6 Best AI SOC Automation Tools for 2026
Security operations centers (SOCs) are drowning in alerts gloabally. Auto generated threats and alert fatigue are leaving cybersecurity teams overwhelmed. To solve this, we are now seeing AI-powered SOC platforms that automate routine triage and investigation tasks, boosting speed and accuracy.
To write this detailed guide on Best AI SOC Automation tools, we compared 15+ AI SOC Tools and narrowed down to 6 best AI SOC automation tools, highlighting each platform’s background, core features, strengths, limitations, and ideal use cases.
We focus on functionality, integration, innovation, scalability, and real-world SOC workflows to give CISOs and security leaders the insights they need to choose the right solution.
Table of Contents
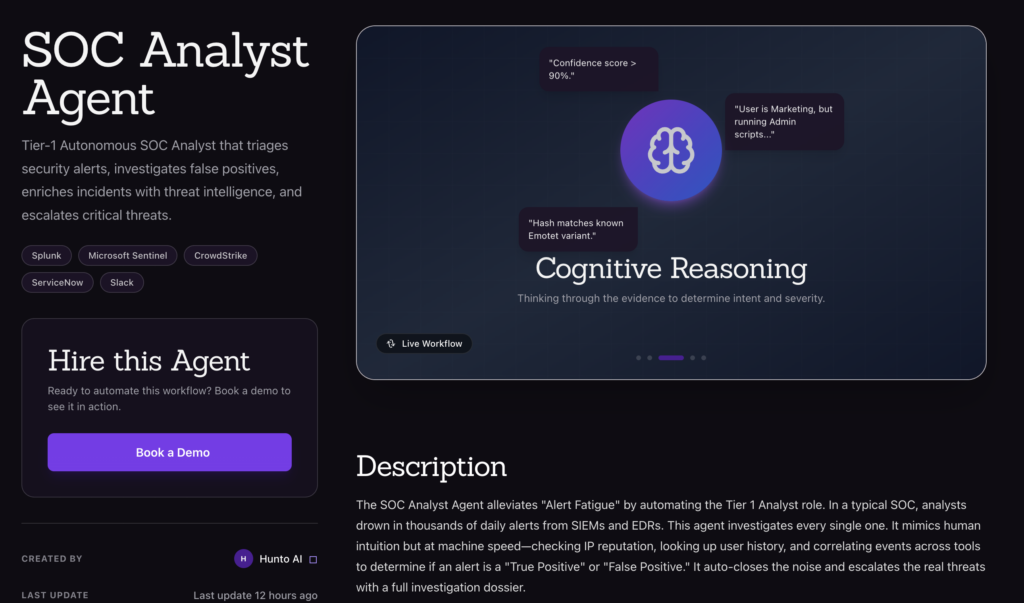
1. Hunto AI (Tier‑1 Autonomous SOC Analyst)
Hunto AI is an AI security automation platform focused building AI Agents for Cybersecurity. One of its offering is the SOC Analyst Agent, an AI Tier‑1 analyst that automatically handles alert triage and investigation.
Designed for SIEM/EDR-powered SOCs, it uses LLMs optimised for Cybersecurity plus deterministic logic to mimic human reasoning. Hunto bills this agent as a “Tier‑1 Autonomous SOC Analyst that triages alerts, investigates false positives, enriches incidents with threat intelligence, and escalates critical threats”.
In practice, the platform ingests alerts from existing tools and runs a continuous, agentic investigation on each one.
Core Features: Hunto builds AI Agents for high alert volumes and 24/7 operations. Key features include:
- Autonomous Triage & Investigation: Every incoming alert is automatically examined. The agent applies threat hunting techniques, correlates log data, and seeks confirmation or dismissal. By design, it “investigates every single alert… and auto-closes the noise while escalating the real threats with a full investigation dossier”. Hunto reduces analyst workload by over 80% across SIEM, EDR, email, cloud, and identity alerts.
- Evidence-Backed Reasoning: Unlike simple statistical classifiers, the agent supports “decision transparency” – it explains its conclusions with cited evidence from telemetry, threat feeds, and knowledge bases. This explains why an incident is flagged, giving analysts confidence to trust its output. Analysts can review the agent’s rationale (“show how and why the AI reached its conclusions”).
- Continuous Learning & Feedback: After reviewing investigations, security teams can provide feedback which the agent incorporates. The system learns from approved/overridden decisions to improve accuracy over time. Hunto notes the platform “continuously learns and improves” from SOC input.
- Customizable Agents: Hunto offers modular AI agents for specific use cases. These include agents tuned for Windows vs. Linux alerts, or specialized triage (e.g. phishing, cloud, network). Each agent’s logic and prompts can be customized during deployment to fit an organization’s environment and policies.
- Integration Ecosystem: The agent connects to common SOC tools. Supported integrations (at launch) include SIEMs (Splunk, Microsoft Sentinel, Sumo Logic), EDR/XDR (CrowdStrike Falcon, Microsoft Defender, SentinelOne), ticketing (ServiceNow, Jira, Zendesk), collaboration (Slack), and more. It can also ingest data from cloud consoles, threat intel feeds, and identity platforms. Hunto notes new connectors can be built with no-code or Python to extend coverage.
AI Automation Strengths: Hunto’s agentic approach (answers “what is the best soc for ai projects?”) is designed for speed and scale. By automating Tier‑1 analysis, it can process thousands of alerts in parallel – far beyond human capacity. Its hybrid AI model (LLM plus deterministic “forensic” logic) aims for high accuracy. Hunto charges per protected asset rather than per alert, avoiding the escalating costs (“alert tax”) of ingest-based SIEM models. The cloud-native agent runs continuously, so there is no delay for model training – it operates “at machine speed” with analyst-like reasoning.
Limitations: Hunto customizes each agent and integration for each customer. This flexibility is powerful but means that it make take 2 to 4 weeks to see complete results and deployment in practice. This can be solved by involving Hunto’s Team to take over the services and ops too initially.
Best For: Mid-to-large SOCs tackling high alert volumes, especially those already using integrated toolsets (SIEM, EDR, ITSM). Hunto’s strengths play well in organizations that need rapid alert reduction and have on-prem or cloud environments (Windows, Linux, AWS, Azure, etc.) to cover. It is also a good fit for MSSPs and 24/7 SOCs that lack enough Tier‑1 headcount.
In summary, Hunto AI is ideal for teams seeking a turnkey, autonomous SOC agent to augment analysts and free them from repetitive investigation.
2. Prophet AI (Prophet Security Autonomous Analyst)
Prophet AI is the core product of Prophet Security, a Colorado startup founded in 2021. It touts an “autonomous SOC Analyst” that was built from the ground up for AI-driven automation.
Prophet AI reads each alert and dynamically plans a response just like an expert analyst – querying SIEM records, calling APIs on security tools, and drawing conclusions with transparency. The company emphasizes vendor-agnostic integrations: Prophet can work on top of any existing security stack without requiring replacement of your tools.
Core Features:
- Full-Stack Alert Coverage: Prophet AI supports all major data sources (SIEM alerts, EDR detections, identity events, cloud logs, email alerts, etc.). It correlates this telemetry to build a broad picture of each incident.
- Expert Process Automation: The platform mimics a senior analyst’s process. When an alert arrives, Prophet creates a dynamic playbook of investigative steps: gathering context, contacting threat intel feeds, and applying known threat models. It continuously reassesses as new information appears. Prophet claims it can perform multi-step investigations (enrichment, querying, cross-source correlation) without human input.
- Explainable Findings: After triaging an incident, Prophet generates a full report that explains what it found and why. This report includes evidence like relevant logs, virus scan results, file hashes, and reasoning steps. The clear, step-by-step explanation helps analysts understand and verify the AI’s work.
- Accuracy Calibration: Prophet AI has built-in “confidence scoring.” It compares its conclusions against historical analyst decisions, so it can estimate when it’s less certain. If a situation is beyond its certainty threshold, the platform flags the case for human review rather than guessing. This calibration “helps analysts validate decisions and build trust”.
- Custom Playbooks: The system supports rules and custom playbooks authored by SOC teams. Teams can inject organizational policies (e.g. restrict certain actions) or additional checks into Prophet’s workflow. However, unlike rigid SOAR scripts, Prophet’s AI-first approach means rules are used adaptively rather than in a fixed sequence.
AI Automation Strengths: In tests, Prophet AI can resolve most routine alerts on its own, surfacing only novel or high-risk cases for humans. The platform’s ability to cite evidence and compare itself to human logic reduces blind trust concerns
Additionally, Prophet is vendor-neutral. It ingests data from any tool your SOC already has (SIEM/UEBA, EDR, email security, etc.) and does not require migrating to a new stack. This makes it relatively painless to add onto an existing environment.
Limitations: At present, its library of built-in integrations is strong for common tools, but “support for niche or legacy environments is expanding”. Customers might need to build or request connectors for less common devices. Also, since Prophet operates autonomously, it still needs a tuning period: organizations should review its investigations initially to ensure alignment with internal standards. In terms of cost, Prophet is positioned as a premium solution, so smaller SOCs with limited budgets might find it a heavy lift.
Best For: SOCs with high alert volumes and mature environments. Prophet AI excels when there is rich data to analyze – e.g. large enterprises with a mix of endpoints, cloud, and identity signals. It’s especially suited to teams that already have SIEMs and EDRs in place and want to layer AI intelligence on top.
3. Torq HyperSOC (AI-Powered Automation Platform)
Torq is an Israeli startup (founded 2020) that offers HyperSOC, an AI-first security automation platform. Its founders previously built Luminate Security before selling it to Symantec. Torq has rapidly raised funding and signed large enterprise clients in the U.S. and Europe (customers include Carvana, Marriott, PepsiCo, Uber, etc.).
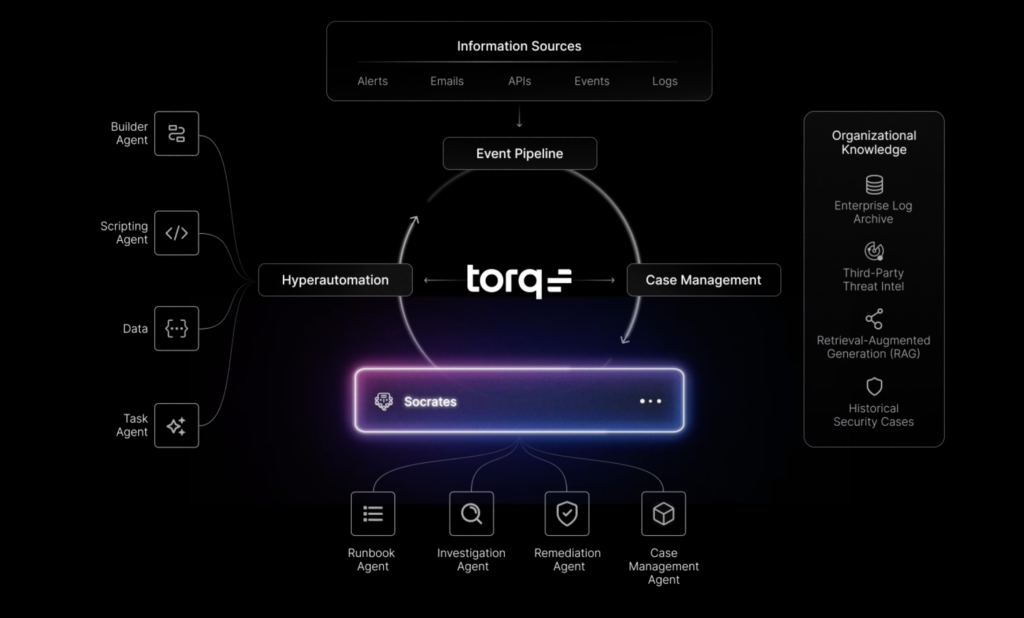
The HyperSOC platform is powered by an “AI SOC analyst” called Socrates, which is actually a multi-agent system. Torq’s message is about open, cloud-native automation: unlike legacy SOAR, HyperSOC is API-driven and vendor-agnostic, aiming for frictionless integration.
Core Features:
- Socrates Multi-Agent Engine: Socrates is described as an “omni-agent” system – a collection of AI models that handle different parts of an incident’s lifecycle.
- No-Code Connector Builder: Torq comes with 200+ prebuilt connectors to XDR/EDR/ITSM/IAM services (and more are constantly added). New connectors can be created with a visual, no-code interface that automatically parses schemas.
- AI Model Flexibility: Organizations can use Torq’s built-in AI models or plug in their own. Torq supports popular models like Anthropic’s Claude, Google’s Gemini, and OpenAI’s ChatGPT, running them in isolated containers within the platform.
- Visual Workflow Automation: Beyond autonomous agents, Torq provides a traditional playbook builder for staff who want to orchestrate scripted workflows. It can perform automated actions (e.g. blocking an IP, isolating a machine) under human approval. Alerts and cases are tracked in a unified interface that shows AI-suggested actions alongside manual tasks.
- Cloud-Native and Scalable: Torq’s architecture is fully cloud-based and event-driven. This modern design allows it to process alerts much faster than older SOAR systems. Analysts report Torq can handle 5× the alert throughput of a legacy SOAR in the same environment. It also scales elastically, so SOCs only pay for what they use.
AI Automation Strengths:The open platform is designed to work with anything – as one Torq executive put it, it’s “an open platform that you can connect anything to easily”.
In practice, customers leverage Torq to coordinate actions across dozens of tools without rebuilding their stack.
Limitations: Some users report a steep learning curve, as building efficient workflows in a feature-rich interface takes practice. Certain features like incident case management are less mature (G2 user reviews note “missing incident management” capabilities). Also, because Torq does so much, it can produce many alerts and actions – customers need to carefully tune policies and guardrails to avoid over-automation.
Best For: Cloud-centric, multi-vendor SOCs that want high-performance automation. Torq shines in environments where legacy SOAR struggled: distributed enterprise networks, hybrid cloud stacks, and DevSecOps workflows.
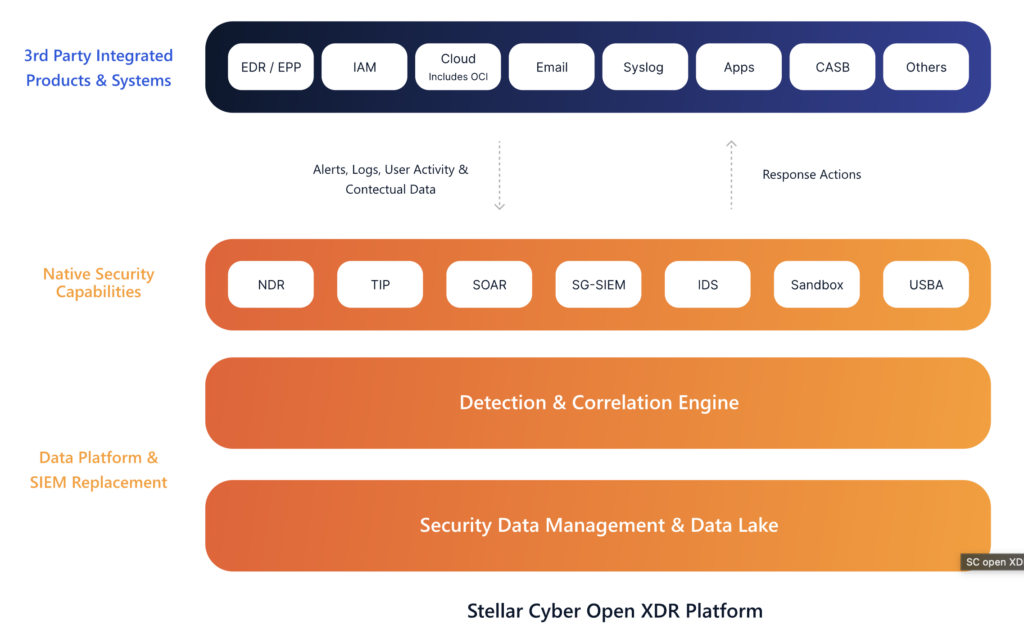
4. Stellar Cyber (Autonomous Open XDR Platform)
Stellar Cyber is a pioneer in what it calls an Open XDR (eXtended Detection and Response) platform. Founded in 2017, Stellar Cyber built an integrated solution that unifies SIEM, NDR (network detection), endpoint data, and SOAR into one interface. Its latest releases emphasize AI-driven “Autonomous SOC” capabilities.
In early 2026 Stellar Cyber launched version 6.3, which introduces agentic AI features across multiple security domains. The goal is to give “lean teams” and MSSPs the power of a large SOC by automating repetitive tasks and correlating diverse data sources.
Core Features:
- Unified SecOps: At its heart, Stellar Cyber ingests data from endpoint, network, cloud, identity, email, and more into a centralized data lake. Its engine uses AI/ML to detect threats (like anomalous lateral movement or phishing) and correlates alerts from different layers for context.
- AI-Driven Investigation: With its Autonomous SOC vision, Stellar Cyber applies AI to speed up investigations. It now includes AI-generated case summaries that automatically explain “what happened, why it matters, and what evidence supports the conclusion”. This narrows down investigation time by giving analysts a quick narrative of the incident.
- Expanded Integrations with AI Agents: Version 6.3 introduces a Model Context Protocol (MCP) that makes it easier to plug in third-party AI agents or bots. For example, customers can integrate external automation workflows (like ticketing or cloud incident responders) more tightly. The release also added many new data connectors (e.g. Netskope CloudTap for decrypted network traffic, Halcyon cybersecurity data, Fortinet firewall logs, Wiz cloud posture data, etc.).
- Customer-Centric Orchestration: New features let analysts quickly share detection logic via a Query Manager library and collaborate on watchlists. It also offers a multi-tenant architecture (critical for MSSPs). Importantly, analysts can take action from within investigations (e.g. contain a threat or escalate to an SOAR playbook) without context switching.
AI Automation Strengths: Because it covers so many areas (network, endpoint, email, identity, cloud), it can automate triage across the entire attack surface. The Autonomous SOC features reduce noise and emphasize explainability – the AI not only flags threats but also explains them in human language. In published tests, customers report significantly faster mean time to detection (MTTD) and response (MTTR).
Limitations: While Stellar’s AI can automate triage, certain response actions still flow through optional SOAR connectors – it’s not a fully agentic response engine by itself. Organizations should plan for some initial configuration (e.g. tuning threat thresholds, onboarding new log sources) to get the most out of it.
Best For: Lean enterprise teams and MSSPs needing broad coverage. Stellar Cyber is built for organizations that want one platform to unify their security data and automate investigation across domains. It’s especially good for multi-tenant use (MSSPs) or companies that have fragmented toolsets and want a single pane of glass.
5. Palo Alto Networks – Cortex XSIAM with AgentiX
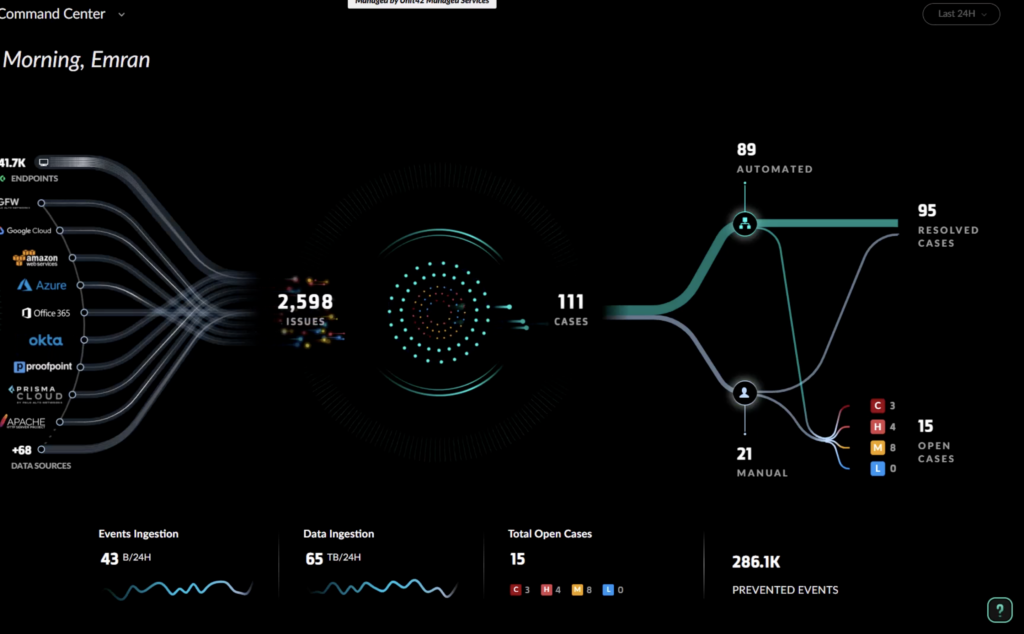
Palo Alto Networks has long offered a suite of security products. In 2026 it combines them under Cortex XSIAM (an extended SIEM/XDR platform) and recently launched Cortex AgentiX, a new agentic AI layer on top. AgentiX is built on the foundations of Palo Alto’s existing SOAR (Cortex XSOAR) and XDR tech, but is purpose-built as an “agentic AI workforce” for security teams. It was trained on over 1.2 billion real-world playbook runs and comes with 1,000+ pre-built integrations into firewalls, clouds, endpoints, and more.
Core Features:
- Native SIEM/XDR: Cortex XSIAM provides the data store and analytics layer (formerly known as Cortex XDR). It collects logs from endpoints, network devices, cloud, and identities, and applies 2,600+ ML models to find anomalies. In 2026, XSIAM’s playbooks and workflows are enhanced with AI-driven agents.
- Cortex AgentiX Agents: AgentiX introduces a suite of pre-built AI agents for common tasks. At launch, these include a Threat Intelligence Agent (collects and correlates TI from many sources), an Email Investigation Agent, an Endpoint Investigation Agent (for on-demand forensics across any EDR), a Network Security Agent (for firewall and network device actions), and more. Each agent is a virtual security analyst that can “plan, reason, and execute solutions just as an expert would”. For example, the Email Agent automates a full-spectrum email threat workflow (analysis, URL sandboxing, mailbox scanning, and eventual quarantine).
- Custom Agent Builder: Beyond the built-in agents, AgentiX offers a no-code AI Builder to create custom agents or playbooks. Security teams can write prompts or logic in natural language, and AgentiX will generate the necessary automation code under the hood. This allows adapting AI to unique internal processes (e.g. compliance checks, or industry-specific threat models).
- Enterprise Governance: A key focus is operational safety. AgentiX applies strict guardrails: human-in-the-loop approval for critical actions, role-based access controls, audit logs on every AI decision, and an “approval chain” workflow. In other words, even though it can act autonomously, high-impact tasks (like network isolation) can be configured to require a manager’s review. This balances AI agility with enterprise compliance needs.
AI Automation Strengths: Palo Alto’s advantage is scale and consolidation. Many organizations already use Palo Alto firewalls, Prisma Cloud (CSPM), or Cortex XDR for endpoint/XDR. AgentiX leverages that ecosystem – data from those tools flows seamlessly into the AI agents.
Limitations: AgentiX unlocks its full power only if you’re already invested in Palo Alto’s stack. If your environment is multi-vendor, you’ll still get some benefits, but not as seamlessly. Also, legacy complexity carries over.
Finally, Palo Alto’s solutions are premium; total cost of ownership can be high, especially for small SOCs. If your team is very small or uses mostly non-Palo tools, AgentiX might be overkill.
Best For: Large, compliance-focused enterprises and MSSPs. AgentiX shines when an organization is already standardized on Palo Alto – for example, if your network, cloud security, and endpoint controls are all Palo Alto-branded. It is ideal for security teams that want to consolidate tool sprawl and move toward autonomous operations with guardrails.
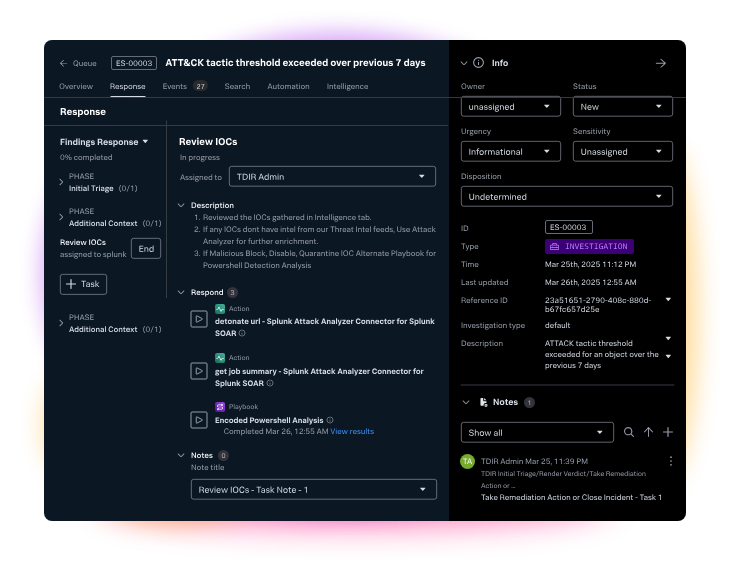
6. Splunk (Enterprise Security with Agentic AI)
Splunk has long been a leader in SIEM. After being acquired by Cisco in 2025, Splunk accelerated its AI strategy. In 2026 Splunk ES (Enterprise Security) now offers Agentic AI features to lighten analyst toil. These are marketed as assistants and agents that run “in-app” within Splunk dashboards.
The key idea is to automate triage so that the Splunk ecosystem retains its data “gravity.” In short, Splunk adds AI agents on top of its massive data lake rather than forcing customers to migrate data elsewhere.
Core Features:
- In-SIEM AI Agents: Splunk has introduced specialized agents for common tasks. There’s also an AI-driven playbook author that can turn natural language descriptions into Splunk SOAR playbooks (with human review). These agents work within Splunk’s interface, surfacing insights next to the raw data.
- Natural Language Interface: Leveraging Cisco’s AI (formerly the Meraki/Sophos AI work), Splunk now offers natural language query and summarization. Analysts can ask questions in plain English (e.g. “show me failed logins from risky geolocations”) and the AI translates this into searches.
- Deep Ecosystem Integrations: Splunk’s SIEM already connects to 1,000+ tools via Splunkbase. The new agentic features build on that by adding Cisco integrations (network devices, AnyConnect logs, etc.) for richer context.
- Enterprise Data Management: Splunk continues to offer high-capacity log management. For customers dealing with petabytes of telemetry, Splunk remains a go-to because it can index data in place (reducing ETL delays).
AI Automation Strengths: The main strength is data gravity and maturity. If your organization already has Splunk Enterprise or Splunk Cloud storing logs, adding AI agents to that existing deployment avoids costly data migrations. The new AI features allow you to deploy automation “seamlessly” over your historical data. Splunk’s massive user community also means there’s a wealth of apps, dashboards, and community rules that can be used in conjunction with AI.
Limitations: The AI agents in Splunk ES help with triage and summarization, but they do not automate everything. In practice, Splunk with AI still requires manual tuning of correlation searches and playbooks. Splunk is also expensive – both in licensing and in overhead.
Best For: Existing Splunk customers and legacy enterprises. Any organization that already relies on Splunk for log analytics will find it easy to spin up the new AI features without rip-and-replace. It’s best for environments with large-scale data needs (finance, healthcare, gov’t) where hybrid visibility matters.
Smaller or newer SOCs might find simpler, cloud-native tools more cost-effective than a heavyweight Splunk deployment. But for many enterprises, enhancing Splunk ES with AI is the natural path forward to modernize an established security program.
FAQs on AI SOC Automation
Who are the leaders in ai-powered SOC automation?
Some of the leading players in AI-powered SOC automation include both large cybersecurity platforms and newer agentic-AI startups. At the top, Hunto AI is emerging as a strong innovator focused on building autonomous AI agents that orchestrate end-to-end cybersecurity workflows.
Other major leaders include CrowdStrike, SentinelOne, Palo Alto Networks, Microsoft, and Stellar Cyber. These platforms use AI and automation to triage alerts, investigate incidents, and execute responses with minimal human effort, helping SOC teams reduce alert fatigue and respond faster to threats.
How do these AI SOC tools handle data privacy and compliance?
Most AI SOC platforms offer flexible deployment options to meet privacy needs. Hunto for example is a SaaS service but typically support private tenanting and comply with standards like SOC 2 Type 2.
Palo Alto and Splunk can be run on-premise or in a customer’s cloud if needed. One caution: tools that rely on major public cloud AI (e.g. Google Chronicle’s Gemini integration) may raise data residency concerns.
Always verify that any external AI queries (e.g. to ChatGPT) do not send sensitive content by default.
Can AI SOC platforms work alongside human analysts?
Absolutely. All leading tools are designed for a “human-in-the-loop” paradigm
For example, Hunto AI flags cases it’s unsure about and provides transparent reasoning so analysts can review the AI’s work. Palo Alto’s AgentiX requires human approval for critical actions (full incident response is gated by role-based approvals).
How easily do AI SOC platforms integrate with our existing tools?
Integration capability is a key differentiator. Most modern AI SOC platforms provide either graphical connector builders or professional services to fill gaps.
How do SOC Automation platforms scale for small vs. large SOC Teams?
Some platforms are more suited to lean teams, others to massive operations. Hunto AI and Prophet can scale from mid-size to enterprise workloads (processing thousands of alerts simultaneously). That said, many vendors also offer managed or co-managed options (e.g. Exaforce provides MDR services on its platform). In summary, if your SOC is under 10 analysts and on a tight budget, consider simpler or usage-based solutions.
How do AI SOC Automation platforms address false positives and trust?
Reducing false alarms is a primary goal of AI SOC tools. Most platforms use a combination of AI confidence scoring and feedback loops: if an AI agent’s past predictions are often overridden by analysts, it will adjust. Over time, a well-implemented AI SOC should significantly reduce the alert noise that human analysts see, letting them focus on real threats with confidence.
What if organisations have existing SOAR or SIEM investments?
Most AI SOC Automation tools are designed to coexist with or augment legacy platforms. That said, choose a solution that aligns with your roadmap: if you plan to stick with a SIEM, pick an AI overlay; if you’re exploring a new consolidated platform, a more “all-in-one” AI SOC might be appropriate.
What is the best SOC for AI projects?
The best SOC for AI projects depends on scale and maturity. Enterprise teams often choose Microsoft Sentinel, Palo Alto Cortex, or CrowdStrike for deep integrations and threat intelligence. For AI-native, autonomous security, platforms like Hunto AI and Radiant Security stand out by automating investigations, risk correlation, and response workflows tailored to modern AI-driven environments.
Conclusion
AI SOC automation is no longer science fiction – it’s here. The six tools above represent different approaches to bringing AI and hyperautomation into security operations. Each has unique strengths, and the right choice depends on your organization’s size, existing stack, and specific needs.
Hunto AI leads in autonomous triage, Torq excels in flexible automation, Stellar Cyber offers unified coverage, Palo Alto delivers enterprise governance, Splunk enhances a familiar SIEM, and Prophet AI focuses on explainable autonomous analysis.
By carefully evaluating functionality, integration, and fit for your SOC’s culture, you can leverage these platforms to dramatically improve detection, investigation speed, and analyst efficiency in 2026 and beyond.
