AI-Powered Brand Impersonation Detection
24/7 Monitoring. Instant Detection. Automated Takedowns.
1M+ daily threats monitored, 99% brand safety coverage, 30min takedown, 100% AI automation Advanced AI brand monitoring with social media impersonation detection and mobile app monitoring across 180+ channels. Our platform provides 24/7 monitoring of brand reputation risks, from phishing sites to fake accounts, eliminating threats before they damage your business.
AI-Powered Social Media & Mobile App Impersonation Detection
24/7 monitoring of brand reputation risks with automated impersonation discovery
Automated Monitoring & Response Workflow
AI-powered detection and elimination in four stages
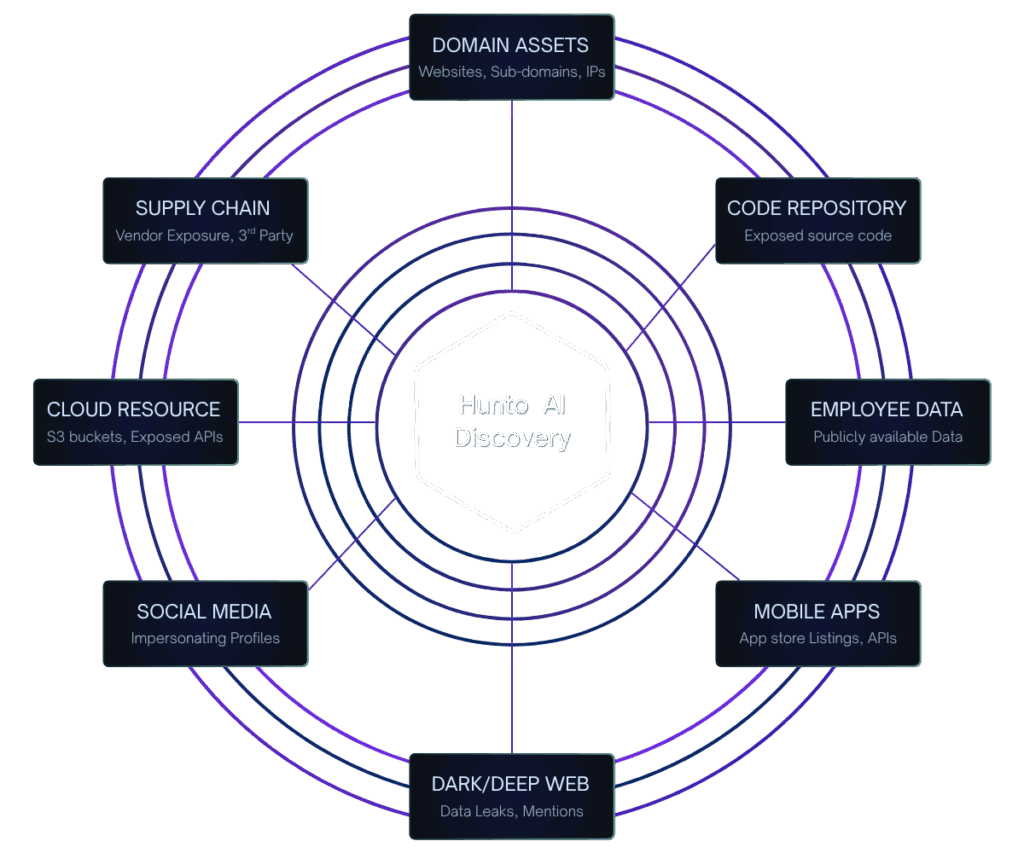
AI-Powered Discovery of Brand Threats
Continuous brand impersonation detection across all channels
Security teams need comprehensive brand impersonation discovery to identify threats across social media, mobile apps, domains, and marketplaces. Our AI-powered platform continuously monitors 180+ channels for fake accounts, rogue apps, typosquatting domains, and unauthorized brand usage—ensuring complete brand safety coverage.
Social Media & Mobile App Impersonation Detection
Real-time AI detection across all platforms
Advanced AI-powered social media impersonation detection monitors Facebook, Instagram, LinkedIn, Twitter/X, and TikTok for fake profiles. Mobile app impersonation detection scans iOS and Android app stores for rogue apps. Our 24/7 monitoring of brand reputation risks uses behavioral analytics to identify sophisticated attacks that evade traditional tools.
DMARC Policy Enforcement
99.9% email spoofing prevention
Findings from Brand Defense on confirmed domain spoofing provide the final proof of malicious intent needed to trigger DMARC+ policy enforcement. Move from monitor to reject safely with full validation. Achieve near-perfect email authentication and prevent unauthorized emails from reaching your customers.

Automated Brand Impersonation Defense
30-minute impersonation takedown response
AI-driven impersonation takedowns remove phishing sites, fake social media profiles, and rogue mobile apps within minutes. Our brand impersonation defense platform automates evidence collection, legal template generation, and platform coordination for rapid response. Integration with brand safety monitoring tools ensures continuous protection.
Complete Brand Impersonation Defense
Our AI brand monitoring platform serves as your primary brand impersonation detection system. By integrating real-time findings with Threat Intelligence and Attack Surface Management, we deliver proactive brand impersonation defense—not just reactive takedowns.
Seamless Integration Across Security Stack
Brand Monitoring enriches Threat Intelligence, ASM, and DMARC+ for complete protection
Problem
Brand Defense findings on phishing sites and fraudulent campaigns often exist in isolation, preventing comprehensive threat actor profiling and infrastructure mapping. Without linking this data to broader threat intelligence, organizations miss opportunities to disrupt entire attack campaigns and attribute threats to specific actors.
Solution
Data from Brand Defense on confirmed phishing sites and fraudulent campaigns is immediately analyzed by the Threat Intelligence platform. This process extracts attacker TTPs (Tactics, Techniques, and Procedures) and infrastructure details, enriching the global threat profile for all Hunto AI clients. Shared threat actor indicators enable proactive blocking before attacks reach your brand.
- Automatic threat actor attribution from brand abuse incidents
- Infrastructure mapping reveals entire attack campaigns
- Shared intelligence protects all Hunto AI clients
- Proactive blocking of known threat actors before they strike
- TTPs extracted from phishing sites inform defensive strategies
- Global threat profile enrichment from real-world brand attacks

Proven Monitoring Results
Real-time threat detection and elimination delivering measurable ROI
99.9% Email Spoofing Prevention
Achieve near-perfect email authentication with DMARC policy enforcement.
10+ Digital Asset Categories Covered
Gain comprehensive visibility across websites, social media, app stores, domains, forums, and the deep/dark web.
30 Min Threat Remediation Window
Experience rapid, AI-driven takedown of phishing sites, fake apps, and impersonating accounts, minimizing damage within minutes.
1M+ Threats Analyzed Daily
Leverage continuous monitoring and AI insights from over a million threats and brand mentions across the digital landscape.
100% Automation in Detection
Benefit from fully automated, AI-powered detection of phishing, impersonation, and brand abuse.
Prevent Financial & Reputational Loss
Proactively identify and dismantle fraudulent schemes, directly safeguarding customer assets and preserving invaluable brand equity.
Industry-Leading Brand Monitoring
Comprehensive asset coverage, AI-driven detection, and automated remediation that outperforms traditional brand protection platforms.
10+ Category Coverage
Achieve unparalleled brand monitoring scope across social media, marketplaces, app stores, forums, domains, and the deep/dark web.
- Social media platforms and emerging channels
- App stores (iOS, Android, third-party)
- Domains, subdomains, and dark web marketplaces
Seamless SIEM/SOC Integration
Connect effortlessly with existing SIEM, ticketing, and cloud platforms for streamlined workflows.
- Native integrations with major SIEM platforms
- Automated ticketing and incident response
- Unified orchestration for security operations
AI-Driven Impersonation Detection
Leverage behavioral analytics to identify and mitigate sophisticated phishing campaigns and fake profiles.
- Behavioral pattern recognition beyond signatures
- Advanced ML for deepfake and synthetic media detection
- Automated threat actor attribution and profiling
Frequently asked questions
AI-powered brand impersonation detection uses machine learning and behavioral analytics to identify fake social media profiles, rogue mobile apps, phishing sites, and unauthorized brand usage across 180+ channels. Our platform provides 24/7 monitoring of brand reputation risks with automated impersonation discovery and takedowns. We monitor social media platforms, app stores, domains, marketplaces, and the dark web to detect brand impersonation, deepfakes, and fraud in real-time.
Our AI-powered social media impersonation detection uses multi-modal AI analyzing text, images, video, and audio across Facebook, Instagram, Twitter/X, LinkedIn, and TikTok. Computer vision algorithms identify visual brand similarity (logos, executive photos). Natural language processing confirms context and intent. Behavioral analysis tracks threat actor patterns to detect sophisticated impersonation that evades traditional monitoring tools.
Mobile app impersonation detection monitors Apple App Store, Google Play, and third-party app stores for rogue apps using your brand name, logo, or screenshots. Our brand safety monitoring tools scan daily, analyzing app names, descriptions, permissions, and developer history to identify malicious clones distributing malware or stealing customer data. Average takedown time is 24-48 hours.
When brand impersonation is detected, our platform generates legal evidence packages with screenshots, metadata, and timestamps. Impersonation takedown requests automatically submit to platforms (Google, Meta, Apple, domain registrars) through 90+ integrations. Our brand impersonation defense system coordinates with platform abuse teams for rapid removal, averaging 24-72 hours with a 98% success rate.
Yes. Our AI brand monitoring platform provides continuous 24/7 monitoring of brand reputation risks across social media, app stores, domains, marketplaces, forums, and the dark web. We analyze 1M+ threats daily, providing real-time alerts for critical brand impersonation incidents. The platform includes brand safety monitoring tools for compliance reporting and audit trails required by SOC 2, ISO 27001, and cyber insurance.
Explore more modules

Ready to Safeguard Your Organization Digital Presence?
See how Hunto AI protects your brand reputation, customer trust, and digital assets. Get a personalized demo today.