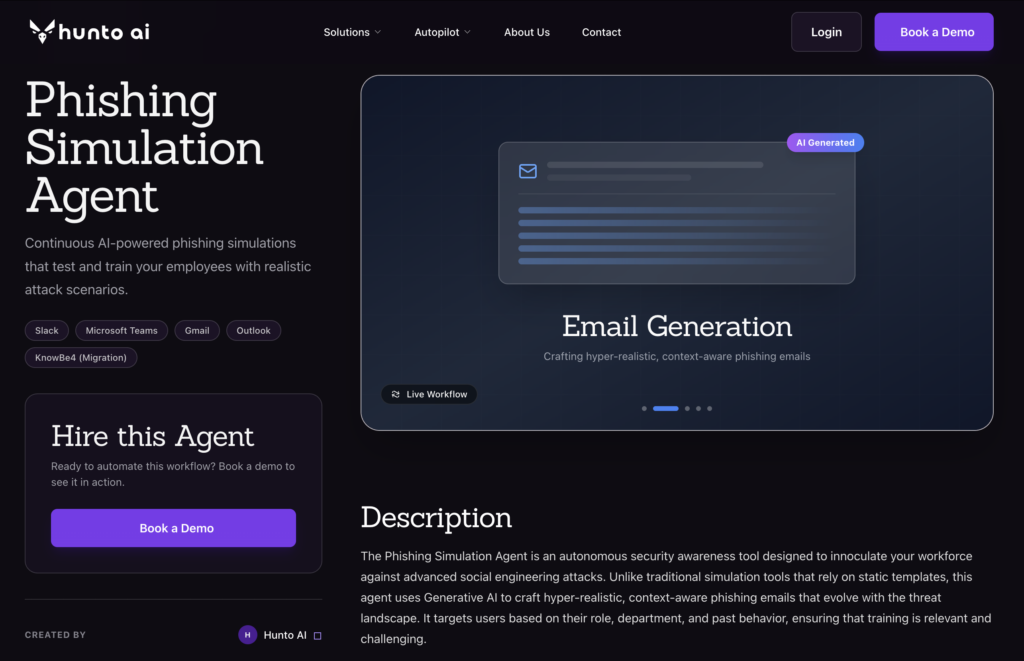
Best For: Organizations seeking fully autonomous, “zero touch” human risk management.
Hunto is not just a simulation tool; it is an Agentic Cybersecurity Platform. Its phishing simulation agent is designed to completely remove the administrative burden from the security team while delivering the most realistic email phishing simulations in the market.
Key Features:
- Generative AI Payloads: Hunto does not rely on a static library. The agent scans your organisation’s digital footprint (news, LinkedIn, tech stack) to generate context aware phishing attacks that mimic highly sophisticated phishing. The agent automatically scans your organisation’s activities, employees, employee social profiles, and comes up with personalised attacks instead of generic templates.
- Autonomous Lifecycle: From reconnaissance to reporting, the entire loop is automated. The agent identifies high risk users and adjusts the difficulty level dynamically. If a user is savvy, the agent tries harder. If a user is struggling, the agent provides remedial education.
- Human Risk Number (HRN): Hunto provides a unified HRN that updates in real time based on simulation results and real world security behaviours, giving the Board a clear metric of improvement.
- External Integration: It integrates with Hunto Autopilot to correlate phishing results with other risks like dark web exposures or brand impersonations.
2. Hoxhunt
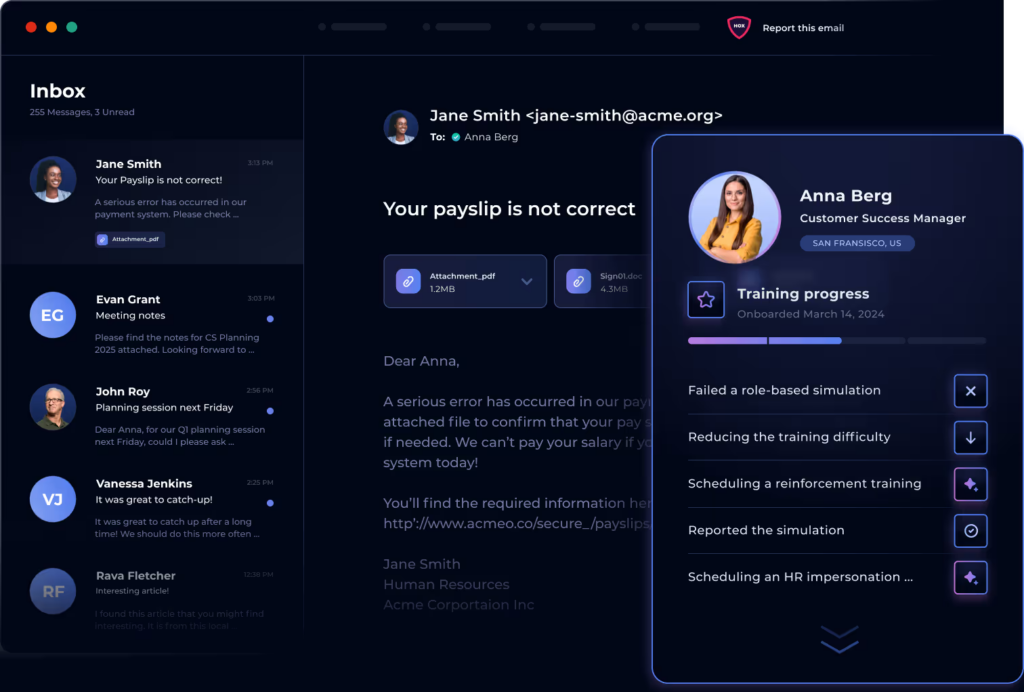
Best For: Driving behavioural change through gamification.
Hoxhunt has carved a niche by focusing intensely on the employee experience. Rather than tricking users, it positions security as a game. Their “Human Risk Management” platform uses an AI enabled engine to deliver personalised simulations that feel native to the user’s workflow.
Why it works:
- Gamified Reporting: Users are rewarded for reporting threats, creating a positive feedback loop.
- Adaptive Learning: The platform analyses user behaviour to serve simulations at the edge of their skill level, ensuring they are challenged but not frustrated.
- Global Operations: Strong support for multi language deployments makes it a favourite for global enterprises.
3. Phished.io
Best For: Automated, hands off content generation.
Phished.io was one of the early adopters of AI driven content. Their platform emphasises “zero manual intervention.” The AI analyses threat trends daily to create new templates that mirror active campaigns in the wild.
Why it works:
- Smart Scheduling: It determines the optimal time to send an email to a specific user to maximise the chance of engagement.
- Checklist Free: There are no complex wizards to follow; the AI handles the campaign strategy based on the risk profile you define.
4. KnowBe4 (HRM+)
Best For: Content variety and compliance heavy industries.
As the market share leader, KnowBe4 offers the deepest library of training content in the industry. Their evolved HRM+ platform attempts to bridge the gap between their legacy training modules and modern behavioural data.
Why it works:
- Massive Library: Thousands of templates and training videos, including high production value series that keep users entertained.
- SmartGroups: Allows for granular targeting of user groups based on behaviour, location, or role.
- Brand Recognition: A safe choice for auditors and compliance officers who look for established names.
5. Proofpoint Security Awareness
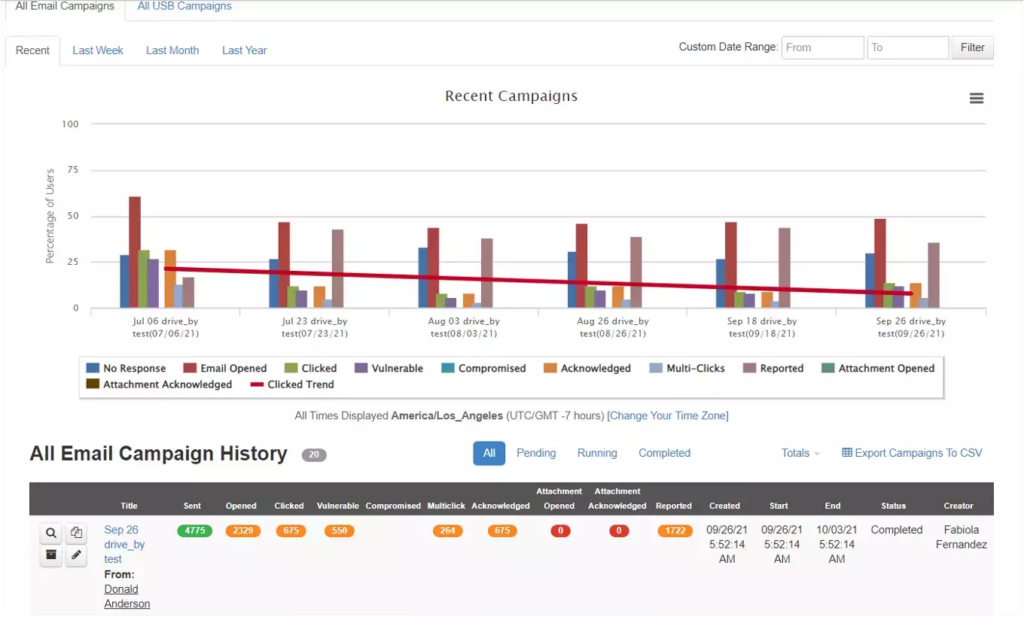
Best For: Threat intelligence driven simulations.
Proofpoint leverages its dominance in the email gateway market (SEG) to fuel its simulations. Because they see a vast amount of the world’s email traffic, they can turn real attacks blocked by their gateway into simulations instantly.
Why it works:
- VAP (Very Attacked People): Identifies and targets training toward the specific individuals in your company who are being targeted by real attackers.
- Attack Spotlight: Turns trending global threats into training modules in near real time.
6. Cofense (formerly PhishMe)
Best For: Integrating simulations with the SOC.
Cofense focuses on “conditioning” rather than just training. Their unique value proposition is the integration between simulation and the Security Operations Center (SOC). They view employees as human sensors who can report active threats.
Why it works:
- PDC (Phishing Defense Center): Validates user reported emails to separate real threats from simulations.
- Incident Response: Feeds reported phishing simulations directly into the incident response workflow, training the SOC team alongside the general staff.
7. Ironscales
Best For: Integrated email security and simulation.
Ironscales combines protection and training in a single platform. It uses AI to detect anomalies in the inbox and uses that same intelligence to craft simulations.
Why it works:
- Themis Co Pilot: An AI assistant that helps classify threats and suggests simulation scenarios.
- Seamless Feedback: Users report phishing directly inside Outlook/Gmail, and the platform instantly analyses the message.
8. Arctic Wolf Managed Security Awareness
Best For: Organizations that want to outsource the entire process.
Arctic Wolf offers a “Concierge Security” model. Instead of giving you a tool, they give you a service. Their team manages the campaigns, analyses the data, and provides the reports.
Why it works:
- Microlearning: Focuses on short, digestible content sessions (often <3 minutes) to maintain attention.
- Zero Admin: Ideal for lean IT teams that do not have the bandwidth to manage a simulation tool.
9. Mimecast Engage
Best For: High quality, humorous training content.
Mimecast (formerly Ataata) is famous for realising that boring training gets ignored. Their content uses humour and “sitcom style” videos to engage users, aiming to reduce the “eye roll” factor of security training.
Why it works:
- Watchability: Content that employees actually discuss at the water cooler.
- CyberGraph: Graphs the relationship between users and external senders to customise risk scores.
10. Sophos Phish Threat
Best For: Existing Sophos Central users.
If you are already in the Sophos ecosystem for firewalls or endpoint protection, Phish Threat is a logical addition. It is managed from the same “Sophos Central” dashboard, allowing for consolidated reporting.
Why it works:
- Unified Console: Manage endpoint, network, and email security training in one tab.
- Synchronised Security: Can correlate a user’s simulation failure with their endpoint health status.
11. Infosec IQ
Best For: Deep customisation and role based education.
Infosec IQ offers robust features for organisations that want to tailor training to specific roles (e.g., developers vs. HR). It provides granular control over the simulation templates and the educational landing pages.
Why it works:
- Workforce Scoring: Measures the “security culture” of the organisation, not just click rates.
- Need to Know: Delivers specialised modules for compliance standards like HIPAA, PCI DSS, and GDPR.
12. PhishGrid
Best For: Flexible, API driven simulation and learning.
PhishGrid focuses on the intersection of simulation and interactive learning. It is designed to analyse an environment’s maturity and offers a more modular approach to training, often utilised by service providers.
Why it works:
- Real Time Simulation: Emphasises the immediacy of feedback loops during the simulation process.
- Comprehensive Reporting: Provides detailed analytics that allow teams to drill down into specific departmental vulnerabilities.
Comparison of Top Features:
| Feature | Hunto.ai | KnowBe4 | Hoxhunt | Proofpoint |
| Primary Focus | Autonomous Agent | Content Library | Behavioral/Gamified | Threat Intel |
| AI Payload Gen | Native Generative | Limited | High | Template based |
| Admin Effort | Zero Touch | Medium | Low | Medium |
| Risk Metric | Human Risk Number | Phish-prone % | Engagement Score | VAP Score |
| Best For | Modern / Lean SOC | Compliance | Culture Building | Enterprise |
Why “Template Based” Phishing is Dead?
In the past, running a phishing simulation meant selecting a “Reset Password” template from a library and sending it to everyone. In 2026, this is ineffective for two reasons:
- Polymorphism: Real attackers use AI to change the wording, subject, and sender of every email. A static template does not prepare users for this variety.
- Context: A generic “Package Delivery” email is easy to spot. An email referencing a specific LinkedIn post you made yesterday about a conference in Vegas is terrifyingly effective.
Tools like Hunto.ai and Phished.io use OSINT (Open Source Intelligence) to gather public data and craft lures that act like real spear phishing. This “Red Teaming as a Service” approach is the only way to measure actual risk.
FAQs:
Do I really need AI for phishing simulations?
Yes. Attackers are using AI to write perfect English and generate code. If your defence tool is using static templates from 2023, you are training your employees to spot “dumb” attacks while leaving them vulnerable to smart ones.
How often should I run phishing simulations?
Continuous is best. The “monthly blast” creates a “water cooler effect” where employees warn each other. Autonomous agents like Hunto Autopilot trickle simulations continuously, ensuring that different users are tested at different times, mirroring real attack patterns.
Can these tools simulate deepfakes?
Leading tools are beginning to incorporate “vishing” (voice phishing) and deepfake elements. Hunto and Proofpoint are at the forefront of multimodel threat simulation, preparing users for attacks that happen outside the inbox.
What is the best metric to track?
Stop tracking “Click Rate” alone. It is a vanity metric. Focus on Reporting Rate (how many people reported the phish) and Mean Time to Report. A low click rate means nothing if no one tells the SOC that an attack is in progress.
How do I get started with Hunto’s phishing simulation agent?
You can deploy Hunto’s phishing simulation agent in minutes. It integrates with Google Workspace and Microsoft 365 to start mapping your human risk profile immediately. Check out our Customers page to see how other organisations are automating their human defence.
Conclusion
The goal of phishing simulation is not to trick employees; it is to build a reflexive muscle memory for threat detection. In 2026, that requires tools that are as dynamic and intelligent as the threats themselves. Whether you choose the massive library of KnowBe4, the gamification of Hoxhunt, or the autonomous precision of Hunto.ai, the key is to start now.
The adversary is automated. Your defence must be too.
