Cybersecurity
Cybersecurity Articles
10 articles in Cybersecurity
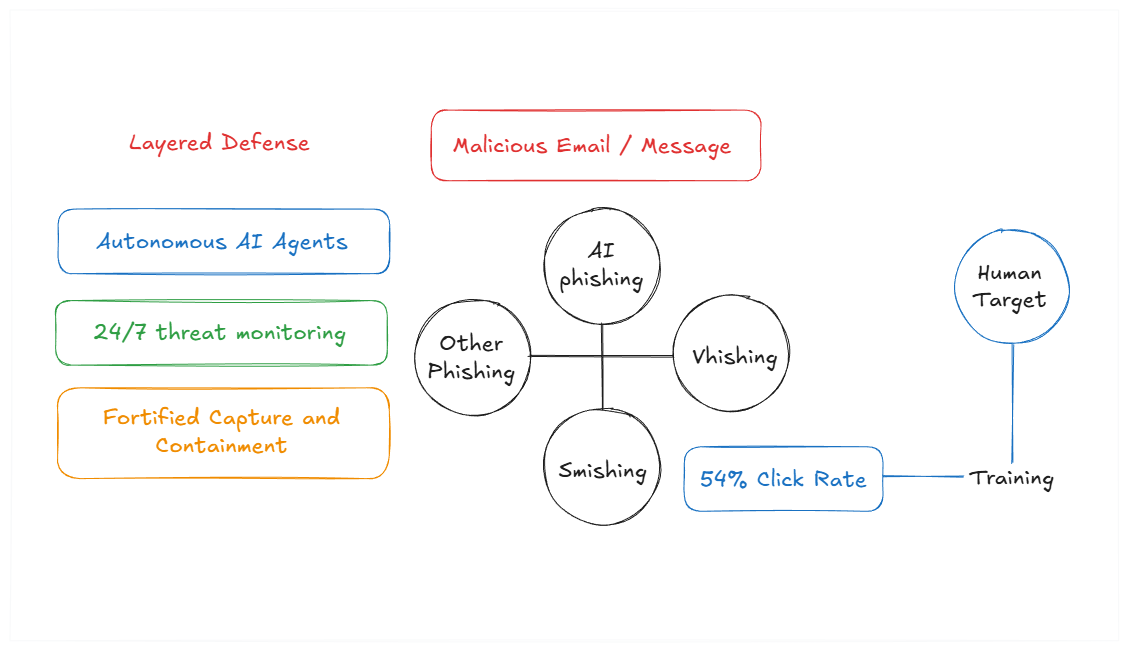
60+ Phishing Attack Statistics: Insights for 2026
Phishing continues to be one of the most pervasive and damaging cyber threats facing organizations globally. Attackers aren’t standing still; they’re […]
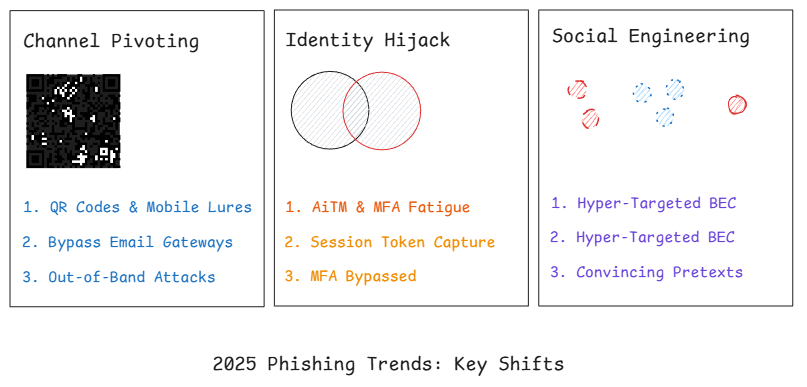
Phishing Trends 2025: What’s Really Changing, What Still Works, and How to Measure Progress
Executive Summary: Defining the 2025 Phishing Trends Phishing in 2025 isn’t a single tactic; it’s a portfolio of low-friction, high-yield techniques
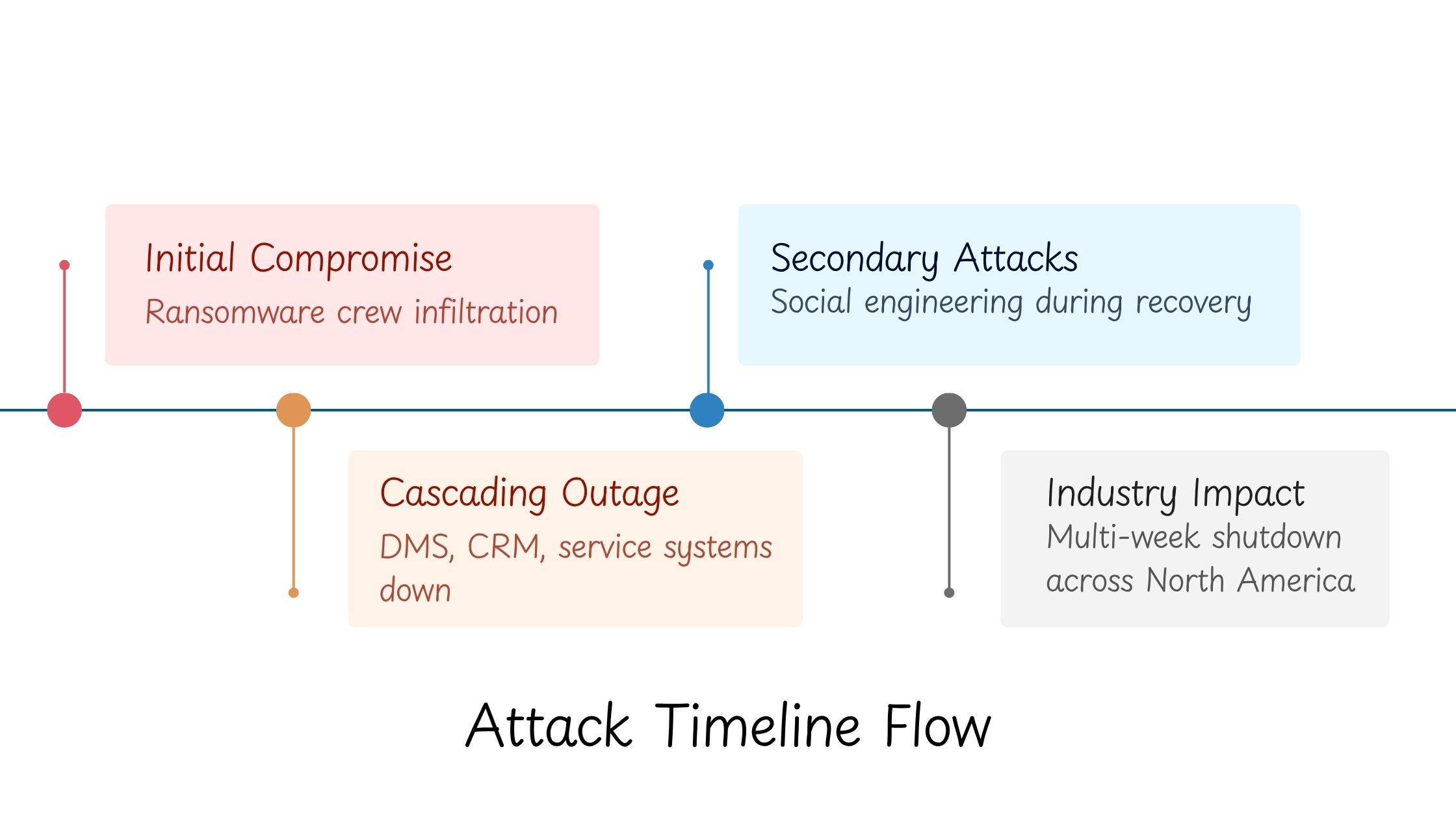
CDK Global Cyber Attack – What Happened And How to Mitigate
If you work anywhere near automotive retail, the June 2024 CDK Global Cyber Attack didn’t read like news, it felt like […]
The Ultimate 2025 Guide to AI in Cybersecurity: Deploying Autonomous Agentic Defense
AI in Cybersecurity has evolved past simple threat detection. Most guides stop there, but the meaningful distinction now is not AI […]
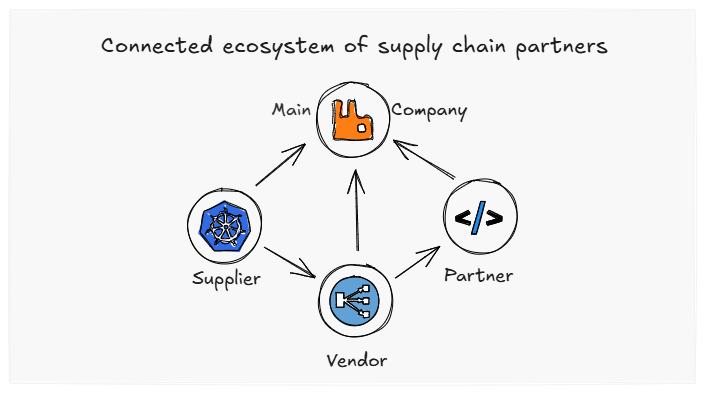
Supply Chain Attacks: The Essential 2025 Guide to Unstoppable Defense
Cybersecurity isn’t about protecting just one company. It’s about keeping an entire web of relationships safe; including suppliers, partners, and vendors [&hell
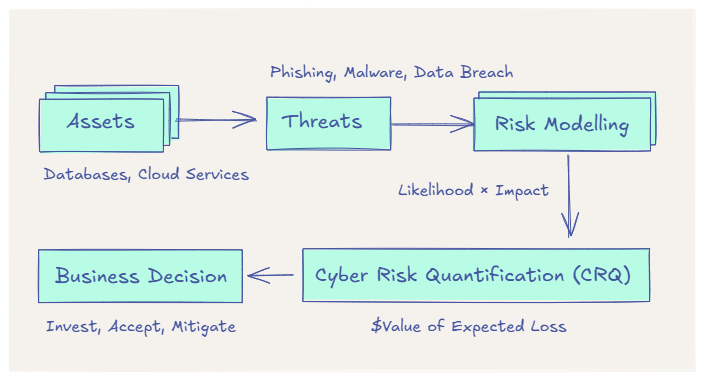
Cyber Risk Quantification (CRQ): 7 Essential Steps to Master Financial Risk
What is Risk Modelling? Cyber Risk Quantification (CRQ) is a way to quantify uncertainty, used across scenarios from being late to […]
Celebrating Safer Internet Day
Safer Internet Day (SID) Safer Internet Day (SID) 2024, observed on February 6, is a significant global event aimed at promoting […]
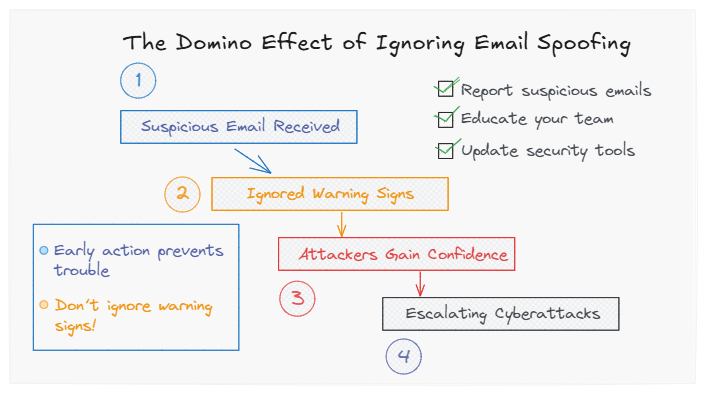
Stop 5 Dangerous Email Spoofing Attacks with DMARC
The Domino Effect of Ignoring Email Spoofing Email spoofing and phishing attacks have become smarter and more common than ever. When […]
O365 – Easy Guide to Add DMARC
What is DMARC in O365? Microsoft’s Office 365 (O365) supports DMARC (Domain-based Message Authentication, Reporting, and Conformance), an email authentication p
Showing 1-10 of 10 posts