What is SIEM? 5 SIEM Tools and 10 Core Features (2026 Guide)
Security breaches are happening every 39 seconds. That’s not just a statistic—it’s a wake-up call for every organisation handling digital assets. While traditional security measures focus on building walls, modern threats slip through gaps you didn’t even know existed. This is where Security Information and Event Management (SIEM) becomes your organization’s central nervous system for threat detection.
SIEM systems have evolved from simple log collectors into sophisticated platforms powered by artificial intelligence and machine learning. But what exactly makes SIEM essential in 2026, and how do you choose the right solution for your security operations center?
This comprehensive guide breaks down everything you need to know about SIEM technology, from core capabilities to implementation strategies. Whether you’re a CISO evaluating tools or a security analyst looking to sharpen your skills, you’ll find actionable insights backed by real-world data.
Modern security teams are also leveraging cybersecurity AI agents to automate routine SIEM tasks, reducing response times from hours to minutes. Platforms like Hunto AI are transforming how organizations handle security event analysis by combining SIEM data with autonomous decision-making capabilities.
Understanding SIEM: The Foundation of Modern Security Operations
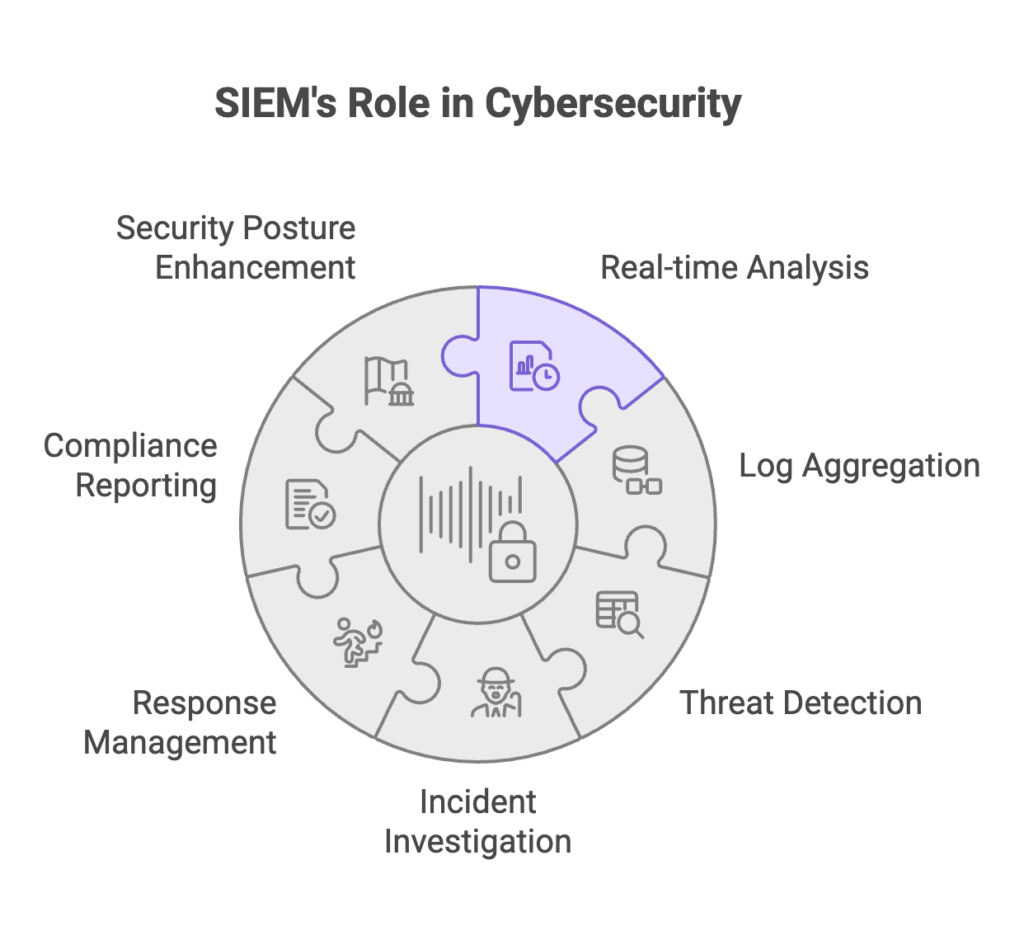
Security Information and Event Management (SIEM) is a comprehensive security solution that combines two critical functions: Security Information Management (SIM) and Security Event Management (SEM). At its core, SIEM aggregates log data from across your entire IT infrastructure, analyzes patterns in real time, and identifies potential security threats before they escalate into breaches.
Think of SIEM as your security command center. It collects data from firewalls, servers, databases, applications, and endpoints, then normalizes this information into a unified format. This centralized approach gives security teams complete visibility into what’s happening across their network at any given moment.
How SIEM Technology Works
The operational flow of a SIEM system follows a structured pattern:
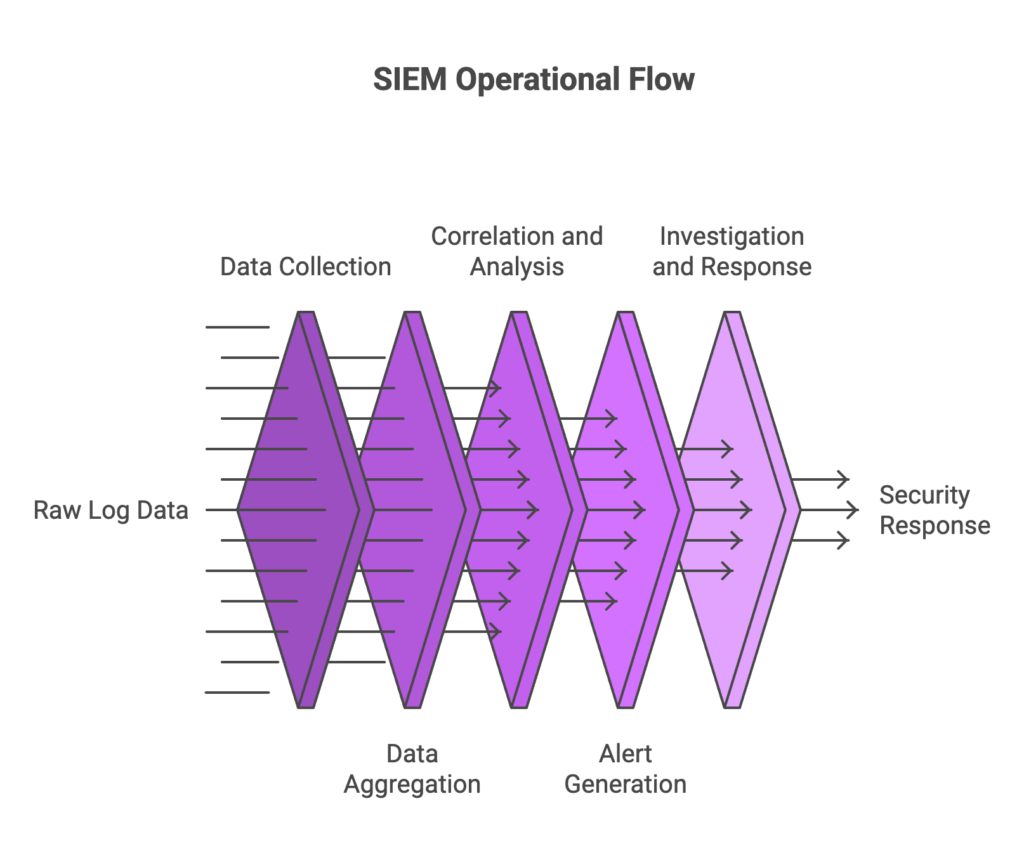
Data Collection: SIEM platforms gather log data and event information from multiple sources including network devices, security tools, applications, and user activity logs. This happens continuously, creating a comprehensive data stream.
Data Aggregation and Normalization: Raw logs arrive in different formats. SIEM normalizes this data into a consistent structure, making it possible to correlate events from different sources. A login attempt from a Windows server and a firewall alert can now be analyzed together.
Correlation and Analysis: This is where SIEM shows its power. The system applies correlation rules to identify patterns that indicate security threats. For example, multiple failed login attempts followed by a successful login from an unusual location triggers an alert.
Alert Generation: When the system detects suspicious activity matching predefined rules or behavioral baselines, it generates alerts prioritized by severity. Security analysts receive notifications about high-priority threats requiring immediate attention.
Investigation and Response: Security teams use SIEM dashboards to investigate alerts, trace the timeline of events, and determine appropriate responses. Modern SIEM platforms include workflow tools to coordinate response activities.
According to the IBM Security Cost of a Data Breach Report 2024, organizations using security AI and automation extensively saved an average of $2.22 million compared to those not using these technologies. SIEM systems serve as the foundation for these automated security operations.
The Evolution of SIEM: From Log Management to AI-Driven Security
SIEM technology has transformed dramatically since its inception in the early 2000s. Understanding this evolution helps explain why modern SIEM platforms function so differently from their predecessors.
First Generation (2000s): Early SIEM systems focused primarily on compliance reporting. They collected logs and generated reports to satisfy regulatory requirements like HIPAA and PCI-DSS. Analysis was mostly manual, and alert fatigue plagued security teams.
Second Generation (2010s): SIEM vendors added real-time monitoring and correlation capabilities. Integration with threat intelligence feeds became standard. However, these systems still required significant manual tuning and produced high volumes of false positives.
Third Generation (2020s-Present): Modern SIEM platforms incorporate artificial intelligence, machine learning, and behavioral analytics. They can detect unknown threats, reduce false positives, and automate response actions. Cloud-native architectures support hybrid and multi-cloud environments.
The current generation of SIEM technology integrates seamlessly with Security Orchestration, Automation, and Response (SOAR) platforms. This combination enables security teams to automate repetitive tasks and focus on strategic threat hunting.
10 Core Features of SIEM Systems in 2026
Modern SIEM platforms offer a robust set of capabilities designed to address sophisticated threat landscapes. Here are the ten essential features you should expect from any enterprise-grade SIEM solution:
1. Real-Time Event Correlation
SIEM systems analyze multiple data streams simultaneously, connecting seemingly unrelated events to identify complex attack patterns. A single failed login might be harmless, but when correlated with unusual network traffic from the same user account, it becomes a red flag.
Real-time correlation enables security teams to detect multi-stage attacks as they unfold. According to Gartner research, organizations that implement real-time correlation capabilities detect breaches 48% faster than those relying on periodic log reviews.
2. Advanced Threat Detection
Modern SIEM platforms use multiple detection methods including signature-based detection, anomaly detection, and behavioral analytics. Machine learning algorithms establish baselines of normal behavior and flag deviations that might indicate compromise.
Advanced threat detection goes beyond known attack patterns. User and Entity Behavior Analytics (UEBA) capabilities identify insider threats and account compromises by recognizing when user behavior diverges from established patterns.
3. Comprehensive Log Management
SIEM systems must collect, store, and index massive volumes of log data from diverse sources. Effective log management includes automated collection, long-term retention for compliance, and rapid search capabilities.
In 2026, leading SIEM platforms process petabytes of data daily. They use intelligent data tiering, storing hot data for immediate access while archiving historical logs to cost-effective storage solutions.
4. Automated Incident Response
Integration with SOAR platforms enables SIEM systems to execute automated response actions. When specific conditions are met, the system can isolate compromised endpoints, block malicious IP addresses, or disable user accounts without human intervention.
Automated response dramatically reduces dwell time. The Ponemon Institute reports that organizations with automated incident response capabilities contain breaches in an average of 74 days compared to 108 days for those using manual processes.
5. Threat Intelligence Integration
SIEM platforms consume threat intelligence feeds from multiple sources, enriching alert data with context about known threats, malicious IP addresses, and attack techniques. This integration helps prioritize alerts and accelerate investigation.
Threat intelligence turns raw indicators into actionable insights. When your SIEM detects traffic to an IP address recently linked to ransomware campaigns, analysts immediately understand the severity.
6. Compliance Reporting and Audit Support
Regulatory compliance remains a primary driver for SIEM adoption. Modern platforms include pre-built report templates for standards like GDPR, HIPAA, PCI-DSS, SOC 2, and ISO 27001. These reports demonstrate security controls to auditors and regulators.
Automated compliance reporting saves hundreds of hours during audit season. SIEM systems maintain comprehensive audit trails showing who accessed what data, when, and from where.
7. User and Entity Behavior Analytics (UEBA)
UEBA capabilities analyze patterns in user activity and entity behavior to detect anomalies that might indicate compromised accounts or insider threats. Machine learning models build profiles for each user and device, flagging unusual access patterns or data movements.
A user who typically accesses files during business hours suddenly downloading gigabytes of sensitive data at 2 AM triggers UEBA alerts. This capability is crucial for detecting threats that bypass perimeter defenses.
8. Cloud and Hybrid Environment Support
As organizations adopt cloud infrastructure, SIEM systems must monitor hybrid environments seamlessly. Modern platforms provide native integrations with AWS, Azure, Google Cloud Platform, and SaaS applications.
Cloud-native SIEM solutions offer elastic scalability, growing and shrinking with your data volumes. This flexibility eliminates capacity planning challenges and controls costs.
9. Network Traffic Analysis
Deep packet inspection and network flow analysis help SIEM systems detect malicious activity at the network level. By analyzing traffic patterns, protocols, and data volumes, these systems identify command-and-control communications, data exfiltration, and lateral movement.
Network visibility complements endpoint and application monitoring, providing a complete picture of your security posture.
10. Customizable Dashboards and Visualization
Security teams need to understand complex data quickly. Modern SIEM platforms offer customizable dashboards that visualize threat landscapes, alert trends, and compliance status. Interactive visualizations help analysts identify patterns and communicate findings to stakeholders.
Effective visualization transforms data into decisions. A well-designed dashboard shows your CISO the security posture at a glance while giving analysts the granular details they need for investigation.
6 SIEM Tools for 2026
Choosing the right SIEM platform depends on your organization’s size, infrastructure complexity, compliance requirements, and budget. Here are five solutions that consistently rank among the best in 2026:
1. Hunto Autopilot
Hunto Autopilot applies AI-driven agents to modern SIEM workflows by automating log correlation, anomaly detection, alert triage, and guided response across security telemetry. Using Hunto AI, organizations can build and deploy custom SIEM agents tailored to their data and threat models—reducing alert noise, accelerating investigations, and enabling explainable, human-in-the-loop security automation at scale.
Key strengths
- Faster analyst workflows: Automates routine triage and repetitive enrichment, freeing SOC analysts for high-value investigations.
- Context-rich decisions: Correlation + enrichment reduces false positives and gives clear evidence chains.
- Modular & flexible agents: Microservice-style agents let teams pick only the capabilities they need and iterate quickly.
- Built-in feedback loop: Analyst corrections feed model retraining to continuously improve detection quality.
- Compliance-friendly audit trail: Decision logs, feature importance, and actions are recorded for forensic and regulatory review.
Best for:
- Mid-to-large SOCs that need to scale triage and reduce noise while keeping human oversight.
- Organizations with multiple telemetry sources (cloud, endpoint, network) needing cross-correlation.
- Teams aiming to operationalize hunting at scale but lacking mature ML pipelines.
- Security teams that require explainability and auditability for model-based decisions.
Considerations / risks:
- Data quality & labeling: Models need clean, well-mapped telemetry and some labeled incidents; poor data yields poor models.
- False positives / alert tuning: Initial models may trigger too many alerts — expect an iterative tuning phase with human-in-the-loop review.
- Model drift & maintenance: Threat landscape and normal behavior change — continuous monitoring and retraining are required.
- Integration complexity: Deep integration with identity stores, SOAR, and on-prem devices can take engineering effort.
- Privacy & compliance: Enrichment or model training using PII or regulated telemetry must be handled per policy (masking, retention rules).
- Operational cost: Real-time feature stores, model inference at scale, and orchestration introduce compute and maintenance costs.
2. Splunk Enterprise Security
Splunk remains the market leader with its powerful analytics engine and extensive ecosystem of integrations. Splunk Enterprise Security excels at processing massive data volumes and offers advanced correlation capabilities.
Key Strengths:
- Exceptional search and investigation capabilities
- Robust app marketplace with hundreds of integrations
- Strong community support and extensive documentation
- Advanced machine learning features through MLTK
Best For: Large enterprises with complex environments and dedicated security operations centers
Considerations: Higher cost of ownership compared to alternatives; requires significant resources for deployment and maintenance
3. Microsoft Sentinel
As a cloud-native SIEM solution, Microsoft Sentinel integrates seamlessly with Azure and Microsoft 365 environments. Its consumption-based pricing model offers flexibility for organizations of varying sizes.
Key Strengths:
- Native integration with Microsoft ecosystem
- Built-in AI and automation capabilities
- Flexible pricing based on data ingestion
- Low barrier to entry for Microsoft customers
Best For: Organizations heavily invested in Microsoft technologies; mid-sized to large enterprises seeking cloud-native solutions
Considerations: May require additional integrations for non-Microsoft environments; effectiveness depends on Azure adoption
4. IBM QRadar
QRadar combines SIEM functionality with extended detection and response (XDR) capabilities. Its flow-based architecture provides efficient network traffic analysis without requiring full packet capture.
Key Strengths:
- Efficient data processing using flow-based analysis
- Strong out-of-the-box correlation rules
- Comprehensive compliance reporting templates
- On-premises, cloud, and hybrid deployment options
Best For: Organizations with stringent compliance requirements; enterprises seeking unified SIEM and XDR capabilities
Considerations: User interface less intuitive than some competitors; learning curve for advanced features
5. Elastic Security (Elastic SIEM)
Built on the Elastic Stack, Elastic Security offers open-source foundations with enterprise features. Its unified search, analytics, and visualization capabilities make it popular among technically sophisticated teams.
Key Strengths:
- Open-source core with commercial features available
- Exceptional search speed and flexibility
- Strong integration with DevOps toolchains
- Cost-effective for organizations with technical expertise
Best For: Mid-sized organizations with strong technical teams; companies seeking open-source flexibility
Considerations: Requires more hands-on configuration than turnkey solutions; support depends on licensing tier
6. Palo Alto Networks Cortex XSIAM
Cortex XSIAM represents the next evolution of SIEM, combining security information management with autonomous threat detection and response. Its AI-driven approach minimizes manual analysis.
Key Strengths:
- Autonomous investigation and response capabilities
- Integration with Palo Alto’s security ecosystem
- Advanced AI-driven threat detection
- Reduced alert fatigue through intelligent prioritization
Best For: Organizations seeking cutting-edge automation; enterprises with Palo Alto Networks infrastructure
Considerations: Relatively newer platform with evolving feature set; premium pricing
SIEM Feature Comparison: Making the Right Choice
To help you evaluate these platforms, here’s a detailed comparison of their core capabilities:
| Feature | Splunk ES | Microsoft Sentinel | IBM QRadar | Elastic Security | Cortex XSIAM |
|---|---|---|---|---|---|
| Deployment Options | On-prem, Cloud, Hybrid | Cloud-native | On-prem, Cloud, Hybrid | On-prem, Cloud, Hybrid | Cloud-native |
| Pricing Model | Data volume | Data ingestion | Events/flows | Data volume/features | Subscription |
| AI/ML Capabilities | Advanced | Strong | Moderate | Moderate | Advanced |
| Compliance Templates | Extensive | Strong | Extensive | Moderate | Moderate |
| Ease of Deployment | Complex | Simple | Moderate | Moderate | Simple |
| Integration Ecosystem | Extensive | Strong (Microsoft) | Strong | Strong | Growing |
| Automated Response | Via SOAR | Built-in | Via QRadar SOAR | Via commercial features | Built-in |
| Learning Curve | Steep | Moderate | Moderate | Moderate | Moderate |
| Best For | Large enterprises | Microsoft shops | Compliance-focused | Technical teams | Automation-focused |
This comparison should serve as a starting point. Conducting a proof of concept with your actual data and use cases remains the best way to evaluate SIEM platforms for your specific needs.
Implementing SIEM: Best Practices for Success
Deploying a SIEM system requires careful planning and execution. Many organizations struggle with SIEM implementations because they underestimate the complexity or skip critical planning steps. Here’s how to set yourself up for success:
Define Clear Objectives and Use Cases
Start by identifying what you want to achieve with SIEM. Common use cases include threat detection, compliance reporting, incident investigation, and security monitoring. Prioritize these use cases based on business impact and regulatory requirements.
Document specific scenarios like detecting lateral movement, identifying data exfiltration, or monitoring privileged access. These scenarios guide your configuration and rule development.
Inventory Your Data Sources
Catalog all systems, applications, and devices that generate security-relevant logs. Prioritize data sources based on their security value. Critical systems like domain controllers, firewalls, and VPN gateways should be among your first integrations.
Remember that more data isn’t always better. Focus on high-value sources before expanding to every possible log generator. This approach prevents overwhelming your SIEM with noise.
Establish a Baseline and Tune Detection Rules
Generic detection rules generate excessive false positives. Invest time in understanding normal behavior in your environment before deploying aggressive detection rules. Machine learning models need training periods to establish accurate baselines.
Continuous tuning is essential. As your environment evolves, update your rules to reflect new applications, user behaviors, and threat patterns. Schedule regular reviews of alert accuracy and rule effectiveness.
Build a Skilled Security Operations Team
SIEM tools amplify human expertise but cannot replace it. Invest in training for your security analysts. They need to understand both the SIEM platform and the underlying security concepts.
Consider starting with a managed SIEM service if internal expertise is limited. Many organizations transition to in-house management as their teams develop skills.
Create Runbooks and Response Procedures
Standardize how your team responds to different alert types. Runbooks should outline investigation steps, escalation criteria, and response actions for common scenarios. This standardization improves consistency and reduces response times.
Document lessons learned from incidents to improve your runbooks over time. Your response procedures should evolve based on real-world experience.
Plan for Scale and Performance
SIEM systems must handle growing data volumes as your organization expands. Design your architecture with scalability in mind. Cloud-based solutions offer elastic scaling, while on-premises deployments require capacity planning.
Monitor SIEM performance metrics like data ingestion rates, query response times, and search latency. Performance degradation affects detection capabilities and user experience.
Integrating AI Agents with SIEM for Enhanced Security Operations
The security landscape in 2026 demands automation at scale. Human analysts cannot manually review the thousands of alerts that modern SIEM systems generate daily. This is where AI agents for cybersecurity transform security operations from reactive to proactive.
AI agents augment SIEM capabilities by automating time-consuming tasks, enriching alerts with contextual information, and executing response actions autonomously. When integrated effectively, these agents multiply the productivity of security teams.
Alert Triage and Prioritization: AI agents automatically analyze incoming SIEM alerts, gathering additional context from threat intelligence feeds, asset databases, and historical incident data. They score alerts based on actual risk, ensuring analysts focus on genuine threats rather than false positives.
Automated Investigation: When SIEM detects suspicious activity, AI agents can automatically query additional data sources, check for similar historical incidents, and compile comprehensive investigation reports. What once took 30 minutes of manual work happens in seconds.
Threat Hunting: Proactive threat hunting identifies compromises before they trigger alerts. AI agents continuously search through SIEM data for indicators of advanced persistent threats, using behavioral analytics and threat intelligence to uncover hidden threats.
Compliance Monitoring: AI agents monitor SIEM data for compliance violations, automatically generating reports and alerting stakeholders to potential issues. This continuous compliance monitoring reduces audit preparation time and identifies policy violations in real time.
Platforms like Hunto AI offer specialized agents that integrate directly with SIEM systems, including agents for vulnerability management, threat intelligence, and incident response. These purpose-built agents understand security workflows and execute tasks with minimal human oversight.
The combination of SIEM and AI agents creates a force multiplier effect. Organizations report reducing mean time to detect (MTTD) by up to 70% and mean time to respond (MTTR) by up to 80% when implementing AI-powered automation alongside traditional SIEM platforms.
Common SIEM Implementation Challenges and Solutions
Despite their value, SIEM implementations frequently encounter obstacles. Understanding these challenges helps you avoid common pitfalls:
Alert Fatigue
The Problem: SIEM systems can generate thousands of alerts daily. Many are false positives or low-severity events that don’t warrant immediate attention. Analysts become overwhelmed and may miss critical threats buried in noise.
The Solution: Implement aggressive tuning during the first 90 days. Use machine learning to establish behavioral baselines. Create tiered alert levels with automated handling for low-severity events. Consider AI-powered alert triage to filter false positives before they reach human analysts.
Data Quality Issues
The Problem: Inconsistent log formats, missing timestamps, and incomplete data reduce SIEM effectiveness. Garbage in means garbage out—poor data quality undermines correlation and detection capabilities.
The Solution: Standardize logging configurations across your infrastructure. Implement log normalization at collection points. Regularly audit data sources to ensure completeness and accuracy. Use SIEM parsing rules to handle format variations.
High Total Cost of Ownership
The Problem: SIEM deployments often exceed budget projections. Licensing costs based on data volume, storage requirements, and staffing needs accumulate quickly.
The Solution: Carefully plan data retention policies, storing only necessary data for active analysis while archiving older logs to cheaper storage. Evaluate cloud-native solutions with consumption-based pricing. Consider managed SIEM services to reduce staffing costs.
Skill Gaps
The Problem: Effective SIEM operation requires specialized skills in security analysis, the specific SIEM platform, and correlation rule development. Many organizations struggle to find and retain qualified personnel.
The Solution: Invest in training and certification programs for existing staff. Start with managed services while building internal capabilities. Leverage automation to handle routine tasks, allowing analysts to focus on complex investigations requiring human judgment.
Integration Complexity
The Problem: Modern IT environments include on-premises infrastructure, multiple cloud platforms, SaaS applications, and legacy systems. Integrating all these data sources into SIEM requires significant effort.
The Solution: Prioritize integrations based on security value. Use vendor-supported connectors where available. Implement a log aggregation layer to simplify SIEM integration. Consider SIEM platforms with extensive integration libraries.
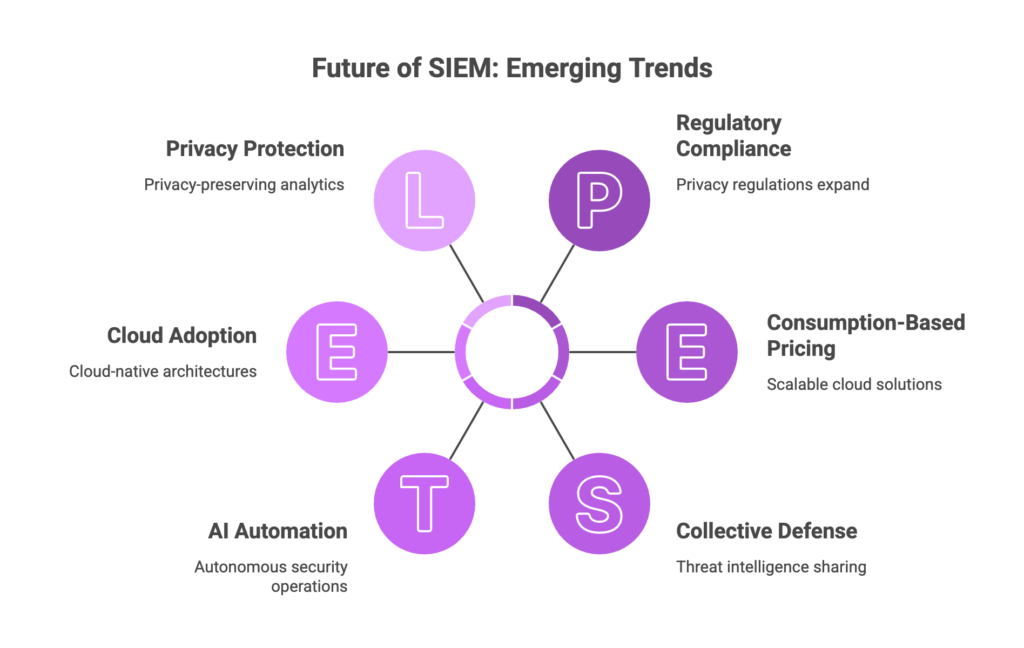
The Future of SIEM: Emerging Trends for 2026 and Beyond
SIEM technology continues evolving rapidly. Several trends are reshaping how organizations approach security information and event management:
XDR Integration
Extended Detection and Response (XDR) platforms are merging with traditional SIEM capabilities. This convergence provides unified visibility across endpoints, networks, cloud environments, and applications. The line between SIEM and XDR continues to blur as vendors add cross-domain correlation and automated response.
Autonomous Security Operations
AI and machine learning are moving beyond assisting analysts to operating autonomously. Future SIEM platforms will detect, investigate, and respond to threats with minimal human intervention. Analysts will focus on threat hunting, strategic planning, and handling novel attack scenarios that require human creativity.
Cloud-Native Architectures
On-premises SIEM deployments are giving way to cloud-native solutions that offer unlimited scalability, consumption-based pricing, and reduced maintenance overhead. Hybrid approaches supporting both cloud and on-premises data sources are becoming the standard.
Privacy-Preserving Analytics
Regulations like GDPR create challenges for SIEM systems that collect and analyze user activity data. New techniques including differential privacy and federated learning enable security analytics while protecting user privacy. These approaches will become essential as privacy regulations expand globally.
Threat Intelligence Sharing
Automated threat intelligence sharing between organizations, industries, and security vendors will enhance collective defense. SIEM platforms will participate in threat intelligence networks, contributing anonymized attack data and benefiting from insights across the security community.
Organizations that stay ahead of these trends will maintain competitive advantages in security effectiveness and operational efficiency.
Conclusion
SIEM systems have evolved from compliance-focused log collectors into sophisticated security platforms essential for modern cybersecurity programs. The combination of real-time correlation, behavioral analytics, threat intelligence, and automated response creates a powerful defense against today’s advanced threats.
Selecting the right SIEM platform requires careful evaluation of your organization’s specific needs, technical environment, and operational capabilities. Whether you choose Splunk, Microsoft Sentinel, IBM QRadar, Elastic Security, or Cortex XSIAM, success depends more on effective implementation and operation than on feature checklists.
The integration of AI agents with SIEM platforms represents the next frontier in security operations. By automating routine tasks and augmenting human expertise, these technologies enable security teams to operate at the speed and scale that modern threats demand.
As you evaluate SIEM solutions for your organization, focus on platforms that not only meet your current requirements but can also adapt to evolving threats and growing infrastructure. The best SIEM investment is one that protects your organization today while positioning you for tomorrow’s security challenges.
Ready to enhance your security operations with AI-powered automation? Explore how Hunto AI can transform your SIEM deployment into an autonomous security operations center.
Frequently Asked Questions About SIEM
What is the difference between SIEM and SOAR?
SIEM (Security Information and Event Management) focuses on collecting, analyzing, and correlating security data to detect threats. SOAR (Security Orchestration, Automation, and Response) emphasizes automating response workflows and orchestrating security tools. While SIEM identifies what is happening, SOAR automates what to do about it. Modern security operations centers use both technologies together, with SIEM providing detection and SOAR enabling automated response. Many vendors now offer integrated SIEM-SOAR platforms that combine both capabilities in a single solution.
How much does a SIEM system cost?
SIEM costs vary dramatically based on data volume, deployment model, and feature requirements. Small organizations might spend $10,000 to $50,000 annually for cloud-based SIEM covering basic needs. Mid-sized enterprises typically invest $100,000 to $500,000 per year including licensing, storage, and staffing. Large enterprises with complex environments can spend millions annually on comprehensive SIEM deployments. Cloud-native solutions with consumption-based pricing offer more predictable costs and lower upfront investment compared to traditional on-premises deployments. Remember to factor in personnel costs, training, and ongoing tuning when calculating total cost of ownership.
Can small businesses benefit from SIEM?
Absolutely. While enterprise SIEM platforms can be overwhelming and expensive for small businesses, several vendors offer right-sized solutions specifically designed for organizations with limited security staff and budgets. Cloud-based SIEM services with consumption-based pricing make the technology accessible to businesses of all sizes. Small businesses facing compliance requirements like PCI-DSS or HIPAA often find SIEM essential for meeting regulatory obligations. Managed SIEM services also provide small organizations with enterprise-grade security monitoring without requiring in-house expertise. The key is choosing a solution that matches your scale and complexity rather than implementing an enterprise platform designed for Fortune 500 companies.
How long does SIEM implementation take?
SIEM implementation timelines range from a few weeks to several months depending on environment complexity, data source diversity, and organizational readiness. A basic cloud SIEM deployment with limited data sources might become operational in 2 to 4 weeks. Comprehensive enterprise deployments typically require 3 to 6 months for initial implementation, followed by ongoing optimization. Key factors affecting timeline include data source integration, correlation rule development, team training, and use case definition. Organizations with clear objectives, documented data sources, and dedicated resources complete implementations faster than those approaching SIEM reactively. Remember that SIEM optimization continues long after initial deployment as you refine rules and expand coverage.
What skills do SIEM analysts need?
Effective SIEM analysts combine technical skills with security knowledge and analytical thinking. Core competencies include understanding network protocols, operating systems, and common attack techniques. Familiarity with the specific SIEM platform is essential, including query languages like Splunk SPL or Microsoft KQL. Analysts need strong pattern recognition abilities to identify anomalies in vast datasets. Knowledge of compliance frameworks relevant to your industry helps with reporting and audit support. Soft skills like communication and documentation are equally important since analysts must explain findings to both technical and business stakeholders. Many organizations look for candidates with certifications like GIAC SIEM (GSEC) or vendor-specific credentials. Platforms like Hunto AI can augment analyst capabilities by automating routine tasks and providing decision support, allowing less experienced analysts to handle complex investigations effectively.
