Block Email Spoofing & Phishing
Without Breaking Legitimate Mail
Stop attackers from impersonating your domain while maintaining 100% email deliverability Deploy enterprise-grade DMARC, SPF, and DKIM protection in 4-6 weeks. AI agents handle the complexity—you get the security.
Why teams choose DMARC+
Enterprise protection without enterprise complexity or risk.
Stop domain impersonation
Block phishing and BEC attacks that fake your brand in under 6 weeks.
95% faster than manual
AI handles report parsing, sender classification, and DNS recommendations automatically.
Zero email disruption
Phased rollout identifies and fixes issues before enforcement begins.
Audit-ready reporting
Continuous monitoring and documentation for SOC 2, ISO 27001, and cyber insurance.
Complete sender mapping
Discover every marketing tool, CRM, and service sending on your behalf.
How DMARC+ Works
Three layers of AI-powered protection that adapt to your infrastructure
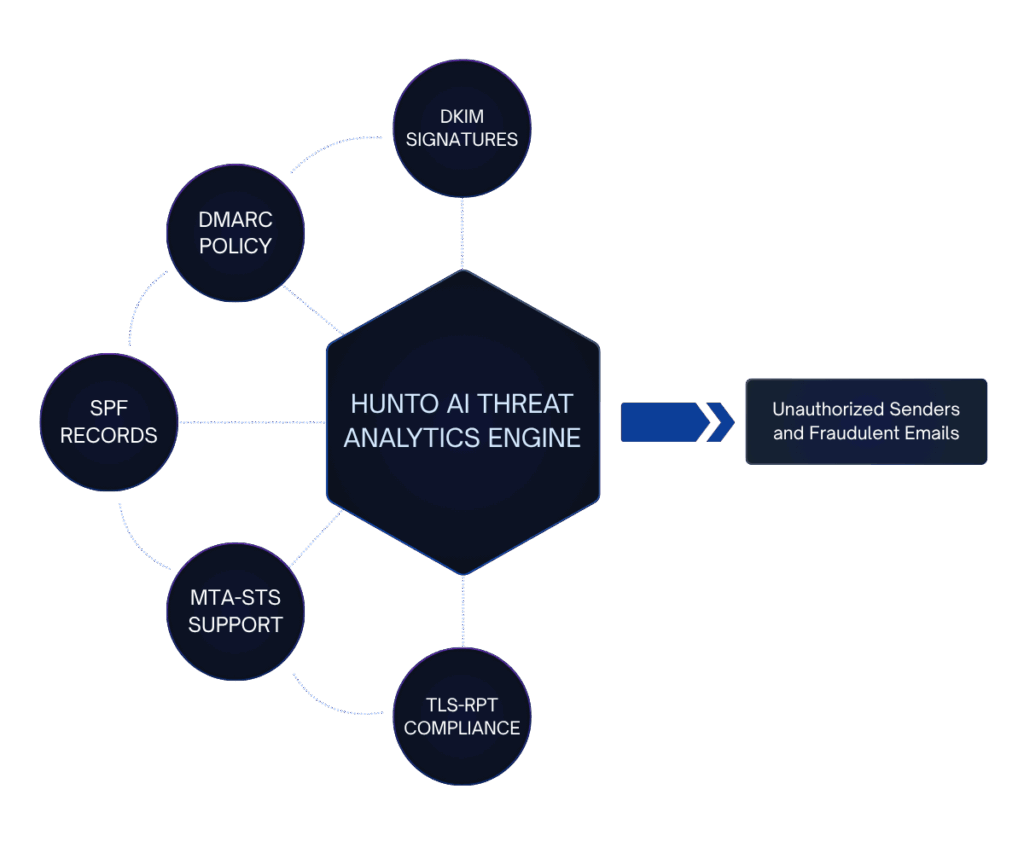
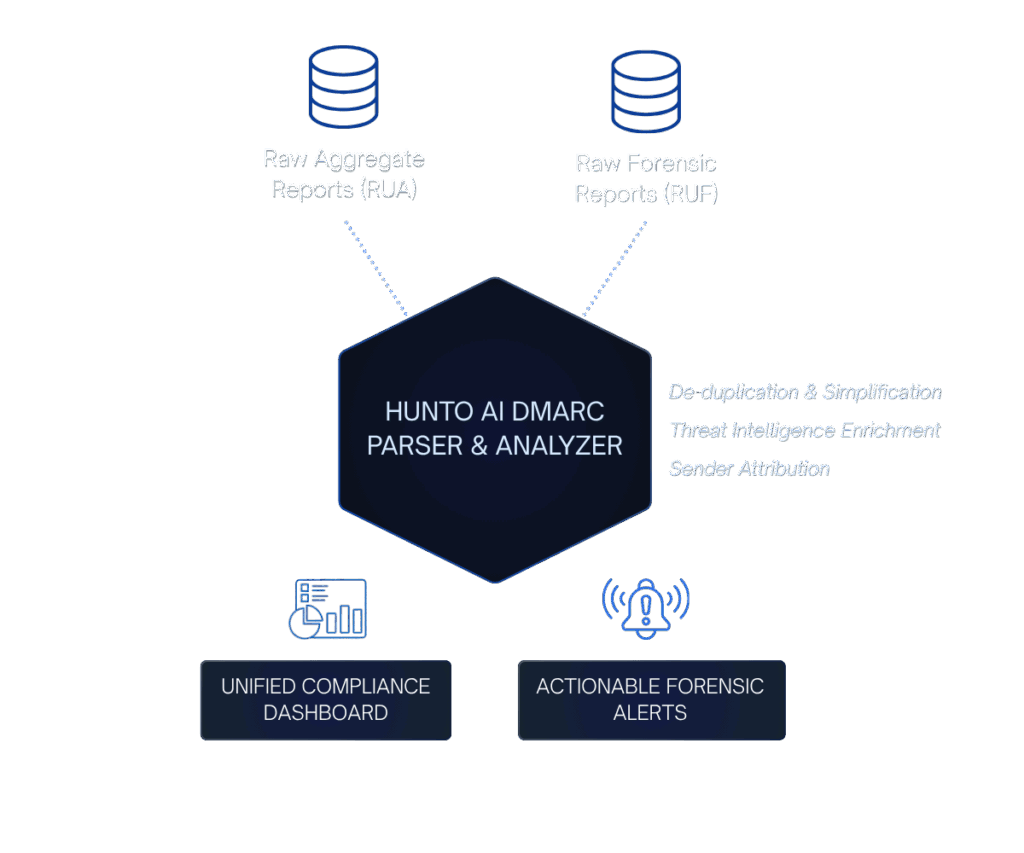
Automated Intelligence from Raw DMARC Data
Turn 10,000+ daily XML reports into actionable security decisions
AI agents ingest aggregate reports from Gmail, Outlook, and hundreds of receivers worldwide. Every IP, service, and authentication failure is classified using threat intelligence. You see a clean dashboard—not XML files. Identify unauthorized senders, track policy compliance, and catch authentication drift in real-time.
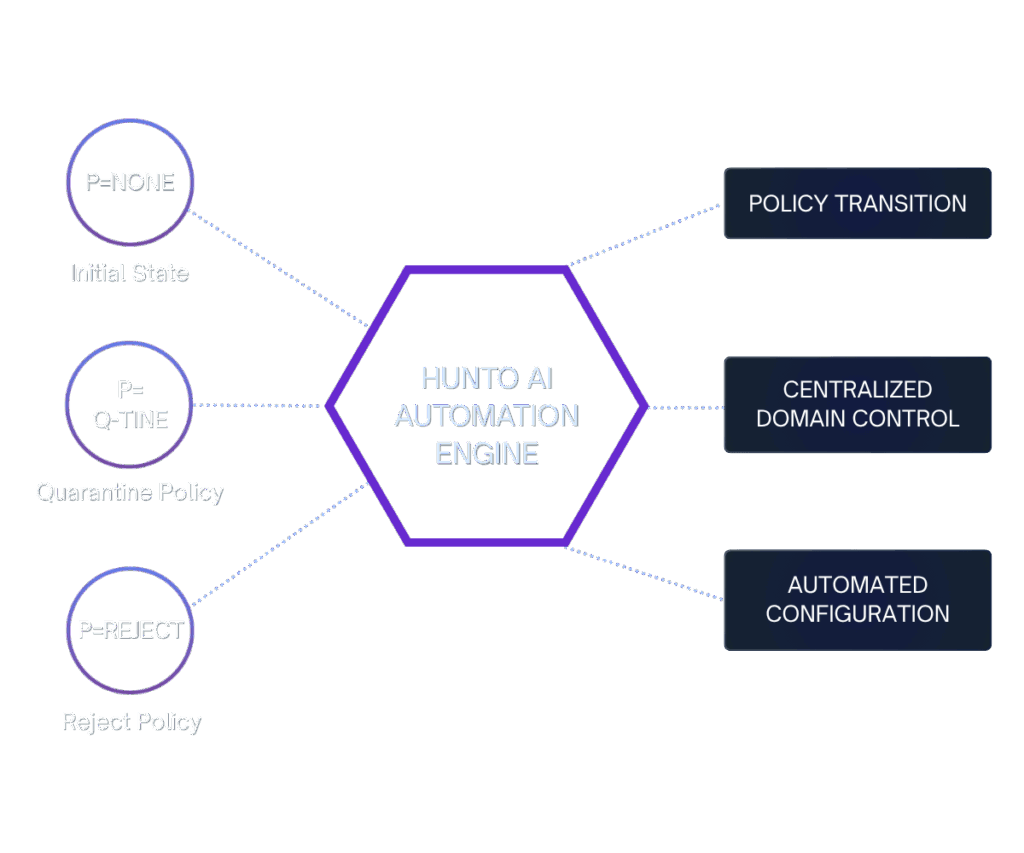
Phased Rollout to p=reject
Enforce protection without breaking business-critical email
Our AI guides you from monitoring (p=none) through soft enforcement (p=quarantine) to full protection (p=reject). Get real-time alerts when legitimate sources fail authentication—with copy-paste DNS fixes to resolve issues before they impact delivery. This isn't theory: our customers reach p=reject with <1% false positive rate.
Continuous Monitoring & Threat Detection
Catch policy drift and new threats before they become incidents
Email infrastructure changes constantly. New marketing tools get added, IPs rotate, vendors change authentication. Our continuous monitoring detects authentication failures, configuration drift, and unauthorized senders in under 5 minutes. Get alerts with context and recommended fixes—not just raw data dumps.
Your Path to Full Protection
Low-risk, phased deployment guided by AI agents. From monitoring to enforcement in 4-6 weeks.
- 1
Discovery & Setup
Deploy p=none monitoring policy in minutes. AI begins ingesting aggregate reports from Gmail, Outlook, Yahoo, and other receivers to map your complete sending infrastructure.
- 2
Sender Intelligence
AI classifies every IP and service sending on your behalf—marketing platforms, CRMs, HR tools, payment processors. Flag authentication gaps and unauthorized sources automatically.
- 3
Authentication Fixes
Get actionable DNS recommendations to align SPF and DKIM for legitimate senders. Copy-paste fixes resolve 95% of issues in days. Verify all authorized mail passes before enforcement.
- 4
Soft Enforcement
Upgrade to p=quarantine policy. Suspicious mail gets filtered to spam while monitoring continues. Fine-tune remaining edge cases with real-time feedback and alerts.
- 5
Full Protection
Activate p=reject to block all spoofed email at the receiver level. Continuous monitoring catches new senders, policy changes, and drift. Export compliance reports on-demand.
Built for every stakeholder
Security, IT, and compliance all benefit from one unified program.
Security Teams
Stop BEC and phishing attacks that bypass perimeter defenses.
- Block domain impersonation at the source—before emails reach inboxes
- Get measurable ROI: reduce phishing incidents by 95%+
- Prove security posture with real-time enforcement metrics
IT & Email Admins
Deploy DMARC enforcement without breaking critical business email.
- AI identifies every legitimate sender—no manual spreadsheets
- Get copy-paste DNS fixes when authentication breaks
- Phase to p=reject with zero false positives or delivery issues
Compliance & GRC
Meet audit requirements with continuous monitoring and documentation.
- Satisfy SOC 2, ISO 27001, and cyber insurance questionnaires
- Export audit-ready reports on policy enforcement and coverage
- Track policy drift and control effectiveness over time
Frequently asked questions
DMARC+ is an end-to-end platform that handles everything from initial setup through continuous monitoring. While basic DMARC requires manual report analysis and DNS management, our AI agents automate sender classification, provide copy-paste DNS fixes, and alert you to drift or threats in real-time. You get to p=reject 10x faster with zero email disruption.
No. Our phased rollout identifies every legitimate sender before enforcement begins. You'll get alerts and DNS fixes for any authentication issues. Our customers reach p=reject with <1% false positive rate because we validate every source during the monitoring phase.
Most organizations reach p=reject in 4-6 weeks. Simple email infrastructures can move faster; complex setups with many third-party senders may take slightly longer. Our AI accelerates every phase—report analysis, sender classification, and DNS fixes—so you're not waiting months for manual work.
No. The platform is designed for security and IT teams without deep email authentication knowledge. You'll get guided setup, plain-English explanations, and copy-paste DNS updates. Most configuration happens through the dashboard—no CLI or scripting required.
DMARC+ helps satisfy email authentication requirements in SOC 2, ISO 27001, NIST CSF, and cyber insurance questionnaires. You can export audit-ready reports showing policy enforcement, monitoring coverage, and incident response. Many customers use DMARC+ to demonstrate continuous controls during audits.
Explore more modules

Ready to Stop Email Impersonation?
See how DMARC+ blocks phishing and BEC attacks without disrupting your email flow. Get a personalized demo.